IoT devices generate vast amounts of data, but without encryption, this data is at risk. Whether it's a factory sensor or a smart building controller, unprotected data can be intercepted, altered, or stolen. Hybrid cloud systems - where data moves between on-premises infrastructure, private clouds, and public clouds - add complexity, creating more vulnerable points.
Here's what you need to know:
- Why encryption matters: Unencrypted IoT data can lead to security breaches, compliance issues (e.g., UK GDPR), and operational failures, such as tampered sensor readings causing equipment breakdowns.
- Hybrid cloud risks: Data travels through multiple layers (device-to-edge, edge-to-cloud, and cloud-to-cloud), requiring encryption at every step to prevent breaches.
- Encryption standards: Use TLS 1.2/1.3 for data in transit and AES-256 for stored data. Employ secure key storage methods like Trusted Platform Modules (TPM 2.0) to protect encryption keys.
- Compliance: UK regulations mandate encryption as a
technical measure
under GDPR and the Data (Use and Access) Act (effective June 2025). Failure to comply can result in fines and reputational harm.
Actionable Tips:
- Encrypt all IoT data during collection, transit, and storage.
- Use hardware-based security for key management.
- Automate processes like certificate rotation and compliance monitoring.
- Regularly update encryption protocols to align with current standards.
Encryption isn't optional - it's a necessity for protecting IoT data and maintaining compliance. Follow these practices to secure your systems effectively.
Encryption Standards and Best Practices for IoT Data
Core Encryption Protocols and Algorithms
When it comes to securing data in IoT systems, Transport Layer Security (TLS) 1.2 and 1.3 are the go-to standards. These protocols protect data as it travels between IoT devices, edge gateways, and cloud services [2][1]. For instance, all Azure services now default to TLS 1.2 on public HTTPS endpoints [2]. It’s crucial to disable outdated versions like TLS 1.0 and 1.1 to block downgrade attacks, where attackers force connections to use weaker encryption methods [2][1].
For data stored on devices or servers, Advanced Encryption Standard (AES) remains the preferred choice. AES-256 is especially recommended for sensitive information, thanks to its robust key length, making brute-force attacks virtually impossible [2][9].
To ensure data integrity and detect tampering, the SHA-2 family (including SHA-256, SHA-384, and SHA-512) is widely used for digital signatures and checksums [2]. Meanwhile, X.509 certificates serve as the standard for device identity and authentication, commonly used during TLS handshakes to establish secure connections [2][1]. For data actively processed in memory, hardware-based Trusted Execution Environments (TEEs) ensure confidentiality, keeping data encrypted even during processing [2][3].
For resource-constrained IoT devices, avoid overly complex encryption methods that could overwhelm their limited processing capabilities. Instead, choose encryption levels that strike a balance between security and performance.
These protocols form the backbone of IoT data security, enabling effective key management and ensuring compatibility across diverse systems.
Secure Key Management Practices
Strong encryption is only as secure as the keys that protect it. Effective key management is essential to safeguarding IoT data.
To ensure keys are secure, generate them using trusted sources of entropy, making it nearly impossible for attackers to predict them. Store encryption keys in secure hardware components like Trusted Platform Modules (TPM 2.0), Secure Elements (SE), or Hardware Security Modules (HSMs) to guard against physical theft [7]. As the UK's National Cyber Security Centre highlights:
Storing cryptographic roots of trust in a secure component, such as a TPM (trusted platform module, at least version 2.0)... can protect cryptographic secret keys from an attacker by ensuring they remain encrypted until required by an authorised entity[7].
Keep keys separate from the data they encrypt. Using a key hierarchy, such as a Key Encryption Key (KEK) to protect Data Encryption Keys (DEK), adds an extra layer of security. This ensures that even if the storage medium is compromised, the data remains inaccessible.
Regular key rotation is another vital practice. Automating this process limits the risk associated with any single key [2][11]. Once a key's lifespan ends, archive it securely and delete it when it’s no longer needed [9][1]. The Information Commissioner’s Office advises:
You should ensure the key size you choose is large enough to ensure that an attack on it is highly unlikely to succeed, taking into account that new attack methods may be discovered[9].
Maintain a comprehensive cryptographic inventory, documenting all tools, algorithms, and processes used across your IoT ecosystem. This makes it easier to review security measures and quickly adapt if vulnerabilities emerge [9]. Additionally, use logging tools to track every key-related action, including who accessed it, when, and for what purpose.
