IAM compliance is more critical than ever in 2025. With data breaches costing an average of $10.22 million and vulnerability exploits up by 34%, strong Identity and Access Management (IAM) systems are essential. Compliance isn’t just about meeting regulations like PCI DSS v4.0.1, GDPR, or ISO 27001 - it’s about protecting your organisation from costly fines (up to £80,000/month for PCI DSS violations) and strengthening security.
Key Takeaways:
- Regulatory Deadlines: PCI DSS v4.0.1 compliance is mandatory by 31 March 2025. Updates include stricter MFA requirements and 12-character password rules.
- IAM Priorities:
- Automate provisioning and de-provisioning to eliminate risks like orphaned accounts.
- Strengthen authentication with MFA, SSO, and conditional access policies.
- Regularly review access permissions and enforce least privilege principles.
- Maintain detailed audit trails and centralised logging to meet compliance requirements.
- Penetration Testing: Now required annually and after major changes by frameworks like PCI DSS, GDPR, and ISO 27001. Testing validates security controls and identifies vulnerabilities.
Actionable Steps:
- Define clear IAM policies and enforce role-based access controls.
- Automate identity lifecycle management to prevent privilege misuse.
- Conduct regular penetration tests to validate compliance and security.
- Use tools like AWS CloudTrail, IAM Policy Simulator, and SIEM systems for monitoring and reporting.
Remote work password security checklist | 7 essential controls
IAM Compliance Checklist for 2025
::: @figure 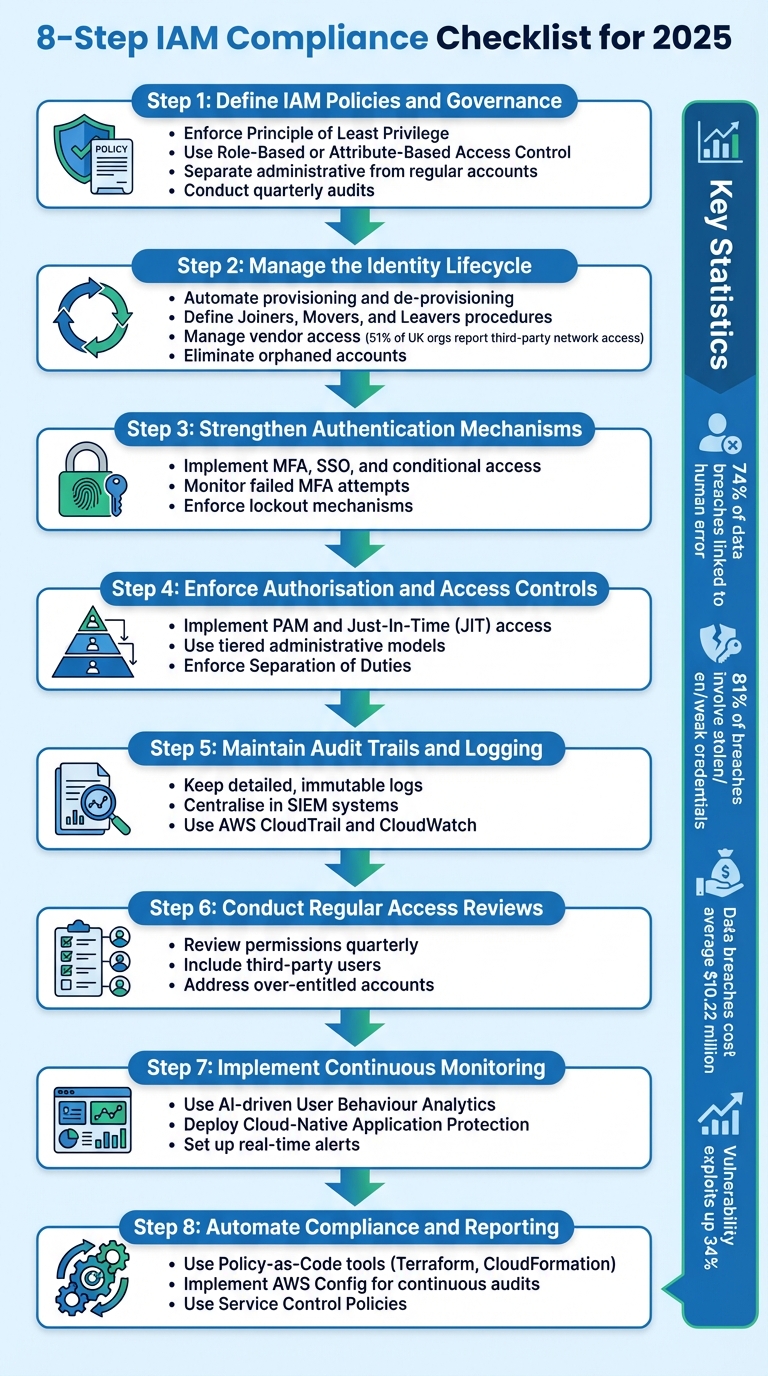 {8-Step IAM Compliance Checklist for 2025}
:::
{8-Step IAM Compliance Checklist for 2025}
:::
To protect your organisation and meet compliance standards in 2025, use this checklist to strengthen your Identity and Access Management (IAM) processes. With 74% of data breaches linked to human error, privilege misuse, or social engineering [8], and 81% of breaches involving stolen or weak credentials [10], robust IAM practices are critical. Start by establishing clear policies to lay the foundation for secure access management.
