Micro-segmentation is a security method that isolates workloads within hybrid cloud environments using detailed, identity-based policies. Unlike traditional methods relying on static IPs and firewalls, it secures internal traffic (east-west
) by creating smaller, isolated zones. This approach aligns with the Zero Trust model, reducing the risk of lateral attacks and improving security across dynamic, multi-cloud infrastructures.
Hybrid cloud environments, combining on-premises and public cloud resources, face challenges like visibility gaps, inconsistent security tools, and vulnerabilities to lateral attacks. Micro-segmentation addresses these issues by enforcing granular controls and ensuring policies follow workloads as they move between environments.
Core Strategies:
- Host-Based Micro-Segmentation: Uses agents on hosts to enforce security at the process level, offering detailed visibility but requiring agent installation.
- Network-Based Micro-Segmentation: Relies on network tools (e.g., SDN, VLANs) for unmanaged devices but struggles with dynamic configurations.
- Cloud-Native Approaches: Utilises metadata and tags for policy enforcement, ideal for containers and Kubernetes but dependent on platform-specific tools.
Key Takeaways:
- Hybrid cloud security improves with micro-segmentation by limiting attack surfaces and preventing lateral movement.
- Combining host-based, network-based, and cloud-native methods creates a flexible, tailored security framework.
- Start small, focusing on critical assets, and gradually expand segmentation efforts while maintaining a unified management interface.
By implementing micro-segmentation, organisations can better secure hybrid cloud environments, protect sensitive data, and align with modern security standards like Zero Trust.
Cloud Agnostic Micro-Segmentation Approach using Open-Source Tools for a Zero Trust Foundation
Core Micro-Segmentation Strategies for Hybrid Cloud
::: @figure 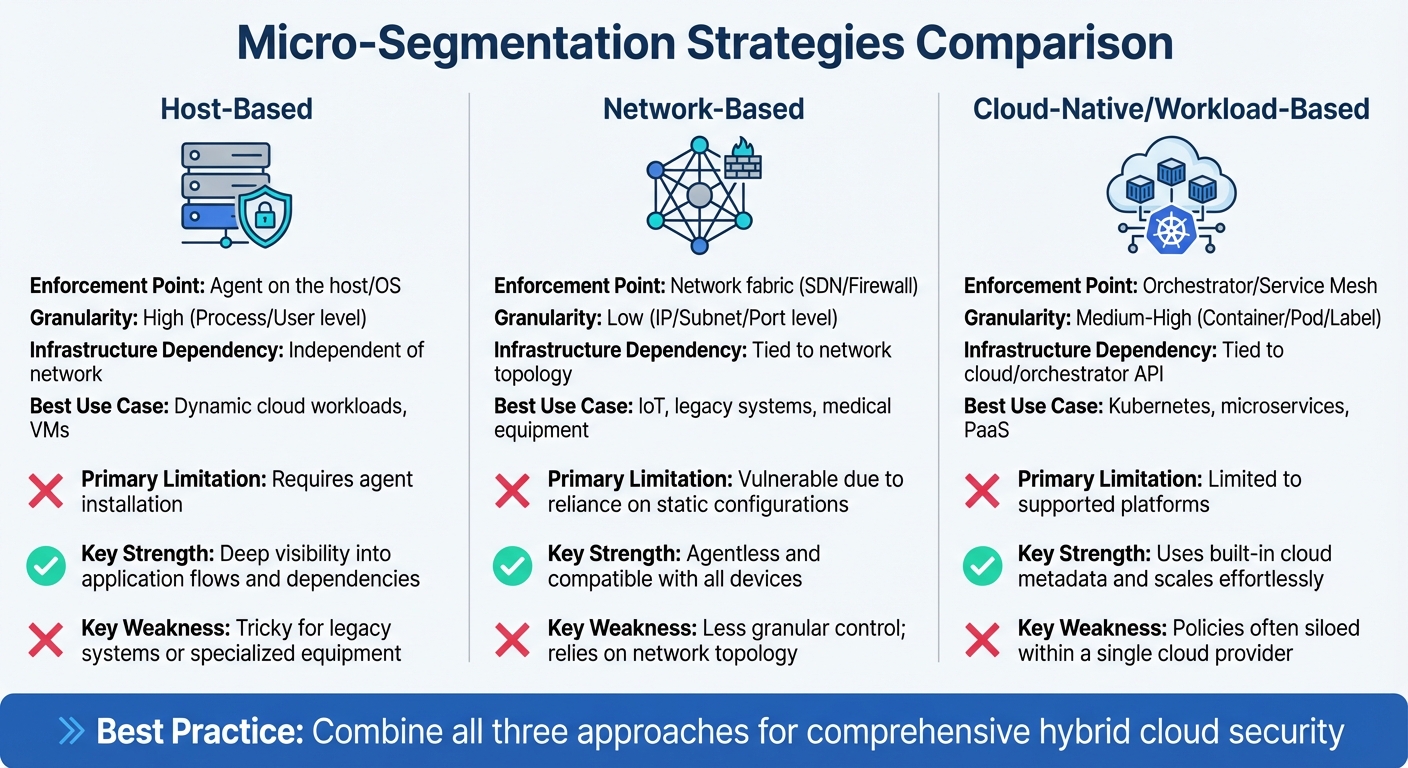 {Comparison of Micro-Segmentation Strategies for Hybrid Cloud Security}
:::
{Comparison of Micro-Segmentation Strategies for Hybrid Cloud Security}
:::
The strategies below address various aspects of micro-segmentation tailored for hybrid cloud environments.