Ensuring Compatibility Across IoT Devices
Ensuring encryption works seamlessly across a diverse IoT environment is a critical challenge.
For older or limited devices, secure field gateways like Azure IoT Edge can handle encryption before transmitting data to the cloud [1][4]. This allows legacy hardware to remain part of the ecosystem without needing significant upgrades.
Using manufacturer-provided SDKs simplifies the process of implementing encryption and authentication. These SDKs typically include pre-configured security best practices and standard encryption libraries [1][4].
When transferring data between on-premises systems and the cloud, rely on Site-to-Site VPNs or dedicated high-speed links like ExpressRoute or Direct Connect. These connections, combined with encryption protocols such as MACsec, ensure secure data transit across hybrid environments [3][12]. For older devices that lack modern encryption capabilities, place them behind firewalls or use data diodes to enforce one-way data flow, protecting the broader network [4].
Automating the issuance and renewal of X.509 certificates helps reduce administrative workload and prevents disruptions caused by expired credentials [1]. Before deploying encryption, categorise your data - such as confidential or public - to apply the right level of protection. This avoids unnecessary performance costs for non-sensitive telemetry data [2][12].
Encryption in IT/OT/IoT Networks and How to Monitor Them
Implementing Encryption Across the IoT Data Lifecycle
::: @figure 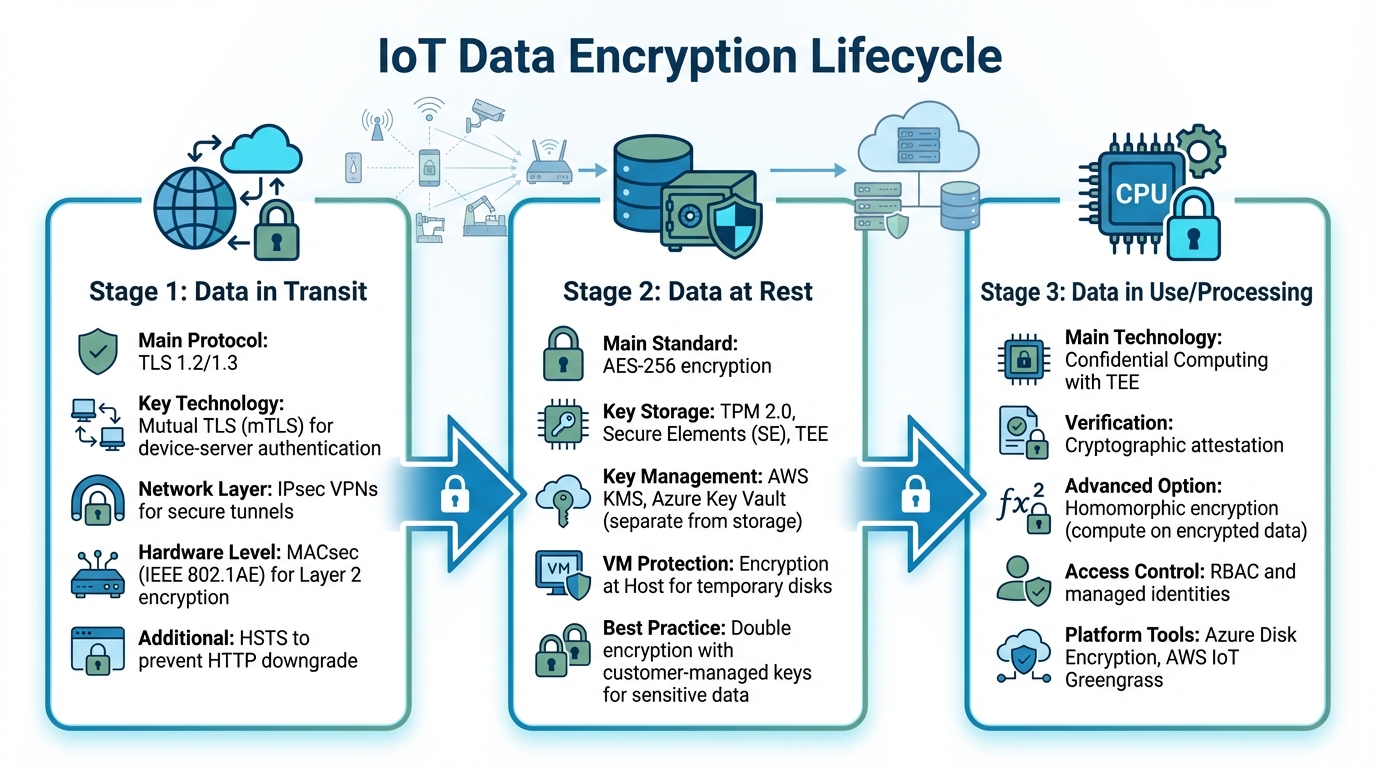 {IoT Data Encryption Lifecycle: Securing Data in Transit, at Rest, and During Processing}
:::
{IoT Data Encryption Lifecycle: Securing Data in Transit, at Rest, and During Processing}
:::
Securing Data in Transit
To safeguard communication between IoT devices and cloud endpoints, Transport Layer Security (TLS) 1.2 or 1.3 is essential. TLS 1.3, in particular, offers an edge by completing handshakes in just one round trip, cutting down on latency - a crucial factor for IoT operations [13]. For protocols like MQTT or HTTPS, Mutual TLS (mTLS) should be implemented to ensure both the device and server authenticate each other using digital certificates.
When connecting on-premises gateways to cloud virtual networks, IPsec VPNs can establish secure tunnels, encrypting data at the network layer. For private high-speed connections like Azure ExpressRoute or AWS Direct Connect, MACsec (IEEE 802.1AE) provides hardware-level encryption at Layer 2, protecting data as it moves across dedicated fibre circuits.
The UK's National Cyber Security Centre underscores the importance of protecting data in transit:
User data transiting networks should be adequately protected against tampering and eavesdropping[5].
Adding HTTP Strict Transport Security (HSTS) can further prevent connections from being downgraded to unencrypted HTTP. These precautions ensure data is secured before it even reaches storage, forming the foundation for robust protection when the data is at rest.
