Policy as Code (PaC) transforms cloud governance by automating and embedding compliance checks directly into development workflows. It replaces slow, error-prone manual processes with executable, version-controlled rules, ensuring faster, consistent, and secure cloud operations. By integrating governance into tools like IDEs and CI/CD pipelines, organisations can catch misconfigurations early, reduce errors by up to 90%, and accelerate security reviews tenfold. Here's why it matters:
- Automation: Eliminates manual reviews, saving time and reducing mistakes.
- Consistency: Policies are applied uniformly across environments.
- Compliance: Simplifies adherence to standards like GDPR and ISO 27001.
- Cost Control: Enforces tagging, resource limits, and prevents overspending.
- Scalability: Adapts to growing infrastructure without adding complexity.
PaC uses tools like Open Policy Agent (OPA), Azure Policy, or HashiCorp Sentinel to enforce rules during development and runtime. This approach not only improves security and compliance but also empowers developers with immediate feedback and streamlined processes. Adopting PaC step-by-step - starting with impactful policies and integrating them into CI/CD pipelines - helps organisations modernise governance without disrupting existing workflows.
Policy-as-Code for Infrastructure-as-Code with OPA and OpenTofu - Colin Lacy, Cisco
What is Policy as Code?
::: @figure 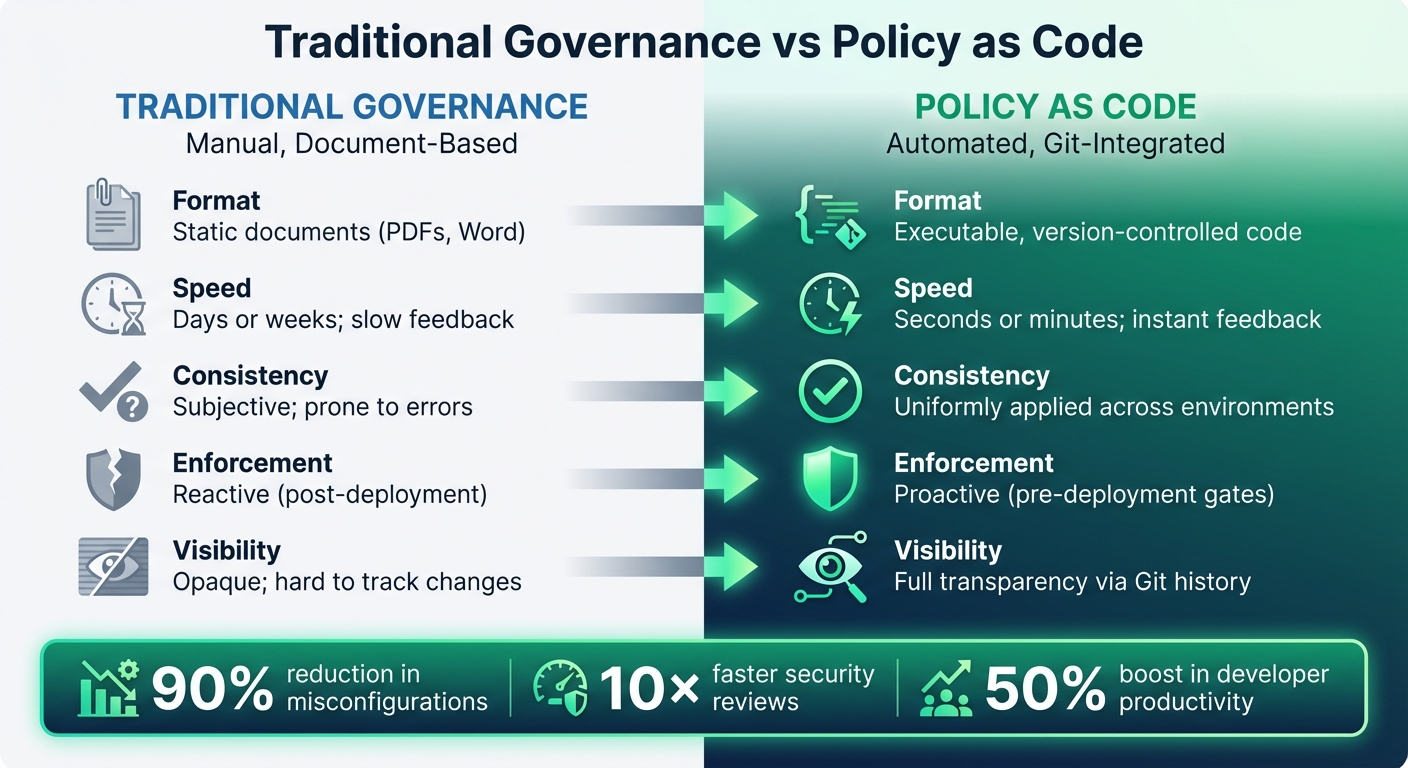 {Traditional Governance vs Policy as Code Comparison}
:::
{Traditional Governance vs Policy as Code Comparison}
:::
Policy as Code (PaC) is all about turning infrastructure governance rules into code that can be executed, versioned, and enforced automatically. Instead of relying on static documents like PDFs or Word files, organisations write these rules in declarative languages - such as Rego or Sentinel - and manage them through Git [1]. This approach modernises governance by embedding it directly into the development process, making it faster, more consistent, and easier to track.