Host-Based Micro-Segmentation
Host-based micro-segmentation uses agents to manage host-level firewalls, like iptables on Linux or Windows Firewall, to establish secure boundaries even at the process level [1][6][7]. One major benefit of this approach is its deep visibility into application flows and dependencies. Unlike network-based tools that only track IP addresses and ports, host-based agents can identify which applications are communicating and understand the reasons behind it [6][7]. This method operates independently of the network's structure, ensuring consistent security policies even when workloads shift across environments.
Host-based microsegmentation and network-level segmentation can and should co-exist, since they each address a different requirement.
– Christer Swartz, Solutions Marketing Director, Illumio [6]
However, this approach requires installing an agent on every host - something that can be tricky for legacy systems or specialised equipment.
Network-Based Micro-Segmentation
This method enforces security at the network layer using tools like Software-Defined Networking (SDN), Virtual LANs (VLANs), and Access Control Lists (ACLs) [6][1]. It’s particularly suited for assets that can’t support agent installation, such as IoT devices, medical equipment, or legacy systems [3].
A limitation of network-based segmentation is its reliance on static configurations, like IP addresses, ports, and protocols, which can be challenging in dynamic hybrid cloud setups [3][7]. For example, setting up 1,000 individual network segments for 1,000 hosts using tools like Cisco ACI EPGs can become impractical [6].
SDN controllers view hosts in the traditional manner, as nodes that attach to the network fabric, and applications running on those hosts are managed using host-centric tools, not network-centric tools.
– Christer Swartz, Solutions Marketing Director, Illumio [6]
Overlay networks like VXLAN offer over 16 million unique IDs, but SDN controllers typically focus on addressing networking issues, such as Layer-2 encapsulation, rather than creating granular segments for individual hosts [6]. While network-based tools excel in monitoring metrics like load, latency, and connectivity issues, host-based tools are better suited for understanding application behaviour and workload-specific needs [6].
Cloud-Native and Workload-Based Approaches
Cloud-native micro-segmentation takes a different route by using metadata, such as tags and labels, to define security policies instead of relying on the network's structure [1][3]. For instance, in Kubernetes environments, you might label pods as production
or PCI-regulated
, and policies will automatically apply based on these attributes, no matter where the workload is running [3].
This method focuses on workload identity rather than IP addresses, ensuring that security rules remain effective even as workloads shift. It aligns with the Zero Trust model, where every connection request is authenticated and authorised at the time of access, regardless of the network location [7][8].
Cloud-native strategies are ideal for containers, Kubernetes clusters, and microservices architectures, but they depend on specific orchestrator APIs or cloud platforms. This means their effectiveness is tied to the platforms your organisation uses [3].
Comparison of Micro-Segmentation Strategies
| Feature | Host-Based | Network-Based | Cloud-Native/Workload-Based |
|---|---|---|---|
| Enforcement Point | Agent on the host/OS | Network fabric (SDN/Firewall) | Orchestrator/Service Mesh |
| Granularity | High (Process/User level) | Low (IP/Subnet/Port level) | Medium-High (Container/Pod/Label) |
| Infrastructure Dependency | Independent of network | Tied to network topology | Tied to cloud/orchestrator API |
| Best Use Case | Dynamic cloud workloads, VMs | IoT, legacy systems, medical equipment | Kubernetes, microservices, PaaS |
| Primary Limitation | Requires agent installation | Vulnerable due to reliance on static configurations | Limited to supported platforms |
Together, these strategies create a flexible and secure framework for managing the complexities of hybrid cloud environments. Each method has its strengths and challenges, making it essential to choose the right approach based on your organisation's needs.