Encrypting Data at Rest
For stored data, AES-256 remains the go-to encryption standard, widely adopted across cloud databases, file systems, and on-premises storage solutions. Services like AWS S3 and EFS rely on AES-256 for their encryption needs. On IoT devices operating at the edge, encryption keys should be stored in hardware-protected modules, such as Secure Elements, Trusted Platform Modules (TPM 2.0), or Trusted Execution Environments (TEE), to prevent physical extraction.
To further secure cryptographic keys, they should be managed separately from the storage medium. Services like AWS Key Management Service (KMS) and Azure Key Vault are designed for this purpose, ensuring that a breach of the storage medium doesn't compromise the keys. For hybrid cloud setups running on virtual machines, enabling Encryption at Host
ensures that temporary disks and caches remain encrypted.
Minimising data storage can also reduce vulnerabilities. Retain only the sensor data critical for local operations and delete it when no longer needed. For highly sensitive data, applying two layers of encryption with different customer-managed keys adds an extra layer of security.
Maintaining Encryption During Data Processing
Encryption isn't just about storage and transit - it must also persist during active data processing. This is where Confidential Computing comes into play. By performing computations within hardware-based Trusted Execution Environments (TEE), data remains encrypted even as it is processed, isolating it from potential threats. Attestation - cryptographically proving that data is being processed securely within a TEE - helps meet stringent regulatory requirements.
Secure key release mechanisms are another critical measure. These ensure encryption keys are only provided to workloads that can prove, through cryptographic attestation, that they are executing inside a secure environment.
For advanced scenarios, homomorphic encryption offers the ability to perform computations on encrypted data without decrypting it. While this method is more computationally demanding, it provides a unique solution for specific use cases [14]. Leveraging platform-integrated encryption features, such as Azure Disk Encryption or AWS IoT Greengrass, can simplify implementation while benefiting from expert design and rigorous testing.
Finally, implementing Role-Based Access Control (RBAC) and managed identities ensures that only authorised users or systems can access encryption keys and processed data, maintaining security throughout analytics workflows.
Identity and Access Controls for Encrypted IoT Data
While strong encryption serves as the first line of defence, protecting IoT data in hybrid cloud environments also requires effective identity and access management. Together, these measures form a comprehensive security strategy for IoT systems operating within hybrid clouds.
