Managing compliance across AWS, Azure, and GCP can be overwhelming. Each platform has unique protocols, and manual processes often lead to errors, misconfigurations, and security risks. By 2025, Gartner predicts 99% of cloud security failures will be caused by customers, with 70% due to misconfigurations. Automating compliance simplifies this by enforcing consistent rules, reducing errors by 90%, and cutting wasted cloud spend by 30%.
Key Takeaways:
- Automating compliance ensures continuous checks and prevents configuration drift.
- Tools like Terraform, Open Policy Agent (OPA), and Cloud Custodian help enforce policies and fix issues in real time.
- Centralised monitoring and audit data collection streamline oversight and reporting.
- Start with soft-fail policies, then enforce stricter compliance as teams adapt.
Automation not only reduces risks but also embeds compliance into everyday operations, making it manageable and efficient.
Policy as Code Automation for Multi-Cloud Security
Preparing for Cross-Cloud Compliance Automation
To tackle the complexities of compliance across AWS, Azure, and GCP, it's crucial to start with the right foundation. This means choosing tools that operate seamlessly across these platforms and translating regulatory requirements into machine-readable policies. Without proper groundwork, you risk creating fragmented systems that undermine your compliance efforts. A strong foundation ensures a cohesive strategy tailored to the challenges of managing multiple clouds.
Required Tools and Technologies
To automate compliance effectively in a multi-cloud environment, your toolkit should include Infrastructure as Code (IaC), Policy-as-Code (PaC), and scanning tools. These technologies work together to streamline processes and enforce compliance consistently.
- IaC Platforms: Terraform is a popular choice for provisioning resources across multiple cloud providers. Alternatives include AWS CloudFormation, which is AWS-specific, and Pulumi, which supports multiple clouds.
- Policy Validation: Tools like Open Policy Agent (OPA) use the Rego language to enforce rules across platforms. For those using Terraform Enterprise, HashiCorp Sentinel offers built-in policy enforcement.
- Pre-Deployment Scanners: Tools such as Checkov, tfsec, and KICS help identify misconfigurations in your IaC templates before deployment, catching potential issues early.
- Post-Deployment Monitoring: Cloud Security Posture Management (CSPM) solutions, including AWS Security Hub, Prisma Cloud, and Wiz, monitor live environments for drift and compliance violations.
- Automated Remediation: Cloud Custodian enables real-time scanning and can automatically address issues like unencrypted storage volumes.
- Centralised Management: AWS Organisations allows you to apply Service Control Policies (SCPs) across accounts, while CI/CD tools like GitHub Actions or AWS CodePipeline integrate compliance checks into deployment pipelines.
Policy-as-Code (PaC) is the cornerstone of effective multi-cloud governance. By standardising on a cloud-agnostic Infrastructure as Code tool... you can create a single, unified control plane.– Policyascode.dev
When rolling out new policies, consider starting with a soft-fail
approach. This alerts teams to violations without blocking deployments, giving them time to adjust. Once teams are familiar with the policies, you can transition to a hard-fail
model that enforces compliance strictly. Centralised workflows can help maintain consistency and ensure compliance baselines are uniformly applied.
Creating Compliance Policies
Once you have the right tools, the next step is to define compliance policies that turn regulatory standards into actionable rules. Begin by establishing unified policies that work across all cloud providers. Each policy should clearly reference the specific regulation it addresses. For example, a comment like // Enforces PCI DSS Req 3.4 can make it clear that a policy enforces encryption requirements.
One of the main challenges in multi-cloud environments is dealing with provider-specific differences. Instead of writing separate policies for each platform, use an abstraction layer - such as OPA - to normalise these differences. For instance, helper functions can account for variations in attribute names, like how different providers label public access controls.
To ensure consistency, maintain a centralised policy library that maps directly to established frameworks like CIS Benchmarks or SOC 2. This library should be version-controlled and integrated into your organisation's pipelines, so compliance standards are applied automatically. Establishing a Cloud Centre of Excellence (CCoE) to oversee this governance framework can help prevent tool sprawl and ensure alignment across teams. Automate remediation for low-risk issues, but require manual reviews for changes that pose higher risks.
