Policy as Code (PaC) transforms cloud access control by automating policies as machine-readable code. This eliminates manual errors, speeds up deployment, and ensures compliance. Here’s why it matters:
- Automation: Reduces human errors by integrating policies into CI/CD pipelines.
- Real-Time Compliance: Automatically detects and addresses policy violations during development.
- Scalability: Simplifies managing access across multi-cloud environments.
- Centralised Control: Ensures consistent enforcement using tools like Open Policy Agent (OPA).
Benefits of Policy as Code in Cloud Access Control
Automation and Error Reduction
Relying on manual enforcement often means depending on undocumented tribal knowledge
, which can lead to inconsistent practices. When policies are confined to static documents, they’re open to interpretation, increasing the risk of errors. By transforming these policies into machine-readable code that integrates directly with CI/CD pipelines, Policy as Code eliminates ambiguity and reduces human mistakes. For instance, Wayfair has implemented advisory, soft-mandatory, and hard-mandatory policies to guide developers away from risky configurations. According to HashiCorp, this method allows organisations to confirm whether IT and business requirements are being met in mere seconds or minutes, compared to the weeks that manual reviews might take [1]. These automated processes enable continuous, real-time compliance checks, streamlining enforcement and reducing delays.
Real-Time Compliance and Auditing
With automation as its foundation, real-time compliance ensures that policy violations are caught and addressed immediately. Traditional compliance audits, often conducted quarterly or annually, can leave non-compliant resources in production for months. Policy as Code changes this by enabling near-continuous compliance. It scans infrastructure in real time, comparing it against established policies. Instead of manually sifting through regulatory documentation, organisations can encode standards like GDPR, HIPAA, or PCI DSS into declarative code that enforces compliance automatically. Moreover, Policy as Code tools generate detailed audit trails to ensure accountability. This proactive approach employs detective controls to spot non-compliant changes and responsive controls to trigger automated fixes. Many organisations start by automating policies for high-risk areas, such as unencrypted storage or publicly accessible buckets, and often utilise pre-built industry benchmarks like the CIS standards to simplify the process [5].
Scalability in RBAC and ABAC
As cloud environments grow, managing Role-Based Access Control (RBAC) and Attribute-Based Access Control (ABAC) manually becomes impractical. Policy as Code addresses this by separating policy decision-making from the underlying systems, offering a unified engine capable of handling complex authorisation across various cloud services [4]. Modern ABAC systems evaluate intricate data, such as user attributes, resource metadata, and environmental factors, and Policy as Code languages are designed to handle these complexities at scale. This approach also helps detect conflicting role assignments, ensuring a clear separation of duties that would be challenging to manage manually. By codifying RBAC and ABAC, organisations can maintain consistent access rules across multi-cloud and hybrid setups, reducing configuration drift. A phased rollout - starting with policies in advisory mode or disabled mode to test impact before full enforcement - is often recommended for a smoother transition [1][6].
Core Principles of Policy as Code
Policies as Versioned Code
When policies are treated like software, they are stored in version control systems like Git. This practice keeps a detailed record of every change, complete with timestamps and authorship. If something goes wrong, teams can quickly roll back to an earlier version. Version control also enables peer reviews, ensuring that changes are scrutinised by relevant teams before being implemented. This method moves away from informal, undocumented practices and ensures consistent application of access rules across development, staging, and production environments.
By replacing static documents with versioned code, policies become dynamic and easier to manage. Instead of relying on outdated PDFs or Word files, organisations maintain an auditable, unchanging record of rules and their history. This approach simplifies compliance audits, provides clear accountability for changes, and ensures policies remain up to date.
Integration with CI/CD Pipelines
Versioned policies become even more effective when integrated into CI/CD pipelines. By embedding policy checks into these automated workflows, security and compliance violations can be detected before infrastructure is deployed. This shift-left
strategy allows developers to identify policy conflicts within seconds or minutes, rather than waiting for lengthy manual reviews that could take weeks. Automated validation occurs every time code is committed, ensuring policies are tested alongside the application code itself.