Think of Infrastructure as Code as the blueprint for your cloud setup; Policy as Code is like the automated inspector ensuring everything meets security, compliance, and cost standards before deployment [1]. By integrating governance early - right into your IDE, pre-commit hooks, and CI/CD pipelines - violations are caught when they’re easiest and cheapest to address. This shift-left
philosophy brings governance into the development workflow itself.
Traditional governance, by contrast, feels slow and clunky. It relies on manual reviews, periodic audits, and inconsistent processes that can create bottlenecks and lead to mistakes [1]. As Kashaf Salaheen and Mitch Pronschinske from HashiCorp put it:
Policy as code gives you an automated way to check, in minutes or seconds, if your IT and business stakeholders' requirements are being followed in your infrastructure deployments [3].
| Feature | Traditional Governance | Policy as Code |
|---|---|---|
| Format | Static documents (PDFs, Word) | Executable, version-controlled code |
| Speed | Days or weeks; slow feedback | Seconds or minutes; instant feedback |
| Consistency | Subjective; prone to errors | Uniformly applied across environments |
| Enforcement | Reactive (post-deployment) | Proactive (pre-deployment gates) |
| Visibility | Opaque; hard to track changes | Full transparency via Git history |
PaC doesn’t stop at deployment. Tools like admission controllers and runtime scanners ensure that manual changes in live environments don’t break governance rules [1]. This continuous approach transforms enforcement from a slow, manual process into an automated system that scales effortlessly with your infrastructure.
How Policy as Code Works
Policy as Code weaves governance into every stage of infrastructure provisioning. Using declarative languages like Rego (for Open Policy Agent), Sentinel (for HashiCorp tools), or JSON (for Azure Policy), policies describe the desired state of your infrastructure [1]. These policies then integrate into various checkpoints throughout the development lifecycle.
For example, during the planning phase in tools like Terraform, PaC evaluates proposed changes before anything is deployed. Pre-commit hooks catch issues directly in your IDE, while CI/CD pipelines serve as another safeguard during automated deployments. In Kubernetes environments, admission controllers act as gatekeepers, stopping non-compliant workloads before they’re deployed.
By identifying issues early, PaC minimises the effort needed to fix them. Runtime scanning keeps an eye on live environments, flagging any configuration drift. Every policy decision is logged, creating a complete audit trail that simplifies compliance reporting for regulations like GDPR or HIPAA [1].
Key Features of Policy as Code
Automation lies at the heart of Policy as Code. It replaces manual ticketing and approval workflows with instant validation that runs every time code is updated. This not only eliminates weeks-long delays but also reduces misconfigurations by up to 90% [1]. Centralising policies in Git provides a single source of truth, enabling pull request reviews, testing, and rollbacks with ease.
CI/CD integration allows developers to deploy infrastructure independently while staying within governance limits. They receive immediate feedback on violations, whether through their IDE, pull request comments, or pipeline error messages. This streamlined approach has been shown to boost developer productivity by 50%, turning security reviews that once took weeks into tasks completed in seconds [1].
