If you're managing security risks, tracking the right metrics is critical. Vulnerability Management KPIs (Key Performance Indicators) help you assess how effectively your organisation identifies, prioritises, and resolves security gaps. Here's why they matter:
- Speed is crucial: 75% of vulnerabilities are exploited within 19 days, yet the average patching time is over 100 days. This gap leaves systems exposed.
- Risk focus beats volume: Not all vulnerabilities are equal. Metrics like Mean Time to Remediate (MTTR) and SLA Compliance Rate help prioritise what's most important.
- Business alignment is key: Metrics that translate technical risks into financial impact resonate better with leadership and justify security investments.
Key Metrics to Track:
- Mean Time to Detect (MTTD): How quickly vulnerabilities are identified.
- Mean Time to Remediate (MTTR): Time taken to fix issues, directly impacting risk exposure.
- Patch Latency: Time between patch release and deployment.
- SLA Compliance Rate: Percentage of vulnerabilities fixed within agreed timeframes.
- Vulnerability Recurrence Rate: How often previously resolved issues reappear.
Real Examples:
- A travel insurance provider reduced vulnerabilities by 86% and saved £800,000 annually by automating processes.
- A medical device company cut vulnerability review times by 90% using machine learning.
- Organisations using modern platforms have drastically reduced detection and remediation times.
Best Practices:
- Focus on risk-based prioritisation rather than sheer vulnerability counts.
- Align KPIs with compliance frameworks like NIST or ISO 27001.
- Use automation to streamline detection and remediation, integrating KPIs into DevOps workflows.
By focusing on meaningful metrics and aligning them with business goals, organisations can close the vulnerability gap and strengthen their security posture.
::: @figure 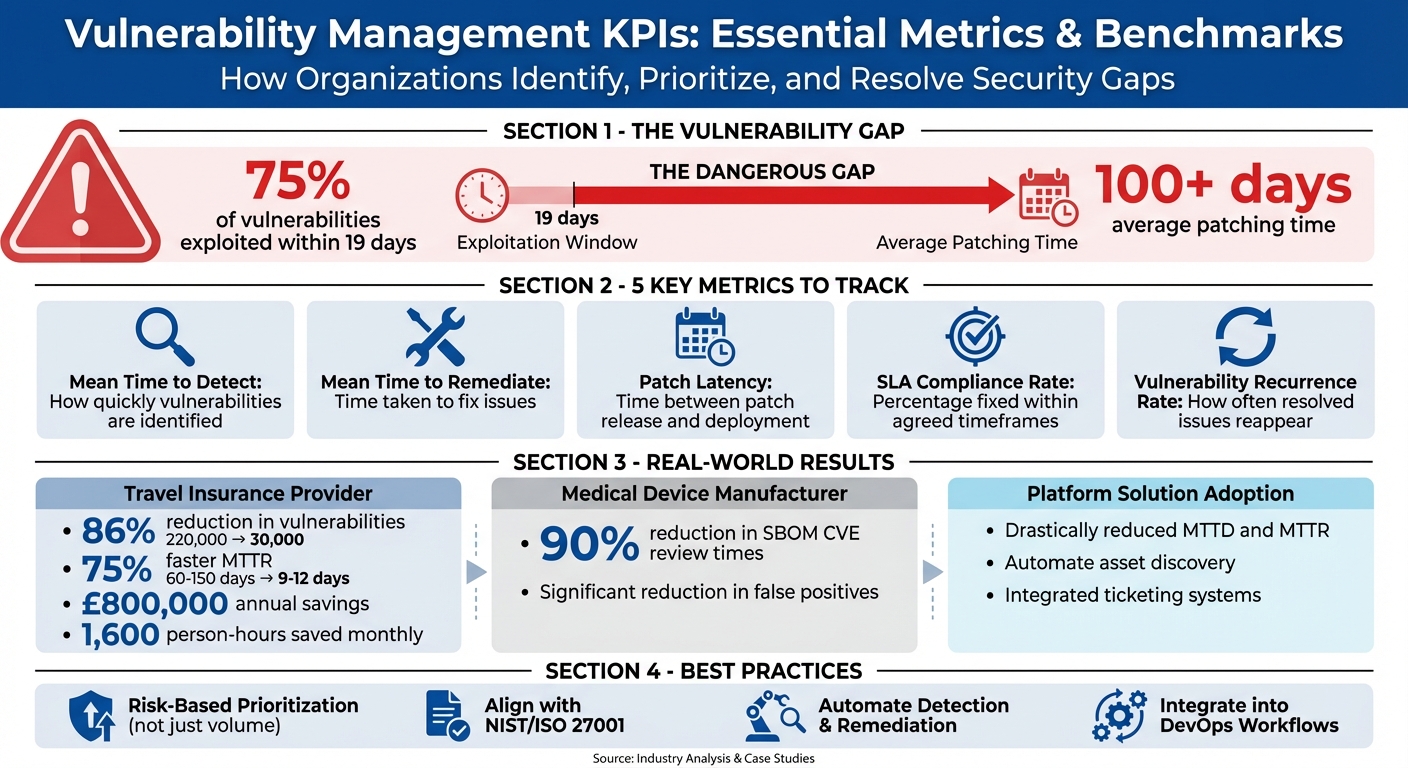 {Vulnerability Management KPIs: Key Metrics and Performance Benchmarks}
:::
{Vulnerability Management KPIs: Key Metrics and Performance Benchmarks}
:::
Case Studies: How Organisations Use Vulnerability Management KPIs
Case Study 1: Reducing Risk for a Travel Insurance Provider
Between 2021 and 2023, PurpleSec implemented a risk-focused vulnerability management programme to tackle 220,000 vulnerabilities for a travel insurance provider. Instead of merely counting vulnerabilities, the provider prioritised addressing risks that were critical to their business operations. By combining AI-driven automation with expert security teams, they automated routine scanning and categorisation tasks. This freed up specialists to concentrate on high-priority threats.
In just six months, the results were striking:
- Vulnerability counts dropped by 86%, going from 220,000 to 30,000.
- The Mean Time to Remediate (MTTR) improved by 75%, shrinking from 60–150 days to just 9–12 days.
- Overall, remediation speed increased by 90%.
- Automation saved 1,600 person-hours per month, leading to annual cost savings of approximately £800,000.
- Enhanced dashboards provided better insights into bottlenecks within business units, improving the organisation's overall security posture by 11%.