How to Automate Compliance Across Clouds
::: @figure 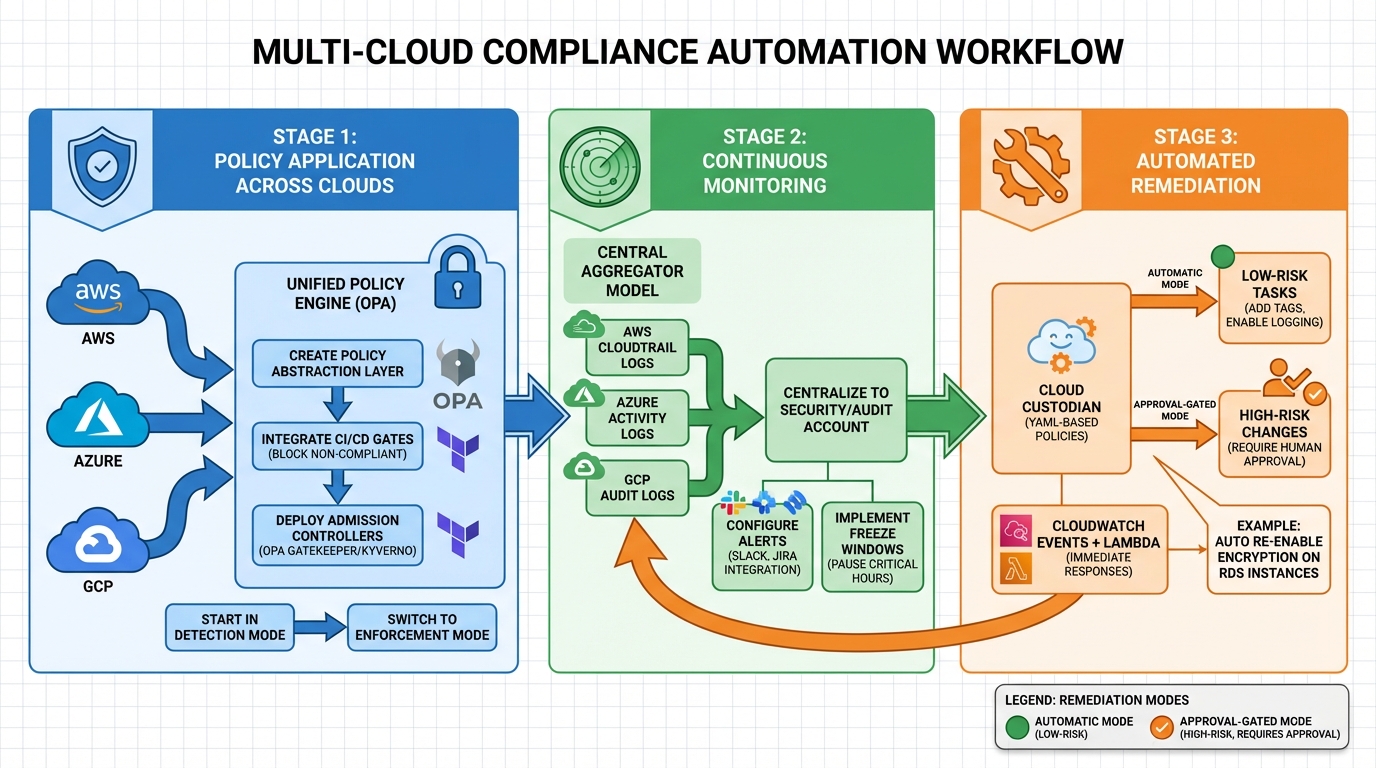 {Multi-Cloud Compliance Automation Workflow: From Policy Creation to Continuous Monitoring}
:::
{Multi-Cloud Compliance Automation Workflow: From Policy Creation to Continuous Monitoring}
:::
Once your policies and tools are in place, automation becomes the next step to ensure compliance is managed in real time. By automating compliance, you can enforce, monitor, and address policy violations seamlessly across pre-deployment, deployment, and live environments.
Applying Policies Across Multiple Clouds
To maintain consistent rules across platforms like AWS, Azure, and GCP, consider creating a policy abstraction layer. Tools such as Open Policy Agent (OPA) can help enforce a single set of rules, reducing duplication and simplifying maintenance.
Policy checks should be integrated at every stage of your workflow. For example:
- Use CI/CD gates to block deployments that fail compliance checks.
