Vulnerability scanning is a key tool for organisations to meet security and compliance standards while keeping software development efficient. By automating checks in CI/CD pipelines, it identifies risks early, aligns with frameworks like ISO 27001, PCI DSS, and SOC 2, and provides audit-ready reports. Here's why it matters:
- Automated Security Checks: Scans code, dependencies, containers, and configurations to catch vulnerabilities before production.
- Compliance Alignment: Helps meet UK regulations like GDPR and PCI DSS by continuously assessing risks and generating evidence.
- Cost-Effective Risk Management: Fixing vulnerabilities early saves resources compared to addressing them post-deployment.
- Policy Enforcement: Automated gates ensure only secure builds proceed, while exceptions are documented and monitored.
- Audit Preparation: Centralised reports and metrics, such as remediation times and scan coverage, simplify regulatory audits.
Vulnerability Scanning and Compliance: The Basics
What is Vulnerability Scanning?
Vulnerability scanning is an automated process designed to uncover security flaws across your software delivery process. It scans everything from code and dependencies to containers and configurations, identifying common vulnerabilities. Unlike manual security reviews, these scans are triggered automatically by events like code commits or pull requests on CI/CD platforms such as Jenkins, GitLab, or GitHub Actions.
Think of it as an automated safety net that checks your pipelines before code moves into production. Tools like SonarQube, Checkmarx, and various container scanners step in early during development, testing code and images right from the first commits. By catching issues early, vulnerability scanning helps avoid costly fixes further down the line.
How Vulnerability Scanning Aligns with Compliance Standards
For organisations in the UK, vulnerability scanning plays a key role in meeting compliance requirements. It aligns with regulations such as the UK GDPR (under the Data Protection Act 2018), ISO 27001, and PCI DSS by continuously assessing risks and identifying potential vulnerabilities, whether related to data exposure, cardholder information, or pipeline security.
The real value lies in the detailed, audit-ready reports these tools generate. These reports include vulnerability severity rankings, remediation tracking, and policy enforcement logs, offering clear evidence of effective security measures. Such documentation not only demonstrates proactive risk management but also reassures regulators that security is deeply embedded in your development process. This makes vulnerability scanning a vital complement to manual testing methods.
Vulnerability Scanning vs. Penetration Testing
While both vulnerability scanning and penetration testing are essential for a strong security posture, they serve different purposes. Vulnerability scanning is automated and continuous, identifying known issues without exploiting them, which ensures a steady development pace. Penetration testing, on the other hand, is a manual, focused effort that simulates real-world attacks to validate security controls at specific intervals.
These two methods work best when used together. Regular vulnerability scanning provides ongoing detection of known flaws, while periodic penetration testing offers a deeper dive into your security defences. Combining the two ensures a more comprehensive security strategy and helps organisations maintain compliance while staying resilient against potential threats.
DevSecOps Governance: Automate Compliance Checks in Your CI/CD Pipeline
Adding Vulnerability Scanning to CI/CD Pipelines
::: @figure 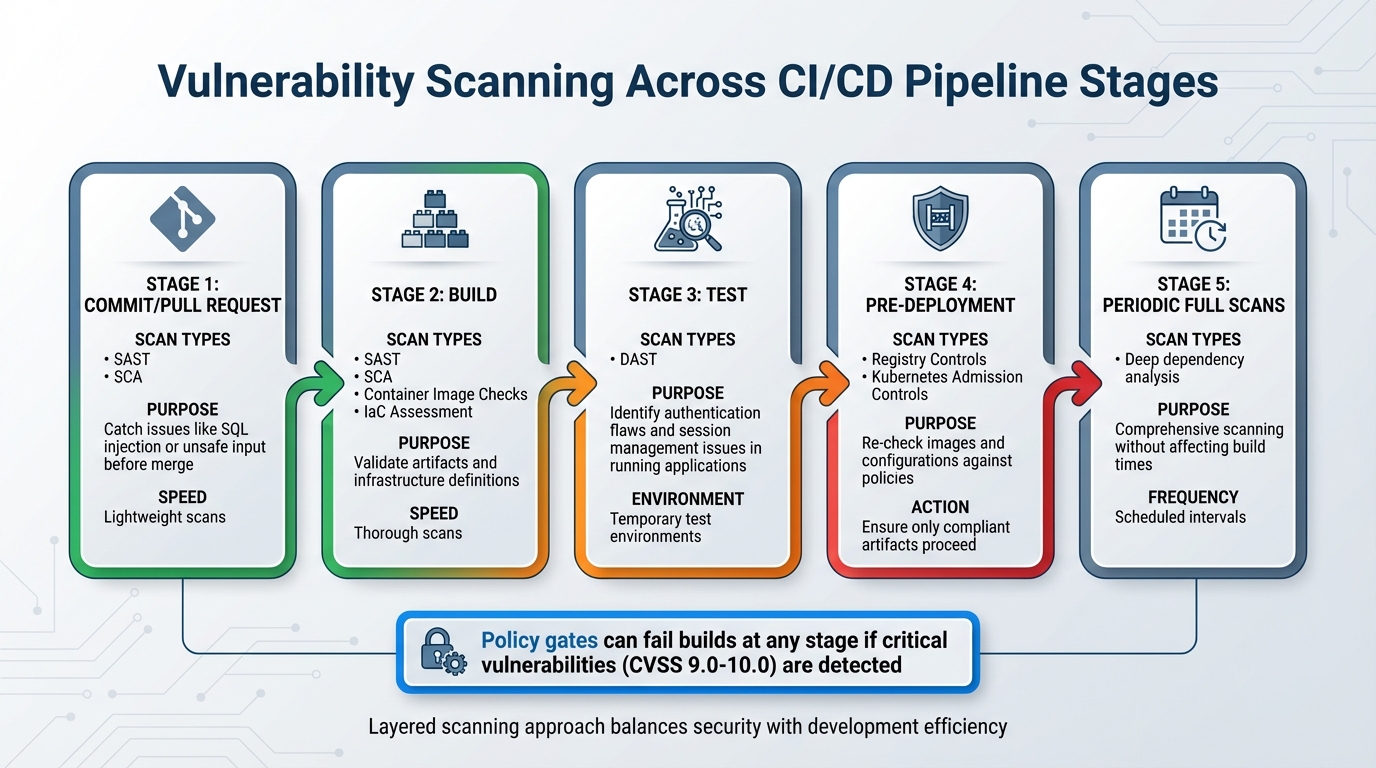 {CI/CD Pipeline Vulnerability Scanning Stages and Tools}
:::
{CI/CD Pipeline Vulnerability Scanning Stages and Tools}