| Metric | Before Implementation | After Implementation | Improvement |
|---|---|---|---|
| Vulnerability Risk | Baseline (100%) | 14% | 86% reduction |
| Mean Time to Remediate | 60–150 days | 9–12 days | 75% reduction |
| Vulnerability Count | 220,000 | 30,000 | 86% reduction |
| Monthly Person-Hours Saved | – | 1,600 hours saved | - |
These results highlight how a focused approach to vulnerability management can yield substantial benefits, paving the way for similar applications across other industries.
Case Study 2: Improving Efficiency in a Medical Device Manufacturer
Another example comes from a global medical device manufacturer that faced challenges in manually reviewing SBOM (Software Bill of Materials) vulnerabilities. The process was slow, labour-intensive, and prone to errors. To address this, the organisation adopted a hybrid approach, blending machine learning algorithms with human oversight to streamline the review of SBOM CVEs (Common Vulnerabilities and Exposures). By introducing a targeted metric - SBOM CVE Review Times - the security team achieved a 90% reduction in review times. This not only sped up the process but also significantly reduced false positives.
These improvements provided tangible evidence of the programme's return on investment (ROI), which helped secure buy-in from senior leadership.
Case Study 3: Faster Remediation with Platform Solutions
One organisation tackled slow remediation times by adopting a modern vulnerability management platform. Previously, manual processes caused delays between vulnerability detection and remediation, leaving systems exposed for longer periods. With the new platform, features like automated asset discovery and intelligent prioritisation drastically reduced the time between identifying vulnerabilities and starting remediation.
Additionally, integrating ticketing systems and Role-Based Access Control (RBAC) ensured vulnerabilities were promptly assigned and addressed. Key performance indicators - such as Mean Time to Detect (MTTD), Mean Time to Inform (MTTI), and Mean Time to Remediate (MTTR) - provided clear insights into the improvements achieved. These changes streamlined workflows and reduced the exposure window, significantly enhancing the organisation's security posture.
Best Practices for Vulnerability Management KPIs
Prioritising the Most Important KPIs
Case studies highlight a recurring theme: successful organisations prioritise risk-based metrics over simply tallying vulnerabilities. For instance, best practices recommend addressing critical-risk vulnerabilities within 3–7 days [4]. This urgency stems from the fact that, on average, vulnerabilities appear in the CISA Known Exploited Vulnerabilities catalogue - indicating active exploitation - just seven days after disclosure [7].
Metrics that combine severity, exploitability, and asset criticality offer more actionable insights than raw CVSS scores. In fact, prioritising vulnerabilities with exploit code is 11 times more effective at reducing exploitability than relying solely on CVSS numbers [7]. Additionally, maintaining a scan coverage rate of at least 95% is essential to eliminate blind spots [4].