Encryption alone isn’t enough to safeguard IoT data if unauthorised users or devices can still gain access. That’s where Identity and Access Management (IAM) comes in, acting as a crucial second layer of protection. IAM ensures that only verified devices and authenticated users can interact with encrypted data. Consider this: 80% of web application attacks exploit stolen credentials, and 40% of breaches involve compromised credentials [16]. For hybrid cloud IoT setups, robust identity controls are non-negotiable.
Device Identity and Authentication
Every IoT device in your network should have its own X.509 certificate and unique identifier, often referred to as a Thing Name.
This one device, one certificate
principle ensures that if a device is compromised, its credentials can be revoked without endangering the rest of the system [15]. To further secure these credentials, store private keys in a Trusted Platform Module (TPM) or Secure Element (SE), which prevents extraction and cloning [15][1].
For older, legacy devices, intermediary gateways can help maintain secure authentication [1]. Mutual TLS (mTLS) is particularly effective for verifying device identity, as it ensures both the device and the server authenticate each other using certificates [2][1]. The NSA and CISA highlight the risks of identity-based attacks:
Identity-based attacks, such as stolen credentials, phishing, and brute force attacks, represent a significant threat to organizations[16].
With device identities verified, the next step is to tightly define what each authenticated entity can access.
Role-Based Access Control (RBAC) in Hybrid Clouds
Once a device is authenticated, Role-Based Access Control (RBAC) determines its permissions. Following the principle of least privilege, devices should only be granted the minimum permissions necessary. For instance, a temperature sensor could be restricted to publishing updates to its assigned MQTT topic [15].
In hybrid cloud setups, adding an API layer - such as Amazon API Gateway - between users and the IoT data plane can reduce risks by preventing direct access to raw encrypted data streams. This extra layer minimises the attack surface [15]. For scenarios where on-premises systems need to interact with cloud-hosted data, temporary credentials (e.g., through tools like IAM Roles Anywhere) are a safer alternative to long-term access keys. These temporary credentials reduce the risk of exposure by limiting their validity period [17].
There’s also a growing shift towards Attribute-Based Access Control (ABAC), which makes authorisation decisions based on real-time factors like device security status, time of access, or location, rather than relying solely on static roles [16].
Multi-Factor Authentication (MFA) for IoT Ecosystems
Securing human access is just as important as device authentication. Multi-Factor Authentication (MFA) plays a key role here. With 20% of breaches linked to phishing [16], MFA helps protect against credential theft. The industry is moving towards phishing-resistant methods such as FIDO authenticators and PKI-based smartcards, moving away from SMS or push-based approaches [16].
Automating credential management is another critical step. Over-the-Air (OTA) updates can rotate device certificates before they expire, and Just-in-Time Provisioning (JITP) ensures new devices meet security standards as soon as they connect [15][1]. Regular audits using tools like IAM Access Analyzer can identify unused roles or overly permissive access, ensuring the system adheres to least-privilege principles [18]. As AWS IoT Lens explains:
The separation of identity and permissions provides flexibility in managing your device security[15].
Cost-Effective Encryption and Compliance Strategies
Let’s dive deeper into how you can secure IoT data while keeping costs in check and meeting compliance requirements. Striking the right balance between robust encryption, performance, and affordability is key - especially when considering UK GDPR standards, which call for appropriate
security measures that align with the state of the art
and the costs of implementation
[8].
Optimising Encryption for Performance and Costs
Not all IoT data is created equal. By classifying data into categories like highly confidential, confidential, or public, you can avoid wasting resources encrypting non-sensitive information. For instance, encrypting a warehouse temperature reading doesn’t need the same level of security as patient health data from a medical device [12].
For devices with limited resources, lightweight protocols such as ETSI EN 303 645 are a smart choice to prevent hardware overload [7]. Instead of investing in custom encryption solutions - which can be costly and vulnerable - stick to proven algorithms like AES-256 and trusted libraries [7][9]. As the Information Commissioner’s Office (ICO) points out, encryption is widely available and doesn’t have to be expensive [8].
Shifting cryptographic workloads to the cloud can also cut costs. Cloud providers can handle tasks like TLS termination and key management, reducing the strain on local IoT devices and gateways [5]. For scenarios demanding high security, use hardware-based solutions like Trusted Platform Modules (TPM 2.0) or Trusted Execution Environments (TEE) to safeguard encryption keys, even if someone gains physical access to the device [7]. Additionally, secure private circuits, such as SD-WAN or bonded fibre, with protocols like IPsec or TLS to protect data in transit [5].