Some advanced PaC frameworks even offer automated remediation, identifying and fixing violations without manual intervention. This is especially useful for managing costs - for instance, ensuring proper resource tagging for billing or blocking the use of expensive, unapproved instance types. Together, these features transform policy enforcement into a fast, agile process that keeps pace with modern development workflows.
Benefits of Policy as Code for Cloud Governance
Policy as Code transforms cloud governance by automating rule enforcement and embedding compliance checks directly into development workflows. For organisations in the UK, where regulatory frameworks like GDPR and ISO 27001 are critical, this approach provides automated safeguards that maintain compliance while keeping operations agile and efficient.
Automation and Reduced Manual Effort
One of the standout advantages of Policy as Code is how it simplifies and speeds up deployment processes. Traditional manual reviews can drag out deployment timelines, turning what could take hours into days or even weeks. This not only slows innovation but also frustrates development teams. Policy as Code changes the game by replacing these time-consuming reviews with automated checks that run in seconds.
Organisations adopting Policy as Code have reported security reviews being completed up to ten times faster [1]. Take MediaMarkt, for example. By enabling governance, security, and platform teams to write policies as code, developers now receive immediate feedback on compliance and cost implications [3]. This shift from manual gatekeeping to automated feedback loops eliminates bottlenecks while ensuring control remains intact. For UK organisations, this level of automation is especially crucial, as it ensures consistent enforcement of standards like ISO 27001 and PCI DSS, reducing the risk of human error and easing the workload on compliance teams.
Improved Compliance and Security
Policy as Code excels in creating consistency. Unlike manual processes, which often rely on informal practices and can result in inconsistent governance, codified policies ensure uniform application. This approach has been shown to reduce misconfigurations by as much as 90% [1]. Violations are detected early - whether during development, within CI/CD pipelines, or even before code is committed - allowing issues to be resolved quickly and cost-effectively.
A cloud architect at ADB described the value of this approach:
Sentinel is going to be that bouncer in a club that allows you to go in or out. For us, that gives us 100% confidence that anything provisioned by Terraform is following our security postures [3].
This automated consistency is a game-changer for UK organisations navigating strict regulations. Azure Policy, for instance, includes prebuilt definitions for ISO 27001, a standard widely used across both government and enterprise sectors [2]. Moreover, storing policies in Git ensures a fully automated audit trail - a clear, timestamped record of every policy change. This not only simplifies regulatory compliance but also significantly reduces the burden of manual audits.
| Governance Category | Automated Policy Example | UK Relevance/Standard |
|---|---|---|
| Regulatory | Sensitive data monitoring via Microsoft Purview | ISO 27001 / GDPR [2] |
| Security | Enforce EBS volume encryption | PCI DSS / Cyber Essentials [4] |
| Cost | Restrict expensive instance types (SKUs) | FinOps / Budgetary Control [2][3] |
| Operations | Require multi-zone redundancy | Business Continuity Standards [2] |
| Identity | Enforce MFA and Just-In-Time access | UK NCSC Guidelines [2] |
Cost Optimisation and Scalability
Beyond compliance and security, Policy as Code plays a key role in managing cloud costs. By enforcing tagging for cost allocation, limiting resource types, and automatically shutting down idle resources, organisations can keep their cloud spending under control [9].
Take Petco’s experience as an example. Their cloud architect highlighted the importance of guardrails:
You need resource guardrails in the cloud because you don't want your CFO coming down to your office saying,
Why did you deploy 50 R5.16XLs? We just missed our quarterly objectives because of your deployment.And this is a job for Sentinel [3].
Policy as Code ensures governance scales alongside infrastructure without needing additional staff. As organisations grow, automated policies maintain standards across thousands of resources [1][7]. Features like hierarchical inheritance models further simplify governance by automatically applying organisational standards to new subscriptions and resource groups [2].
Modern tools even integrate cost estimates directly into pull requests, giving engineers a clear view of the financial impact of their infrastructure changes before deployment [9][3]. This shift-left
approach to cost management helps prevent budget overruns by addressing potential issues early. By aligning cost controls with governance practices, organisations can achieve both operational efficiency and financial discipline.
For UK businesses looking to integrate Policy as Code into their cloud governance strategies, Hokstad Consulting offers expert guidance to optimise cloud infrastructure and manage costs effectively.