Another crucial metric is the recurrence rate (or reopen rate). When vulnerabilities that were previously fixed reappear, it often points to systemic issues with baseline configurations. By tracking this, organisations can determine whether their remediation efforts are genuinely effective or just superficial [1][5].
Avoiding Common Mistakes
While selecting the right KPIs is vital, avoiding common mistakes is just as important. One frequent error is treating all vulnerabilities as equal, regardless of their context. For example, a vulnerability on a guest Wi-Fi laptop poses far less risk than one on a production database [4]. Yet many organisations fail to differentiate, creating unnecessary work and diluting focus on critical threats.
Presenting vulnerability reports to senior management without key metrics will also limit your ability to effectively communicate the overall risk of your organization.– Michael Swanagan, CISSP, PurpleSec [1]
Fragmented data across multiple platforms also undermines effective reporting. Consolidating information into a single dashboard resolves this issue [4][2]. However, it’s important to avoid overloading dashboards with excessive data. Limit reports to 3–5 high-value KPIs per stage of the vulnerability management process [4]. Keep in mind that only 37% of organisations have fully developed risk-based prioritisation processes [2]. A focused and straightforward approach often yields more actionable insights.
Lastly, don’t assume that closing a ticket means the issue is resolved. Automated validation or rescanning is essential to confirm that fixes are effective [2]. Without this step, you’re merely tracking activity, not outcomes.
Integrating Vulnerability Management KPIs with DevOps and Cloud Monitoring
Embedding KPIs into CI/CD Pipelines
Incorporating vulnerability management KPIs directly into CI/CD pipelines transforms security into a proactive and integral part of the development process. By embedding automated security tools - such as SAST, DAST, and SCA - into these pipelines, organisations can monitor metrics like Mean Time to Detect (MTTD) in real time. This approach enables early identification of vulnerabilities, which often leads to faster and more cost-effective fixes [8][9]. Security configurations can also be codified alongside application code, while telemetry hooks (M.E.L.T.) enhance both preventative and reactive monitoring [9]. Focusing on runtime-exploitable code can reduce patching efforts by as much as 60% [11].
All an engineer has to do is click a link, and they have everything they need in one place. That level of integration and simplicity helps us respond faster and more effectively.– Sajeeb Lohani, Global Technical Information Security Officer, Bugcrowd [9]
Using well-established KPIs, such as Mean Time to Repair (MTTR), as a baseline helps track progress over time. Additionally, organisations should monitor error budgets through service level indicators (SLIs) and service level objectives (SLOs). If error budgets are exceeded, it should trigger a renewed focus on improving performance and security [10].
Using Cloud Monitoring for Faster Remediation
Taking CI/CD integration a step further, cloud monitoring adds another layer of efficiency to vulnerability remediation. Cloud-native monitoring tools offer real-time visibility into critical KPIs, enabling teams to address vulnerabilities without delay. Automated asset discovery ensures that new resources - whether cloud instances, containers, or serverless functions - are immediately included in scan coverage [4]. This is crucial given that 75% of cyber-attacks exploit vulnerabilities that have been known for at least two years [12].
Cloud monitoring consolidates data from various sources, including asset inventories, vulnerability scanners, threat intelligence feeds, and configuration management databases (CMDBs) [1]. Risk-based prioritisation, supported by Vulnerability Priority Ratings (VPR), ensures that teams focus on vulnerabilities that pose the most substantial threats in production environments, rather than simply addressing issues based on volume [3]. For actionable insights, it’s essential that at least 90% of critical risks are assessed with threat context, such as data from CISA's Known Exploited Vulnerabilities catalogue [4].
Continuous validation plays a key role in ensuring remediation efforts are effective. Automated testing or breach-and-attack simulations can confirm whether patches have successfully mitigated risks [2].
Basic vulnerability scans tell you where you're vulnerable, but Cymulate tells you if you will be compromised. Vulnerability scanning just gives a report. Cymulate gives us intelligence.– Shaun Curtis, Head of Cybersecurity, GUD Holdings [2]
For best results, critical vulnerabilities should ideally be addressed within 3–7 days [4]. Integrating cloud monitoring tools with ticketing systems can further streamline the process by automating ownership assignment and tracking. This not only reduces response times but also supports compliance with service-level agreements (SLAs) [1].