:::
Scanning at Different Pipeline Stages
Integrating vulnerability scanning into your CI/CD pipeline is essential for balancing security and development efficiency. By running targeted scans at specific stages, you can address potential risks early without significantly slowing down workflows.
At the commit or pull-request stage, lightweight scans such as SAST (Static Application Security Testing) and SCA (Software Composition Analysis) can catch straightforward issues like SQL injection or unsafe input before code is merged into the central repository [1][5]. Moving to the build stage, more thorough scans are conducted, including SAST, SCA, container image checks, and IaC (Infrastructure as Code) assessments. These scans validate artefacts and infrastructure definitions before they are published to registries [1][2].
The test stage focuses on DAST (Dynamic Application Security Testing), which examines running applications in temporary test environments. These scans help identify vulnerabilities like authentication flaws or insecure session management [4][5]. Before deployment, registry and Kubernetes admission controls re-check images and configurations against established policies, ensuring only compliant artefacts are deployed in production environments [2]. Additionally, scheduling periodic full scans enables deeper analysis of dependencies without affecting individual build times [1][3].
This layered scanning process lays the groundwork for automated policy gates, which ensure compliance throughout the pipeline.
Using Policy Gates to Enforce Compliance
Policy gates provide an automated way to enforce security standards by evaluating scan results against predefined risk thresholds. For instance, pipelines can be configured to fail automatically if a critical vulnerability (e.g., CVSS score of 9.0–10.0) is detected in application code, container images, or infrastructure components [1][2]. High-severity issues may be allowed in non-production environments, but only with explicit risk approval, while medium and low-severity findings typically generate warnings and remediation tickets [1].
There are several ways to implement these gates. CI configurations can be set to exit with a non-zero status if thresholds are breached. Registry or Kubernetes admission controllers can block non-compliant images, and tools like GitLab can enforce scan and pipeline execution policies across projects [2][6]. For organisations in the UK adhering to standards like PCI DSS or ISO 27001, these policies should be version-controlled, documented, and aligned with regulatory frameworks that require timely mitigation of high-risk vulnerabilities [3][4].
Managing Risk and Exceptions
When fixing vulnerabilities immediately isn’t possible, a structured risk acceptance process becomes crucial [3]. This involves documenting the issue, including its severity, the affected systems, the potential impact on UK customer data, and the reasoning behind delaying remediation [3].
To mitigate risks in the interim, compensating controls such as enhanced firewalls, stricter network segmentation, or increased monitoring can be implemented. Each exception should have a review and expiry date, ensuring it is revisited periodically [4]. These exceptions should be tracked in a centralised register or GRC (Governance, Risk, and Compliance) tool and linked to CI scan results. This allows policy gates to differentiate between approved exceptions and new vulnerabilities [1][3].
During audits, maintaining detailed documentation - such as scan histories, exception records, and remediation tickets - demonstrates that vulnerabilities are actively managed. This approach satisfies both regulatory requirements and business expectations, showing that risks are being handled responsibly rather than ignored [3][4].