- In Kubernetes environments, deploy admission controllers like OPA Gatekeeper or Kyverno. These tools intercept
kubectlcommands and prevent the creation of non-compliant resources in real time.
When starting out, operate in a detection-only mode to gauge the impact of your policies. Once confident, switch to enforcement mode [6]. After that, set up continuous monitoring to maintain visibility and ensure compliance across your multi-cloud setup.
Setting Up Continuous Monitoring
Post-deployment monitoring is critical for detecting drift and configuration changes. A central aggregator model is often the most efficient. For instance, in AWS, enable Config recorders across all member accounts and consolidate compliance data into a dedicated Audit
or Security
account. This provides a unified view of violations across accounts and regions [6].
For a multi-cloud setup, centralise audit logs from AWS CloudTrail, Azure Activity Logs, and GCP Audit Logs into platforms like Microsoft Sentinel or Splunk. This unified perspective makes it easier to identify patterns and respond quickly to security events. To streamline operations, configure alerts to integrate with your existing tools - whether that’s Slack for team notifications or Jira for compliance tickets.
Introduce freeze windows to pause automatic remediation during critical business hours or scheduled maintenance. This prevents unexpected disruptions during high-demand periods. Lastly, automate remediation to address non-compliance issues as soon as they are detected.
Automating Remediation
For automated remediation, Cloud Custodian is a powerful choice. Its YAML-based policies and stateless rules engine allow you to manage resources across AWS, Azure, and GCP, while integrating with serverless runtimes like AWS Lambda for real-time responses [5][7]. According to its documentation:
Cloud Custodian is a tool that unifies the dozens of tools and scripts most organisations use for managing their public cloud accounts into one open source tool[5].
When automating remediation, categorise actions based on risk:
- Automatic mode: Handle low-risk tasks like adding missing tags or enabling logging on S3 buckets without human intervention.
- Approval-gated mode: For high-risk changes, such as altering production database configurations, require human approval before execution. This ensures security while avoiding unnecessary delays.
For immediate responses, configure CloudWatch Events to trigger Lambda functions that revert non-compliant changes. For example, if encryption is disabled on an RDS instance, a Lambda function can automatically re-enable it, ensuring compliance without delay.
Scaling Compliance Automation
As your multi-cloud infrastructure expands, keeping compliance in check becomes increasingly important. Avoid the chaos of managing multiple tools by sticking to a single, unified system for your policies and evidence. Many organisations that successfully scale treat compliance as code - storing policies in Git, testing them in development environments, and rolling them out through CI/CD pipelines, just like application code [2][8]. This streamlined approach not only keeps policies current but also ensures that evidence remains auditable.
Updating Policies Regularly
Regulations change, cloud providers release new services, and your infrastructure evolves. To keep up, appoint a Cloud Centre of Excellence (CCoE) to oversee and coordinate policy updates [3]. This team manages the universal policy engine and ensures consistent updates across all cloud environments.
When introducing new policies, start with a test-first approach. Deploy the updated rules in a development environment with enforcement mode turned off. This allows you to audit existing resources against the new policies without disrupting operations [8]. Once you’re confident that automated remediation tasks - like auto-encrypting a storage bucket - are working as intended, you can switch on enforcement mode.
Store all policies in version control, using names that directly correspond to regulatory controls. For instance, naming a policy file pci_dss_3_4_1.rego creates a clear, auditable link between the code and the specific compliance requirement [2]. Peer reviews for policy changes add an extra layer of oversight, ensuring the compliance framework evolves in a controlled and traceable way. With updated policies in place, the next step is to focus on centralising and simplifying audit evidence.
Collecting Audit Evidence in One Place
Centralising your audit evidence makes compliance a continuous and manageable process rather than a last-minute rush. Automate an evidence pipeline that gathers data from cloud APIs, policy evaluation logs, CI/CD logs, and vulnerability scanners into a centralised data lake [2]. A typical pipeline involves four stages: data collection, centralised storage, correlation and analysis, and reporting.
In AWS, for example, you can centralise configuration data using Config aggregators, then query and visualise the results with tools like Athena and QuickSight [9]. Store audit logs and policy decisions in immutable, WORM-enabled storage (e.g., S3 with Object Lock) to preserve evidence integrity [2].