Hokstad Consulting's Approach to Security

Hokstad Consulting exemplifies these practices through a comprehensive approach to security integration. Their solutions embed security into every stage of DevOps transformation and cloud optimisation. By integrating automated security checks into CI/CD pipelines and performing continuous cloud security audits, Hokstad helps clients cut cloud costs by up to 50% while maintaining compliance. Their services include Security as Code practices and AI-powered threat detection, enabling streamlined monitoring and remediation with minimal manual effort. With flexible engagement models - such as retainer-based support or a no savings, no fee
option - Hokstad makes expert security guidance accessible without significant financial risk.
Need help optimizing your cloud costs?
Get expert advice on how to reduce your cloud expenses without sacrificing performance.
Vulnerability Management Metrics: Top 10 KPIs To Measure Success
Conclusion
Managing vulnerabilities effectively hinges on choosing KPIs that genuinely reflect your organisation's security health. Interestingly, 67% of surveyed leaders admit their vulnerability programme metrics fall short [13]. This underscores a common struggle: turning technical data into actionable insights for business decisions. The case studies in this article highlight that true success comes from moving past just counting vulnerabilities. Instead, focusing on context - like business impact, exploitability, and asset importance - leads to more meaningful prioritisation [4][13].
Metrics alone don't tell the full story. For instance, high remediation rates lose their value if scan coverage declines [6]. To make better decisions, it's essential to balance operational numbers with outcome-focused measures, such as risk reduction [13][5].
Integrating KPIs into DevOps workflows and cloud monitoring can shift security practices from being reactive to proactive. This approach aligns with earlier findings on proactive security strategies. Leading teams, for example, resolve critical vulnerabilities within just 3–7 days by leveraging automation and centralised data management [1][4].
With 75% of cyber-attacks exploiting vulnerabilities that are over two years old [6], the cost of inadequate vulnerability management goes far beyond regulatory compliance. To address this, organisations should adopt risk-based SLAs, dynamic risk scoring, and tailored dashboards that connect technical risks to their broader business impact [1][4].
For the future, expert recommendations can help businesses transition from basic vulnerability scanning to a more advanced exposure management approach. Automating security checks in CI/CD pipelines and conducting continuous cloud audits can significantly lower risks and expenses while maintaining compliance.
FAQs
What are the key KPIs for successful vulnerability management?
Key performance indicators (KPIs) play a crucial role in assessing and enhancing vulnerability management strategies. Here are some key metrics that organisations should keep an eye on:
- Mean time to remediation (MTTR): This tracks how quickly vulnerabilities are addressed after being identified, giving insight into response efficiency.
- Risk score: This evaluates the severity of vulnerabilities, factoring in the levels of risk that have been deemed acceptable.
- Average vulnerability age: This measures how long vulnerabilities remain unresolved, highlighting potential delays in mitigation efforts.
- Scan frequency and asset coverage: This monitors how often systems are scanned and what percentage of assets are included, ensuring no critical areas are overlooked.
- Rate of recurrence: This indicates how often previously resolved vulnerabilities resurface, pointing to gaps in the overall process.
Keeping a close eye on these KPIs allows organisations to focus their resources effectively, reduce exposure to threats, and maintain compliance with service-level agreements (SLAs).
How does automation enhance vulnerability management?
Automation takes vulnerability management to the next level by making processes faster and more precise. With automated tools, regular scans can be scheduled across all assets, cutting down on manual work and ensuring no gaps in coverage. These tools also use contextual risk scores to rank vulnerabilities in real time, allowing security teams to zero in on the most urgent issues first.
On top of that, automation connects vulnerability data with asset inventories, builds live KPI dashboards, and even generates remediation tickets directly within change-management systems. This means quicker response times, fewer backlogs, and measurable cost savings in pounds (£). It also helps organisations stay compliant with UK regulations and reporting standards.
Hokstad Consulting supports businesses in integrating automation into their DevOps pipelines, ensuring continuous asset monitoring, better KPI tracking, and smoother workflows.
Why is it important to prioritise vulnerabilities based on risk?
The sheer volume of software vulnerabilities uncovered each year can leave security teams feeling buried. Just look at 2022: over 26,000 new vulnerabilities were reported, with critical issues climbing steadily. Many organisations are left with daunting backlogs of unpatched flaws, making it tough to decide what demands attention first.
This is where a risk-based approach becomes essential. By evaluating vulnerabilities based on factors like how easily they can be exploited, the importance of the affected asset, and the potential impact on the business, teams can zero in on the most urgent threats. This method sifts out lower-priority issues, allowing for quicker and more efficient fixes.
Beyond that, prioritising by risk brings other benefits. It delivers clear metrics that help allocate resources wisely, supports smarter decision-making, and tracks progress in reducing cyber risks. In short, it turns overwhelming amounts of data into actionable steps, ensuring vulnerability management aligns with the organisation's broader goals.