Combining Multiple Micro-Segmentation Approaches
Enterprise environments are rarely uniform. Different assets demand different security measures: legacy systems and specialised devices often rely on network-based controls, while dynamic cloud workloads benefit from cloud-native enforcement methods [3].
Comparing Micro-Segmentation Methods
A unified strategy brings together host-based agents for detailed server and VM security, network-based controls for unmanaged devices, and cloud-native (agentless) enforcement for Platform-as-a-Service (PaaS) resources [2]. Modern solutions function as overlays, enabling organisations to define a single security intent that adapts dynamically across hybrid environments using the appropriate enforcement mechanism.
| Method | Strengths | Weaknesses | Best Use Case in Hybrid Cloud |
|---|---|---|---|
| Host-Based | Offers fine-grained control and visibility into east-west traffic at the process level [3][5] | Requires agent installation and management; unsuitable for IoT or legacy systems [3] | Best for securing VMs and servers in any environment |
| Network-Based | Agentless and compatible with all devices, including IoT and medical equipment [3] | Provides less granular control; relies on network topology [3] | Ideal for legacy hardware and unmanaged devices |
| Cloud-Native | Uses built-in cloud metadata and scales effortlessly with workloads [2][5] | Policies are often siloed within a single cloud provider [2] | Perfect for cloud-only workloads, but needs third-party tools for hybrid environments |
This comparison highlights the importance of blending these methods to create a tailored security approach that fits your organisation's needs.
Choosing the Right Approach for Your Organisation
To secure assets effectively in a hybrid cloud, organisations must integrate these methods into a unified strategy. Hybrid clouds, with their mix of dynamic workloads and diverse devices, benefit from a single dashboard that consolidates flow logs and metadata across hyperscalers and on-premises systems [2]. Without such integration, policy creation risks breaking critical application dependencies. Modern platforms leverage hybrid enforcement engines to dynamically switch between agent-based enforcement (for VMs and legacy servers) and agentless enforcement (for PaaS and cloud-native resources), depending on the asset type [2].
Start by mapping your critical assets to ensure a smooth and secure cloud migration [2]. Use AI-driven recommendations to analyse traffic flows and automatically suggest segmentation groups, simplifying the process of managing policies in hybrid environments [5]. Tag workloads by application type (e.g., PCI-regulated
) to ensure consistent policies across all environments [3][5].
Moving from IP-based rules to identity-centric policies is another key step. This method uses cloud metadata, user-defined tags, and JSON web tokens (JWT) to identify workloads across different environments [5]. For network-based segments, deploy Segment Connectors (Direct or SNAT) to enable controlled communication between isolated environments, such as Production and Shared Services [9].
A primary goal of Zero Trust is to minimise the attack surface - and microsegmentation is key to achieving this.
– Jacob Abrams, Product Marketing Manager, Akamai [2]
Achieving success requires collaboration. While networking and security teams typically lead the effort, application owners play a crucial role in ensuring business processes remain uninterrupted [3]. As of November 2024, platforms like Akamai Guardicore have introduced agentless policy enforcement for PaaS resources in both Azure and AWS, addressing a critical gap in hybrid cloud security [2].
Implementation and Best Practices
How to Implement Micro-Segmentation
To put micro-segmentation into action, a phased and organised approach is key. Start by automating the discovery process to map all connections and dependencies - both for east-west (internal) and north-south (external) traffic. This visibility ensures that critical business functions aren't disrupted when security policies are applied [2].
Next, divide your environment into logical segments. Instead of relying on static IP addresses, base these segments on attributes like application characteristics, user roles, or identity tags. Deploy appropriate security controls, such as firewalls, software-defined networking (SDN), or host-based agents, to manage traffic between segments. Before enforcing these policies, simulate them against real traffic patterns to identify potential issues [1].
It's wise to follow a crawl-walk-run
strategy: begin with high-priority assets, like production servers, and gradually expand segmentation efforts [3][1]. Gaining executive support early is crucial to secure funding and encourage collaboration across departments. As Erez Tadmor from Tufin points out:
Previously, security teams had problems getting support to implement micro-segmentation because there were no direct benefits to the business. Today, thanks to new mandates for zero trust architectures... there's a greater sense of urgency[3]
Once implementation starts, being aware of and addressing common mistakes is vital for maintaining an effective security system.