Need help optimizing your cloud costs?
Get expert advice on how to reduce your cloud expenses without sacrificing performance.
Creating Evidence for Compliance Audits
When it comes to compliance audits, having thorough and well-organised evidence is just as important as conducting vulnerability scans and remediation. Let’s break down what auditors look for and how to keep everything centralised and efficient.
What Evidence Do Auditors Need?
Auditors typically ask for a range of documentation to confirm that your organisation is meeting compliance standards. This includes:
- A vulnerability management policy that outlines scan schedules, scopes, and tool configurations. Supporting evidence like screenshots or exported settings is often required.
- An asset register listing all in-scope systems.
- Scan reports from the past 6–12 months. These reports should include:
- Details on identified vulnerabilities, their CVSS (Common Vulnerability Scoring System) ratings, and the affected components.
- Evidence of a complete remediation workflow, such as ticket system records, pull requests, deployment logs, and management reports.
- Key report details like the date and time (in UK local time with offset), scan scope (e.g., IP ranges, domains, repositories), scan type, triggering CI/CD job, and build version.
- Annotations linking the report to relevant policies or standards, along with justifications for any known false positives [1].
Keeping these reports centralised and well-structured is critical for audit readiness.
Centralising Evidence Management
A centralised repository for evidence not only simplifies audits but also demonstrates continuous monitoring and control. Ideally, this repository should align with your Information Security Management System (ISMS) or Governance, Risk, and Compliance (GRC) framework.
Here’s how to structure it effectively:
- Organise evidence by standard (e.g., ISO 27001, PCI DSS, SOC 2), control ID, and system.
- Store documents in a version-controlled, access-restricted system such as Git, SharePoint, or a GRC tool.
- Include key items like scan reports, pipeline logs, tool configurations, policies, and SOPs, tagged with metadata such as system name, environment, date, and responsible owner.
Automation can make this process even smoother. For instance, integrating scanning tools, ticketing systems, and GRC platforms can automatically link reports and closure evidence to the appropriate controls. Imagine a failed container image scan triggering a ticket, attaching the related report, and flagging the associated GRC control as non-compliant
until the issue is resolved. For UK organisations using an ISO 27001 ISMS, this kind of automation provides a clear, tool-supported control lifecycle, eliminating the need for last-minute evidence scrambling during audits [2].
Tracking Metrics for Continuous Improvement
Auditors are also keen to see metrics that demonstrate progress over time. These metrics highlight how your organisation is reducing risks and improving processes. Common examples include:
- The number of open vulnerabilities, broken down by environment and severity.
- Mean Time to Remediate (MTTR) for critical and high-priority issues.
- The age of unresolved vulnerabilities (e.g., critical issues older than 30 days).
- Scan coverage, showing the percentage of applications, repositories, containers, and cloud accounts regularly scanned.
- Pipeline failure rates due to security gates.
To track these metrics, export scan results from CI/CD jobs into a central database or metrics system like Prometheus or Elasticsearch after each run. Dashboards can then aggregate the data and calculate metrics like MTTR, using timestamps to measure how long it takes to resolve vulnerabilities from detection to closure.
Set clear targets to guide your team’s efforts, such as:
- 100% scan coverage for internet-facing services.
- No unresolved critical vulnerabilities in production (with a seven-day SLA).
- Reduction in high-severity issues older than 30 days.
Leveraging External Expertise
If building and maintaining this evidence model feels daunting, external specialists can help. They can align your scanning outputs with regulatory requirements, fine-tune configurations to minimise unnecessary noise, and implement automation to streamline evidence collection. Firms like Hokstad Consulting, which focus on DevOps, cloud infrastructure, and automation, can optimise your tools and processes. They can even introduce AI-driven solutions to summarise raw scan data into actionable insights, creating reports that resonate with UK boards and regulators [1].
Working with Experts for Compliance-Driven Scanning
Aligning Scanning Strategies with Compliance Requirements
Automated scanning and audit-ready evidence lay the groundwork, but expert input takes compliance strategies to the next level. External specialists can help transform vague compliance mandates into clear, actionable scanning plans. For instance, instead of relying on trial and error to choose tools or determine their placement, experts create a detailed control matrix. This matrix maps specific compliance clauses - like PCI DSS's requirement for regular internal scans or ISO 27001's A.12.6.1 on vulnerability management - to the appropriate scan types, such as SAST, SCA, DAST, container scanning, or infrastructure-as-code checks [3][4][8].