How Policy as Code Simplifies Cloud Governance: Step-by-Step
You can implement Policy as Code gradually, without disrupting your current infrastructure, making it easier to manage cloud governance.
Define Your Governance Policies
Start by documenting your existing manual processes, security assessments, compliance requirements (like GDPR or PCI-DSS), and operational challenges. This helps identify the policies that will have the greatest impact.
Group your policies into categories such as Security, Cost Optimisation, Compliance, and Operational Excellence. For organisations in the UK, it’s especially important to address data sovereignty to meet UK GDPR requirements.
Apply policies at a high level - for example, Management Groups in Azure or AWS Organisations - so that all workloads automatically inherit these standards. Initially, use a monitor-first
approach by deploying policies in an audit or disabled mode. This lets you assess their impact on your resources before shifting to a stricter deny
mode, minimising disruption for developers.
Translate these policies into code formats like JSON, YAML, or Rego to make them testable and reusable. Blocklists are often more effective than detailed allowlists, as they provide flexibility for innovation. Also, establish a tagging strategy early on, as many policies rely on tags for cost allocation and compliance tracking.
Once your policies are codified, the next step is choosing tools that integrate seamlessly with your cloud environment.
Choose the Right Tools and Frameworks
The tools you pick will depend on your cloud setup and existing systems. Open Policy Agent (OPA), an open-source engine from the CNCF, uses the Rego language and works across Kubernetes, CI/CD pipelines, and multiple cloud platforms. Its vendor-neutral design makes it ideal for multi-cloud environments.
For Azure users, Azure Policy integrates smoothly with GitHub and Azure DevOps, offering real-time enforcement at no extra cost to subscribers. AWS users have options like CloudFormation Guard for proactive template validation, AWS Config for detective controls, and Service Control Policies (SCPs) for preventive measures. If you’re working with Terraform, HashiCorp Sentinel integrates directly with Terraform Enterprise and Cloud.
For Infrastructure as Code (IaC) security, tools like Checkov, TFSec, and Terrascan specialise in detecting misconfigurations in Terraform or CloudFormation templates before deployment. Cloud Custodian, an open-source rules engine, can also scan infrastructure in real time and handle auto-remediation.
| Tool | Primary Use Case | Language | Cloud Provider |
|---|---|---|---|
| OPA | General-purpose / Multi-cloud | Rego | All / Kubernetes |
| Azure Policy | Native Azure Governance | JSON | Azure |
| CFN Guard | AWS IaC Validation | Guard | AWS |
| Sentinel | IaC Guardrails | Sentinel | Multi-cloud (via Terraform) |
| Checkov | IaC Security Scanning | Python/DSL | Multi-cloud |
Azure Policy, for instance, includes built-in compliance policies for standards like ISO 27001 and PCI DSSv4, which is particularly relevant for UK financial and public sector organisations. To maintain transparency and control, store your policy definitions in version-controlled repositories like GitHub or Azure DevOps. This practice facilitates auditing, rollbacks, and collaborative reviews.
After selecting the right tools, integrate your policy checks into CI/CD pipelines to ensure compliance throughout the development lifecycle.
Integrate Policies into CI/CD Pipelines
Embedding policy checks into your CI/CD pipelines allows you to catch misconfigurations early, following a shift-left
strategy that reduces costly fixes later. Tools like opa eval or cfn-guard validate can run these checks before provisioning resources.
Microsoft highlights the importance of this approach:
By making Azure Policy validation an early component of the build and deployment process, the application and operations teams discover if their changes are behaving as expected long before it's too late.
Adopt three types of controls:
- Proactive: Scan IaC templates before deployment.
- Preventative: Restrict actions using tools like SCPs or Azure Policy denies.
- Detective: Monitor deployed resources for drift.
For detective controls, consider automating fixes with serverless functions or tools like Cloud Custodian, which can correct non-compliant resources in real time.
Validate your policies with unit tests, using both compliant and non-compliant samples, before deploying them in production. Start with a few impactful, non-blocking policies - like auditing for publicly accessible S3 buckets - to build trust and confidence within your team. Over time, expand coverage and empower platform teams to enforce inherited policies while allowing workload teams to manage governance within their specific domains.