Replacing manual ticketing and approval processes with automated checks removes bottlenecks that often delay deployments. Teams receive instant feedback, enabling them to address issues early in the development process. This not only reduces the stress of deployment but also ensures that policies function correctly before reaching production, maintaining a strong security framework.
Centralised Policy Management
Centralising policy enforcement takes automation a step further by simplifying decision-making across the technology stack. Tools like Open Policy Agent (OPA), a project under the Cloud Native Computing Foundation, provide a unified policy engine. This engine ensures consistent rule management across different layers, including Kubernetes, CI/CD systems, and cloud environments. By separating policy decision-making from enforcement logic, it prevents access rules from being scattered across application code. Systems send structured data - usually in JSON format - to the central engine to receive clear allow
or deny
responses.
OPA decouples policy decision-making from policy enforcement. When your software needs to make policy decisions it queries OPA and supplies structured data (e.g., JSON) as input.– Open Policy Agent [4]
With centralised management, policies are applied uniformly, no matter where resources are deployed. Because the same policy code produces identical results every time it's run, teams can trust that access controls remain consistent and reliable across their entire cloud infrastructure. This predictability is key to maintaining a secure and well-organised environment.
Deploying Policy-as-Code with Readable Rego Policies, and Open Policy Agent - Peter O'Neill, Styra
Need help optimizing your cloud costs?
Get expert advice on how to reduce your cloud expenses without sacrificing performance.
How to Implement Policy as Code for Cloud Access Control
::: @figure 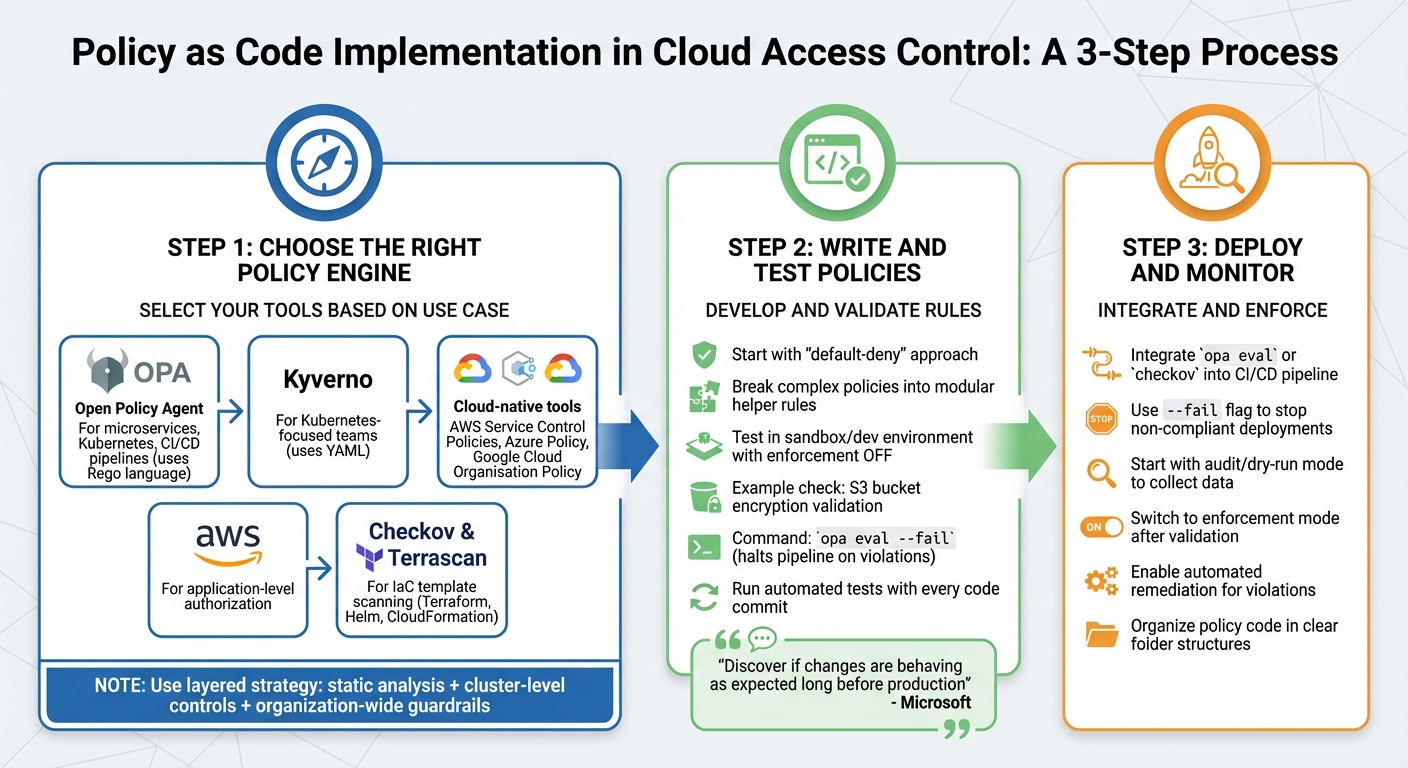 {Policy as Code Implementation Process for Cloud Access Control}
:::
{Policy as Code Implementation Process for Cloud Access Control}
:::
Turning a strategy into action requires effectively implementing policies as code.
Choosing the Right Policy Engine
The choice of a policy engine depends on your enforcement needs and the expertise of your team. Open Policy Agent (OPA), a project under the Cloud Native Computing Foundation, is a versatile engine that integrates with microservices, Kubernetes, and CI/CD pipelines [4][11]. It uses Rego, a policy language, to evaluate JSON data and delivers straightforward allow