They also ensure these controls align with the right stages of the CI/CD pipeline. For example, SAST and secrets scanning might occur at the pre-commit and build stages, dependency and SCA checks at build, container image scanning during build and registry stages, and DAST in staging or pre-production environments [1][5][8]. The result is a comprehensive mapping document that specifies which tool runs where, how often, under what policy, and how evidence is collected. This ensures each compliance control is both auditable and defensible during an audit, supporting long-term compliance efforts.
Reducing Costs and Improving Efficiency in Scanning
Bringing in consultants isn’t just about compliance - it’s also about efficiency. Experts can assess the financial impact of scan frequencies, tool choices, and infrastructure usage [1][3]. For instance, they might recommend scheduling resource-heavy scans, like DAST or container scans, during off-peak hours. Using ephemeral build agents with auto-scaling runners and optimising container resources can prevent expensive infrastructure from sitting idle [1][2].
By embedding metrics such as cost per build, scan duration, and failure rates into pipelines, teams can fine-tune their policies. For example, full scans might only run on release candidates, balancing cloud costs with compliance risks. These efficiency gains often pave the way for more advanced automation, streamlining compliance without sacrificing quality.
Custom Automation and AI-Driven Solutions
Custom automation can take compliance to a whole new level. For example, it can categorise findings by severity, affected component, and regulatory relevance, then automatically create or update tickets in tools like Jira or ServiceNow with all the details auditors need [1][3]. Policy-as-code engines can enforce rules like failing builds only for critical issues, reducing unnecessary alerts while maintaining strong controls [1][8].
AI-powered tools add even more value by correlating results from multiple scanners - SAST, SCA, DAST, container, and IaC - to eliminate duplicate alerts and highlight vulnerabilities most likely to be exploited in the current environment [1][4]. These tools can also generate easy-to-read summaries and tailored remediation suggestions, cutting down the time it takes to address issues [5][8]. Companies like Hokstad Consulting specialise in designing and integrating these solutions into existing workflows, ensuring they meet UK and EU data handling and privacy regulations [4][7].
Conclusion
Vulnerability scanning turns compliance into an ongoing, automated process, providing reliable audit evidence throughout [3][5]. By integrating scans at various stages of the pipeline - spanning source code, dependencies, containers, infrastructure-as-code, and runtime images - organisations can identify issues early, well before deployment. This not only reduces the cost and effort of fixing problems but also aligns with frameworks like ISO 27001, SOC 2, and PCI DSS, all while keeping development moving efficiently [1][3][5].
Once scans are complete, enforceable policy gates step in. These automated gates ensure that risk thresholds are met by blocking non-compliant builds [1][2]. Lower-severity findings can still be monitored within agreed SLAs, preventing unnecessary delays in the pipeline while maintaining robust oversight. Any exceptions must be documented, time-limited, and approved to ensure they remain audit-ready [3][6]. Consolidating scan results, remediation tasks, and risk acceptance records into a single system creates the kind of detailed audit trail that regulators expect [3][2]. Additionally, tracking metrics like remediation times, scan coverage, and overdue issues highlights ongoing improvements, a key requirement for most modern compliance frameworks [4][5].
To provide a well-rounded assurance, automated scanning should be complemented with regular penetration testing and manual reviews, meeting the expectations of regulators and industry standards [3][4].
FAQs
What’s the difference between vulnerability scanning and penetration testing?
Vulnerability scanning and penetration testing play distinct roles in keeping systems secure.
Vulnerability scanning is an automated process designed to spot known security flaws. By comparing your systems against a database of vulnerabilities, it helps uncover weaknesses that could be exploited. Think of it as a proactive check-up to catch issues early.
Penetration testing, however, goes a step further. It involves manual or semi-automated techniques where testers mimic real-world attacks to exploit vulnerabilities actively. This approach offers a clearer picture of how attackers might breach your defences and the damage they could cause.
Both processes are crucial for ensuring compliance and bolstering security, particularly in fast-paced environments like CI/CD pipelines, where frequent updates can lead to new risks.
How do policy gates help maintain compliance in CI/CD pipelines?
Policy gates are an essential part of maintaining compliance within the CI/CD pipeline. These checkpoints automatically enforce specific rules and standards at crucial stages, stopping any code that doesn't meet the required criteria from progressing further. This helps ensure that regulatory requirements and security policies are consistently upheld.
By embedding these gates into your pipeline, you can make sure that only code meeting the set compliance standards gets deployed. This not only reduces risks but also simplifies the process of aligning with industry regulations.
How does vulnerability scanning assist with audit preparation?
Vulnerability scanning is an essential step in getting ready for audits. It helps spot security weaknesses and compliance issues early, giving you the chance to address them long before the audit begins. This proactive method shows a clear dedication to maintaining security and meeting compliance standards.
Fixing these issues ahead of time reduces audit risks, simplifies the process, and allows you to present auditors with solid proof of your efforts. Beyond just meeting regulatory obligations, it also bolsters your overall security framework.