For UK organisations looking to streamline cloud governance, following these steps - along with expert advice from Hokstad Consulting (https://hokstadconsulting.com) - can lead to a more efficient and compliant infrastructure.
Need help optimizing your cloud costs?
Get expert advice on how to reduce your cloud expenses without sacrificing performance.
Common Challenges in Policy as Code Adoption
Tackling the hurdles of adopting Policy as Code is crucial for fully realising the potential of automated governance in today’s cloud ecosystems. Many organisations face resistance from teams used to manual processes, with some perceiving automation as a bottleneck to speed [10]. Skill gaps also pose a challenge, as teams often lack familiarity with policy languages like Rego or Sentinel and struggle to integrate these tools into CI/CD pipelines [7]. As policies grow in scope, they can become overly complex, harder to maintain, and may even impact system performance if not optimised [7].
Switching to code-driven enforcement can be bumpy, but the benefits are undeniable. Organisations have reported outcomes such as a 90% reduction in misconfigurations, 10x faster security reviews, and a 50% increase in developer efficiency [1]. These results highlight the importance of creating clear, structured, and manageable policy definitions.
Simplify Policy Definitions
Complexity is a common roadblock when scaling policies. A practical way to address this is by modularising rules and providing clear documentation that explains the purpose of each policy to all stakeholders [7]. Start with straightforward, impactful policies - like preventing public S3 buckets or enforcing resource tagging - before moving on to more intricate architectural rules [1]. When violations occur, ensure error messages are detailed and actionable, outlining both the issue and the steps to fix it. This approach is far more effective than generic responses like Access Denied
and empowers developers to resolve issues independently, reducing reliance on governance teams [1][9].
Build Team Buy-In and Collaboration
Resistance often stems from the perception that compliance slows down delivery. DevOps engineer Suvrajeet Banerjee explains:
If compliance is treated like a burden, it will always feel like an obstacle. However, when compliance is seen as part of quality, it becomes easier to adopt [10].
Involving engineering teams early in the policy development process fosters understanding and encourages collaboration. When teams grasp the reasoning behind controls, they are more likely to contribute to creating practical and effective rules [10]. Storing policies in Git, combined with branching, peer reviews, and version control, further strengthens collaboration between developers, security, and compliance teams [7]. Introducing graduated enforcement - starting with warnings before fully enforcing policies - gives teams the time they need to adapt without feeling overwhelmed [7][3].
Measure Success and Maintain Policy Governance
Rolling out Policy as Code is just the beginning; the real challenge lies in measuring its impact and ensuring policies stay relevant. Without proper metrics, it’s tough to justify the investment or pinpoint areas needing improvement. As CloudifyOps puts it, You can't manage what you can't measure.
By tracking the right indicators, you can showcase value to stakeholders and uncover opportunities to refine your approach.
Define Success Metrics
To gauge the effectiveness of governance, compliance metrics are a must. Keep an eye on the percentage of resources adhering to policy standards and track how quickly violations are resolved over time [8]. For example, aim for a 90% reduction in misconfigurations. Automation can also make a big difference here, delivering security reviews up to 10× faster and boosting developer productivity by as much as 50% [1].
Cost efficiency is another key area to monitor. Assess your overall cloud spend and unit costs to ensure they align with business growth [9]. With businesses potentially wasting around 28% of their public cloud budgets, identifying savings - like those from automatically shutting down idle resources - can make a significant impact. AWS users, for instance, could save up to 36% by optimising instance sizes. And with downtime costs ranging from £1 million to £5 million per hour, these metrics are critical for demonstrating the financial benefits of Policy as Code.
Ensure Continuous Policy Improvement
Defining success metrics is just the start; keeping your policies up to date is equally important. Policies need to evolve with your business and the ever-changing regulatory landscape. A good first step is adopting a monitor-first approach - deploy new rules in audit mode to observe their impact on workloads and weed out false positives before enforcing them [5][2]. Storing policies in Git can also help maintain traceability and improve collaboration across teams.
For high-priority violations, automation can handle remediation, cutting down on manual effort. Consider implementing tiered policies, where stricter controls apply to production environments while development environments offer more flexibility [9]. Regularly review audit logs from policy engines and CI/CD pipelines to spot recurring issues and fine-tune your rules.