or deny
decisions. If your organisation is primarily focused on Kubernetes, Kyverno might be a better fit. It uses YAML, which is more familiar to teams working with Kubernetes manifests, making it easier to adopt [10].
Cloud providers also offer built-in tools, such as AWS Service Control Policies, Azure Policy, and Google Cloud Organisation Policy, to enforce governance at the account level [10][7]. For application-level authorisation, AWS Cedar offers fine-grained, context-aware access control that operates independently of your application's codebase [10]. Additionally, tools like Checkov and Terrascan are designed to scan Infrastructure as Code templates, such as Terraform, Helm, or CloudFormation files, for misconfigurations before deployment [10][5]. A layered strategy - combining static analysis during CI/CD with cluster-level admission controls and organisation-wide guardrails - ensures a more secure setup [10][5].
Once you've chosen your engine, the next step is to develop and test clear policies with a default-deny
approach.
Writing and Testing Policies
Start with a default-deny
policy that only grants access when specific conditions are met [9]. This approach minimises the risk of unintentional over-permissioning. When crafting complex Rego policies, consider breaking them down into smaller, modular helper rules
to make them easier to read and manage [9]. For instance, a policy for ensuring S3 bucket encryption might scan Terraform plans to find aws_s3_bucket resources missing the server_side_encryption_configuration block. If an unencrypted bucket is detected, the CI/CD pipeline can run opa eval --fail, halting the deployment and displaying an error message like: S3 bucket \[name\] must have server-side encryption enabled
[9].
Testing policies should begin in a sandbox or development environment with enforcement turned off. This lets you audit compliance and fine-tune rules without disrupting resource creation [6][10]. Microsoft advises this phased approach:
By making Azure Policy validation an early component of the build and deployment process, the application and operations teams discover if their changes are behaving as expected long before it's too late and they're attempting to deploy in production[6].
Automated tests should run with every code commit, ensuring that policies are validated alongside the application itself before reaching production.
Once policies are thoroughly tested, they can be deployed and monitored to maintain continuous compliance.