Once performance is optimised, the next step is ensuring your encryption strategy aligns with UK regulations.
Meeting UK Regulatory Requirements
Under UK GDPR, encryption is highlighted as an example of an appropriate technical and organisational measure
for securing data (Article 32) [8]. The National Cyber Security Centre (NCSC) reinforces this, stating that the level of security should match the potential impact of a confidentiality or integrity breach [7].
Your compliance plan should cover both data at rest (stored on servers or devices) and data in transit (transferred across networks) [8][7]. Use TLS 1.2 or TLS 1.3 for transport encryption and disable outdated SSL/TLS versions [19]. For web-based IoT interfaces, implementing HTTP Strict Transport Security (HSTS) ensures all connections use HTTPS, reducing the risk of downgrade attacks [19].
Maintain a cryptographic inventory to simplify audits [9]. Regularly update encryption keys, automating their renewal and re-encryption processes to minimise the risks of key compromise [9]. For IoT devices, enable remote deletion of sensitive data to mitigate the impact of lost or stolen devices, keeping GDPR breaches at bay [7].
Automating Compliance Monitoring and Reporting
Manually tracking compliance is time-consuming and prone to errors. UK GDPR mandates organisations to test, assess and evaluate the effectiveness of the technical and organisational measures
they use [9]. Automating these processes can save time and improve accuracy.
Audit logging plays a critical role in monitoring encrypted IoT data. Tools like AWS CloudTrail and Azure Monitor can automatically log access attempts, recording details such as IP addresses and protocols used [2][3][12]. For data classification, platforms like Azure Information Protection can label sensitive IoT data based on predefined rules, ensuring the right encryption levels are applied [3].
Automating certificate management is another way to simplify compliance. Services that handle TLS/SSL certificate renewals without manual intervention can reduce administrative overhead [2]. For sensitive workloads, consider hardware attestation to verify encryption during data processing [2]. Schedule regular reviews - at least annually - to evaluate your encryption measures and ensure signing keys are only used under proper permissions [9][2].
| Compliance Component | Recommended Standard/Tool | Function |
|---|---|---|
| Data in Transit | TLS 1.3, IPsec [8][5] | Encrypts data moving between devices and the cloud |
| Data at Rest | AES-256, FIPS 140-3 [8][9] | Protects stored data on devices and servers |
| Key Management | Azure Key Vault, AWS KMS, Managed HSM [2][12] | Centralised control and automated rotation of encryption keys |
| Logging & Audit | AWS CloudTrail, Azure Monitor [3][12] | Tracks access attempts and cryptographic operations |
| IoT Device Security | ETSI EN 303 645, TPM 2.0 [7] | Provides hardware-level protection for resource-constrained devices |
For organisations managing complex hybrid cloud environments, achieving both cost efficiency and regulatory compliance can feel overwhelming. Hokstad Consulting offers tailored solutions, helping businesses cut cloud expenses by 30–50% while maintaining strong security and compliance standards. Their expertise in hybrid cloud setups and automated infrastructure monitoring ensures your encryption strategies stay effective and within budget.
Conclusion and Key Takeaways
Protecting IoT data in hybrid cloud environments isn’t just a good practice - it’s a legal obligation under UK GDPR and the Data (Use and Access) Act, which came into effect on 19 June 2025 [8][10]. The risks of neglecting encryption are very real. For instance, in March 2022, Tucker's Solicitors LLP faced a £98,000 fine from the ICO after a ransomware attack exposed unencrypted court documents [20]. These incidents highlight the critical need for a well-planned, lifecycle-based encryption strategy.
Summary of Encryption Best Practices
To effectively secure IoT data, encryption must address all stages of its lifecycle - data at rest, in transit, and in use. This ensures protection from collection through to processing. Implementing AES-256 and TLS 1.3 protocols is a strong starting point [8]. Cryptographic keys should always be managed separately from the encrypted data [2][7]. Additionally, classifying your data before applying encryption is essential. Not all IoT data requires the same level of security, and this approach strikes a balance between protection and performance efficiency [2][12].