Continuous monitoring and automated enforcement are essential for long-term success [6]. Think of Policy as Code as a living, breathing product - it should adapt to changes in cloud APIs, new regulations, and your business needs. Regular updates and refinements ensure it remains effective and aligned with your goals.
Conclusion
Policy as Code shifts cloud governance from manual oversight to proactive, automated enforcement. By turning governance rules into code, organisations can apply them consistently across all resources and cloud providers, eliminating the inconsistencies and human errors that often undermine traditional approaches.
This shift brings clear benefits in efficiency and compliance. Features like automated tagging enforcement and proactive cost controls provide the transparency needed to manage expenses while preserving the flexibility to innovate. These improvements highlight the strategic value of Policy as Code, with proven practices that can be tailored to suit any cloud environment.
Start with impactful policies - such as preventing public storage buckets or requiring cost-allocation tags - and test new rules in audit mode to evaluate their effects before moving to full enforcement[2][5]. Keeping all policies in version control not only creates clear audit trails but also promotes collaboration across teams. These small, deliberate steps lay the groundwork for advanced governance systems that can adapt and evolve.
Policy as Code enables self-healing systems that automatically fix violations and enforces standards through hierarchical inheritance models, making it easier to scale governance as your cloud environment grows. Treat your policies as dynamic tools that evolve with your business, regulatory demands, and cloud platform updates. For further guidance on implementing Policy as Code, reach out to Hokstad Consulting.
FAQs
How does Policy as Code make cloud governance more efficient?
Policy as Code streamlines cloud governance by automating rule enforcement, eliminating the need for error-prone manual checks. This method ensures that policies are applied consistently across all environments, making it easier to maintain compliance and scale operations effectively.
With version-controlled policies, organisations can track changes effortlessly, ensuring transparency and enabling swift adjustments to meet changing requirements. This approach not only speeds up compliance efforts but also reduces operational costs and simplifies management.
What are the best tools for implementing Policy as Code?
Policy as Code can be brought to life using tools that fit neatly into your CI/CD pipelines and version control systems, making policy enforcement an automated part of your workflow. Here are a few standout options:
- Open Policy Agent (OPA): This versatile, language-neutral engine relies on the Rego language to enforce policies. It’s especially effective for Kubernetes environments when paired with Gatekeeper, as it handles complex, cross-resource rules seamlessly.
- Kyverno: Designed specifically for Kubernetes, Kyverno uses YAML for policy creation, making it a straightforward choice for teams already working with Kubernetes manifests.
- Kubernetes Admission Controllers: These built-in hooks enforce basic guardrails within Kubernetes. While effective for simpler policies, they may not be the best fit for more intricate requirements.
For broader cloud ecosystems, tools like HashiCorp Sentinel (integrated with Terraform and other HashiCorp tools) and Cloud Custodian (which ensures continuous compliance for cloud resources) are widely used. Combining these tools can help ensure consistent governance across both development and operations.
If you’re looking for expert guidance, Hokstad Consulting can assist in choosing and integrating the right tools tailored to your UK-based cloud environment, ensuring efficient governance and compliance at every step.
How can organisations adopt Policy as Code for cloud governance?
Integrating Policy as Code into your workflows can simplify cloud governance by automating compliance checks and maintaining consistency across your processes. Here’s how you can get started:
Identify compliance needs: Start by pinpointing the regulations and internal standards your organisation must adhere to, such as GDPR or PCI DSS. Knowing these will guide your policy creation.
Select a policy engine: Choose a tool that fits your team's skills and environment. Popular options include Open Policy Agent (OPA), Kyverno, or Kubernetes Admission Controllers.
Define and test policies: Write rules in the chosen tool’s language - examples include setting resource limits or specifying approved registries. Test these policies thoroughly to catch and block non-compliant changes.
Integrate into CI/CD pipelines: Embed policy checks into your development workflows. This ensures that any non-compliant code is flagged and rejected before deployment.
Monitor and refine: Use continuous scanning to detect violations, keep track of policy changes with version control, and update your policies as compliance requirements evolve.
By weaving Policy as Code into your delivery pipeline, you can automate governance while maintaining the agility your team needs. For tailored solutions, Hokstad Consulting provides expert support to design and optimise these workflows for your cloud environment.