Deployment and Monitoring
Integrate tools like opa eval or checkov into your CI/CD pipeline [4][5]. Use the --fail flag to exit with a non-zero code when a policy query fails, effectively stopping the pipeline and preventing non-compliant resources from being created [6][5]. Organise your policy code into clear folder structures, including versions, parameters, and rules, to keep your library manageable as it grows [6].
Start with an audit or dry-run mode to collect compliance data without causing disruptions [6][10]. Once you're confident in the rules, switch to enforcement mode to automatically block violations. Some policies even support automated remediation - for example, encrypting an unencrypted volume immediately upon detection - allowing you to correct non-compliant resources without manual intervention [5][6].
Advanced Use Cases and Best Practices
Expanding on the core advantages of Policy as Code, its advanced applications can streamline multi-cloud operations, optimise costs, and strengthen compliance efforts.
Multi-Cloud and Hybrid Cloud Access Control
Managing access across platforms like AWS, Azure, and GCP can quickly become chaotic without a unified system. Instead of relying on each provider's individual tools, use cloud-agnostic Infrastructure as Code (IaC) tools like Terraform alongside universal policy engines like Open Policy Agent (OPA). This allows you to create a single governance framework. For instance, rather than crafting separate rules for AWS S3, Azure Storage, and GCP Buckets, you can build a policy abstraction layer - a unified storage
policy that smooths out the differences between these platforms [12].
Setting up a Cloud Centre of Excellence (CCoE) is another key step. This team oversees governance and ensures tools don't spiral out of control [12]. Apply universal tagging rules - like requiring owner and cost-centre tags - so policies can consistently identify and manage resources across all clouds [12]. Pair preventive measures, such as incorporating OPA into CI/CD pipelines, with detective controls like Cloud Custodian, which can scan for issues and automatically correct configuration drift in real time [5].
To prevent the chaos of role proliferation in multi-cloud setups, adopt Attribute-Based Access Control (ABAC). This method dynamically grants permissions based on tags assigned to both users and resources [13]. Reinforce Zero Trust principles by validating user authentication, device compliance, and network conditions across all cloud environments [14]. Additionally, segment production virtual networks into at least three subnets to maintain clear security boundaries [14]. These practices integrate seamlessly with the foundational principles discussed earlier, extending them into diverse cloud environments.
Cost-Effective Access Policies
Policy as Code doesn't just enhance security - it can also lower cloud expenses. By using ABAC to allocate permissions based on tags, you can simplify role management and reduce administrative overhead [13]. Start with broad controls like Service Control Policies (SCPs) and account-level boundaries before moving to more detailed identity policies, which helps manage complexity at scale.
Providing pre-approved Terraform modules with built-in security measures can help avoid costly misconfigurations [12]. For minor issues, such as a missing cost-centre tag, automate fixes to save time and effort [12]. Limit high-privilege IAM sessions to one hour to minimise security risks [14], and deactivate or remove IAM users who haven't been active for over 90 days [14]. These cost-saving strategies complement the security enhancements discussed earlier.
Compliance with Regulatory Standards
Policy as Code also plays a crucial role in meeting regulatory requirements. Automating evidence collection for audits ensures logs are tamper-proof and meet retention mandates, such as keeping records for 365 days [14]. Enforcing strong password policies - requiring at least 14 characters - further enhances compliance in cloud environments [14].
Transition from outdated IAM users to Identity Centre models (SAML/OIDC) managed by a corporate Identity Provider (IdP). This modern approach is not only scalable but also more auditable compared to using individual users with long-lived keys [13]. Permissions boundaries can also be used to define the maximum permissions an identity-based policy can grant, creating a sandbox
environment where developers can safely experiment without risking privilege escalation [13][15].
For continuous compliance monitoring, adopt a multi-layered validation strategy: evaluate policies during IaC linting, enforce checks at the CI/CD pipeline stage, and continuously monitor the live environment to detect and address drift [6]. This ensures compliance is not just a one-time effort but an ongoing process.
Conclusion
The discussion above has shown how Policy as Code simplifies security, compliance, and cost management in cloud environments.