Automating processes like certificate rotation, key management, and compliance monitoring can significantly reduce errors and lighten administrative workloads [1][2]. To further safeguard encryption keys, adopt Role-Based Access Control (RBAC) and Multi-Factor Authentication (MFA) to ensure only authorised personnel have access [6]. The National Cyber Security Centre (NCSC) aptly warns:
Poorly chosen mechanisms or weak or poorly implemented algorithms often result in little or no security gains and may provide a false sense of security[7].
Next Steps for UK Businesses
With these best practices in mind, UK organisations can take proactive steps to strengthen their encryption strategies. Start by conducting a Data Protection Impact Assessment (DPIA) to evaluate data risks and identify encryption requirements [20]. Develop a formal encryption policy that specifies algorithms, key sizes, and rotation schedules to align with UK regulations [8]. Leveraging native cloud encryption tools can also provide a cost-effective way to achieve strong security [2][4].
For expert guidance, Hokstad Consulting offers tailored solutions to optimise cloud infrastructure while ensuring robust security and compliance. Their expertise in hybrid cloud environments and automated monitoring can help UK businesses implement encryption strategies that prioritise data protection without sacrificing efficiency.
FAQs
How can I ensure secure and consistent encryption for IoT devices in a hybrid cloud environment?
To ensure reliable and secure encryption for a variety of IoT devices in a hybrid cloud environment, start by adopting standards-based encryption protocols like TLS 1.2 or 1.3 for securing data in transit. For devices with limited processing capabilities, lightweight algorithms such as ECC are a great choice, while AES-256 is better suited for encrypting larger data payloads once a secure connection is established.
Streamline the process by centralising key and certificate management. Use a cloud-native key management service (KMS) or a secure secrets store to handle this efficiently. Automating key rotation and certificate provisioning ensures that devices can authenticate and encrypt data smoothly, whether interacting with public cloud platforms, private data centres, or on-premise systems.
Lastly, deploy tools to automate SSL/TLS certificate renewal and monitoring. This helps avoid disruptions caused by expired or improperly configured certificates. By following these steps, you can maintain strong encryption and seamless communication across all IoT devices in your hybrid cloud environment.
What should organisations consider when automating compliance monitoring for IoT data encryption?
To streamline compliance monitoring for IoT data encryption, organisations need to start by setting clear compliance goals. These could include aligning with standards like GDPR or ISO 27001. Once defined, these goals should be converted into machine-readable policies that automated tools can enforce and review continuously. Equally important is implementing identity and access controls, such as role-based access control (RBAC) and multi-factor authentication (MFA). Logging all privileged actions in immutable audit trails is essential to maintain transparency for audits.
Another key element is centralised key management. Automating processes like key retrieval, rotation, and injection within CI/CD pipelines helps minimise risks and ensures encryption keys are handled securely. Tools that generate short-term secrets and maintain detailed logs are particularly effective for meeting regulatory requirements.
Finally, leverage continuous monitoring platforms that can analyse logs from IoT devices, edge gateways, and cloud services. These platforms should be capable of identifying and alerting on encryption issues in real time. Automated reporting tools can then compile compliance dashboards and evidence packages, ensuring alignment with UK-specific regulations and showcasing encryption best practices across hybrid cloud and IoT setups.
How can I ensure IoT data encryption is cost-effective and compliant with UK regulations?
To strike the right balance between encryption performance, cost, and compliance with UK regulations, start by choosing an algorithm that fits your specific requirements. For instance, AES-256 is a solid choice for high-throughput data since it's supported by hardware acceleration on most cloud platforms. On the other hand, for low-power IoT devices, algorithms like ECC or ChaCha20 are better options, as they prioritise energy efficiency and minimise latency.
Centralising your key management is another essential step. Adopting a unified Key Management System (KMS) or a Hardware Security Module (HSM) can simplify compliance with regulations like GDPR. These systems reduce operational complexity, provide necessary audit trails, and automate key rotation, which not only strengthens your security but also helps avoid unexpected costs.
Lastly, keep a close eye on encryption-related expenses as part of a FinOps strategy. This includes monitoring CPU usage, storage encryption fees, and data transfer costs. You can optimise your workloads by adjusting instance sizes or leveraging spot capacity when it makes sense. By following these practices, you can ensure strong encryption measures without stretching your budget.