Effective evidence doesn’t just show pass
or fail
outcomes. It should also include context - like resource attributes, timestamps, and the policy version applied. This level of detail not only makes audits smoother but also helps identify trends and patterns across your multi-cloud environment. By focusing on centralisation and transparency, you can transform compliance from a burden into a well-oiled, continuous process.
Conclusion
Automating multi-cloud compliance weaves regulatory requirements seamlessly into everyday operations. Instead of depending on nerve-wracking, one-off audits, automation ensures continuous, verifiable compliance, where compliance evidence is automatically generated as part of routine processes [2][4]. By embedding compliance into your infrastructure, you can address risks before they even have a chance to materialise [1]. This integrated strategy lays the groundwork for a robust and automated compliance framework.
This method offers centralised oversight and immediate issue resolution. Automated remediation steps in to fix violations or roll back changes as soon as drift is detected, preventing compliance gaps from escalating into larger problems [2][4]. When compliance checks are built directly into CI/CD pipelines, developers gain the tools they need to manage compliance independently, while non-compliant resources are stopped in their tracks before reaching production [2][10].
Start small by automating a handful of critical controls, then expand as your confidence in the system grows [2]. Consider establishing a Cloud Centre of Excellence to standardise your Infrastructure as Code (IaC) practices and policy engines [3]. Store policy decision logs in tamper-proof locations like S3 with Object Lock to ensure they remain unaltered and accessible for auditors [2]. Scaling these foundational steps will set the stage for fully automated governance.
Additionally, use AI-driven monitoring and carbon-aware governance to align cloud operations with environmental, social, and governance (ESG) goals [1]. Organisations that embrace automation today are preparing themselves for a future where regulatory needs are seamlessly integrated into infrastructure pipelines [1]. This forward-thinking approach not only cuts costs and simplifies workflows but also bolsters security across all cloud environments.
FAQs
What are the advantages of automating compliance in multi-cloud environments?
Automating compliance in multi-cloud environments comes with several advantages. For starters, it eliminates much of the manual effort, ensuring security policies and regulatory requirements are consistently applied across all platforms. This not only saves time but also reduces the chances of human mistakes slipping through.
On top of that, automation simplifies audits, making it far easier to prove adherence to industry standards. With proactive monitoring and management, businesses can cut operational costs, speed up deployment timelines, and lower the likelihood of fines or damage to their reputation. It’s a step towards building a cloud infrastructure that’s both secure and efficient.
What is Policy-as-Code, and how does it simplify compliance in multi-cloud environments?
Policy-as-Code allows organisations to write compliance rules in machine-readable code, which means automated testing, enforcement, and updates can be applied seamlessly across different cloud platforms. By embedding these policies directly into CI/CD pipelines, businesses can maintain consistent governance and keep a close eye on compliance across even the most complex multi-cloud environments.
This method not only cuts down on manual work but also reduces the risk of errors. It ensures compliance standards are uniformly applied across all cloud providers - a critical practice for companies managing varied cloud setups.
What are the key tools for automating compliance across AWS, Azure, and Google Cloud?
Automating compliance in multi-cloud environments demands tools that can enforce policies, monitor configurations, and deliver audit-ready evidence. One standout option is Open Policy Agent (OPA), a versatile, vendor-neutral engine that enables policy writing and evaluation across platforms like AWS, Azure, and Google Cloud. Another valuable tool, Terraform Sentinel, integrates compliance checks directly into infrastructure-as-code workflows, ensuring non-compliant resources are blocked before deployment.
For broader policy enforcement, Cloud Custodian offers a YAML-based approach to defining policies, automating remediation for non-compliance, and generating detailed reports. Additionally, each cloud provider comes with its own native tools: AWS Config tracks configuration changes and evaluates them against custom rules, Azure Policy enforces real-time guardrails with automated remediation, and Google Cloud Security Command Centre provides continuous monitoring and alerting for workloads on GCP.
These solutions are particularly helpful for UK organisations striving to maintain consistent compliance, quickly identify configuration drift, and meet regulatory standards like GDPR or ISO 27001. With the expertise of Hokstad Consulting, you can implement and fine-tune these tools to align with your organisation’s specific compliance needs and regulatory obligations.