Key Takeaways
Policy as Code shifts cloud access control from a manual, error-prone process to an automated system operating at machine speed. By codifying policies, it eliminates human inconsistencies and ensures compliance through CI/CD preventive controls and real-time scanning [3][5]. The shift-left
approach catches security issues during development, significantly reducing vulnerabilities before they ever reach production [2].
Scalability is another major advantage. Manual reviews quickly become unmanageable when dealing with thousands of resources across multiple cloud providers. Policy as Code enforces consistent standards, whether you're managing three accounts or three hundred [2][3]. This efficiency eliminates the need for lengthy approval cycles, replacing them with instant feedback, allowing developers to work faster without compromising security.
Cost management is also a key benefit. Automated resource guardrails prevent unexpected expenses, such as deploying costly instances by mistake. Tools like version control, automated testing, and centralised policy management provide a single source of truth, simplifying governance across teams and offering clear audit trails for compliance [8][1].
How Hokstad Consulting Can Help

Implementing Policy as Code effectively calls for expertise in DevOps transformation and cloud infrastructure optimisation - areas where Hokstad Consulting excels. Their services include custom development and automation, integrating policy engines directly into existing CI/CD pipelines to ensure security checks are automatic during deployment. With experience across public, private, hybrid, and managed hosting environments, they create tailored solutions that fit your specific cloud setup.
Hokstad Consulting also offers cloud cost engineering services that align seamlessly with Policy as Code. Their approach can reduce expenses by 30–50% using automated resource guardrails and usage policies. Additionally, they provide ongoing DevOps support, including infrastructure monitoring and security audits, ensuring your policies stay effective as your environment evolves. Whether you're starting with basic tagging rules or building a robust multi-cloud governance framework, their expertise in strategic cloud migration and AI-driven automation can accelerate your Policy as Code adoption - all while maintaining zero downtime.
FAQs
How does Policy as Code enhance security and compliance in cloud environments?
Policy as Code is all about turning security and compliance rules into machine-readable code. This allows for automated enforcement across cloud systems, cutting down on the need for manual checks, reducing mistakes, and ensuring that least-privilege principles and regulatory standards are applied consistently.
With automated policy validation and remediation, organisations can simplify compliance workflows, strengthen their security measures, and lower the chances of human error. This method not only makes cloud governance easier to manage but also helps businesses scale and adjust effortlessly in ever-changing cloud environments.
What are the best tools for implementing Policy as Code in cloud environments?
Several tools are commonly used to implement Policy as Code in cloud environments, making it easier to manage access control and maintain compliance:
- Open Policy Agent (OPA): This open-source policy engine uses the Rego language to enforce policies across platforms like Kubernetes, CI/CD pipelines, and APIs.
- Pulumi Policies: These let you define policies using familiar programming languages, working seamlessly with tools like Pulumi, Terraform, and CloudFormation.
- Cloud Custodian: A rule-based engine designed for continuous resource scanning and automated remediation. It's often paired with OPA for real-time compliance checks.
- Azure Policy as Code: Offers the ability to manage policies in JSON or YAML, store them in Git for version control, and apply them through Azure Pipelines to ensure ongoing compliance.
- AWS Config: Monitors resource configurations and evaluates them against custom rules. It's commonly used alongside tools like OPA or Cloud Custodian for more extensive governance.
These tools cater to a variety of needs, from open-source options to cloud-native services, allowing you to codify, version-control, and automate policy enforcement across different cloud platforms.
How does Policy as Code help lower cloud management costs?
Policy as Code helps cut down cloud management expenses by automating cost-saving practices and reducing resource wastage. It enforces rules such as mandatory tagging, blocking the use of oversized instance types, and spotting unused resources, ensuring these measures are applied consistently.
By removing the need for manual oversight and lowering the chances of mistakes, this method simplifies governance. It also helps avoid avoidable costs, freeing up teams to concentrate on more impactful and strategic tasks.