Common Mistakes and How to Avoid Them
One major misstep is trying to segment the entire network at once, which often results in unnecessary complexity [3]. Another common error is neglecting to involve application owners. While networking and security teams usually lead the process, application owners are key to understanding which traffic flows are essential for business operations [3].
Fragmented policy management across multiple cloud environments can also cause misconfigurations and uneven security. As Jacob Abrams from Akamai highlights:
Without unified visibility, it is very difficult to build and apply policy that protects those components without breaking something critical[2]
To avoid this, select tools that provide a single interface for managing hybrid cloud environments. Use application-centric labelling and identity-based tags so that policies can move seamlessly with workloads across environments [1][2]. After refining and validating policies, regular maintenance is essential to keep up with new threats.
Maintaining Micro-Segmentation Over Time
Keeping micro-segmentation effective requires ongoing effort. Conduct regular audits to ensure policies stay aligned with both emerging threats and changing business requirements [4]. Transition from network topology-based rules to identity-driven policies using metadata and tags. This allows security measures to adapt automatically as workloads shift between on-premises and cloud environments [1][3].
Automating asset discovery is another critical step. Continuously map application dependencies and traffic flows to ensure policies remain accurate as your infrastructure evolves [4]. Consistent tagging across all assets helps coordinate policies, especially for applications subject to regulations like PCI-DSS compliance [3]. Modern cloud-native systems can enforce policy changes in milliseconds, a stark contrast to legacy tools that require hours [1].
Finally, adopt a deny-all
default policy and gradually add permissions as verified communication needs arise. This approach ensures a least-privilege access model, strengthening overall security [1].
Conclusion
The strategies outlined here highlight practical ways to enhance hybrid cloud security and safeguard your organisation's critical assets.
Main Benefits of Micro-Segmentation
Micro-segmentation strengthens security in hybrid cloud setups by minimising the attack surface and stopping lateral movement within networks. It aligns with Zero Trust principles, requiring verification and authentication for every interaction [2] [4].
It also provides a unified view across multi-cloud and on-premises environments, simplifying policy enforcement. Organisations can better meet regulatory standards by isolating sensitive data as per industry requirements [4]. In the event of a breach, containment becomes more efficient - security teams can isolate affected zones without impacting unrelated systems [4].
These advantages form the foundation for actionable steps to secure your organisation's infrastructure.
Next Steps for Your Organisation
Start by identifying your most critical assets that need immediate protection during cloud migration [2]. Use automated tools to map out all communicating components and dependencies before defining segments [4]. Ensure these efforts align with your Zero Trust strategy for consistent security across all environments.
Opt for a solution with a unified management interface that spans your hybrid infrastructure, and focus on identity-based policies rather than static IP rules [2] [4]. Begin with high-priority assets and expand segmentation gradually, using a phased approach [1] [3]. For tailored guidance on implementing micro-segmentation and optimising your cloud infrastructure, Hokstad Consulting offers expert DevOps transformation and security services to help reduce costs while boosting protection across hybrid environments.
FAQs
How is micro-segmentation different from traditional firewalls?
Micro-segmentation establishes secure zones to isolate application workloads, limiting east-west traffic by applying a zero-trust model. This approach helps minimise attack surfaces and prevents threats from moving laterally within a network. Unlike traditional firewalls, which primarily focus on perimeter security, micro-segmentation offers the detailed workload isolation that hybrid cloud environments demand.
Which micro-segmentation approach fits my hybrid cloud best?
The ideal micro-segmentation strategy hinges on your specific security requirements, the complexity of your operations, and the structure of your infrastructure. A Zero Trust model stands out as a strong option, as it enforces strict access controls and continuous verification, which helps limit lateral movement and keeps workloads isolated. Alternatively, pairing workload-based segmentation with application-level controls can strengthen both security and compliance measures. These approaches help create a secure, adaptable, and efficient hybrid cloud environment.
How can I start micro-segmentation without disrupting applications?
To implement micro-segmentation smoothly, a well-thought-out plan is essential. Start by evaluating the dependencies between applications and setting up security policies that won't interfere with operations, such as using monitoring modes initially. Before rolling out changes in production, test these policies in a staging environment to identify any issues.
Leverage automated tools to analyse traffic patterns, which can help in applying policies step by step. Monitor the impact of each change closely and adjust as needed to maintain stability. A gradual approach ensures that your applications stay fully functional throughout the transition.