1. Define IAM Policies and Governance
Develop IAM policies that clearly outline who has access, under what conditions, and for what purposes. These policies should apply to all users - whether they are employees, contractors, volunteers, or third-party visitors - and enforce the Principle of Least Privilege using Role-Based or Attribute-Based Access Control. A default deny
approach should be the standard, allowing access only to authorised IP ranges and specific permissions.
Separate administrative accounts from regular business accounts to minimise risks like spear-phishing or lateral movement. For sensitive operations, implement Separation of Duties so no single person has full control over critical processes. Conduct quarterly audits to identify and address over-entitled accounts [9].
Penetration testing can validate these policies by attempting to bypass controls, ensuring that lower-privilege users cannot access restricted areas. This testing also checks compliance with PCI DSS v4.0 and GDPR Article 32 by verifying that access controls are enforced at the server level.
2. Manage the Identity Lifecycle
Automate processes like provisioning, de-provisioning, and off-boarding to eliminate orphaned accounts. Define clear Joiners, Movers, and Leavers
procedures to ensure access rights are updated or revoked immediately as roles change or employment ends. With 51% of UK organisations reporting third-party network access in 2024 [8], managing vendor access effectively is more important than ever. Require vendors to provide certifications and compliance reports before granting access, and enforce Non-Disclosure Agreements alongside strict termination procedures for external users.
Penetration testing can uncover inactive or orphaned accounts and verify that unauthorised users cannot exploit provisioning systems to re-enable deactivated accounts.
3. Strengthen Authentication Mechanisms
Implement Multi-Factor Authentication (MFA), Single Sign-On (SSO), and conditional access policies that factor in location or device health. Monitor failed MFA attempts and ensure lockout mechanisms are resistant to brute-force attacks.
Penetration tests can simulate phishing, password spraying, and brute-force attacks to measure the resilience of your authentication systems. These tests also assess risks like account enumeration, ensuring error messages or system responses don’t inadvertently reveal valid account information or allow impersonation.
4. Enforce Authorisation and Access Controls
Introduce Privileged Access Management (PAM) and Just-In-Time (JIT) access to grant elevated privileges only when absolutely necessary. Use tiered administrative models to separate privileged accounts from standard accounts, and enforce Separation of Duties to prevent any single individual from having unchecked control over critical systems.
Penetration testing can identify privilege escalation vulnerabilities by attempting to access admin-only functionality using low-privilege accounts. It also evaluates lateral movement risks by simulating credential theft, ensuring compliance with ISO 27001 standards.
5. Maintain Audit Trails and Logging
Keep detailed, immutable logs of all authentication and authorisation events. Centralise these logs in a Security Information and Event Management (SIEM) system for streamlined compliance reporting. Tools like AWS CloudTrail and CloudWatch can help ensure logs are preserved and accessible.
Penetration testing can evaluate the integrity of your logging systems by attempting to alter or delete records. It also verifies that critical events - such as root account usage or changes to MFA devices and IAM policies - are logged and flagged for review.
6. Conduct Regular Access Reviews
Review access permissions regularly, including those for third-party users, to ensure they align with current roles and responsibilities. This step is essential to address vendor access concerns highlighted earlier.
Penetration tests can simulate insider or vendor threats by auditing access logs and testing third-party access points. These tests help identify over-entitled accounts so they can be promptly corrected.
7. Implement Continuous Monitoring and Risk Assessment
Leverage AI-driven tools, such as User Behaviour Analytics, to detect unusual access patterns more efficiently than manual reviews. Use Cloud-Native Application Protection Platforms to automate responses, and set up CloudWatch Alarms and Event Rules to monitor unauthorised API activity in real time.
Penetration testing can challenge the responsiveness of your monitoring systems by simulating anomalous behaviour. This ensures your tools can detect and respond to threats without being easily bypassed.
8. Automate Compliance and Reporting
Use Policy-as-Code tools like Terraform or CloudFormation to standardise IAM configurations, including roles and password policies. Tools like AWS Config can continuously audit compliance, while AWS Access Analyzer identifies resources shared with external entities. For organisations with multiple accounts, Service Control Policies can restrict root user actions or prevent the creation of new IAM users and access keys.
Penetration tests can confirm that these automated workflows enforce IAM policies effectively and prevent unauthorised access, ensuring continuous compliance with standards like PCI DSS and HIPAA.
Penetration Testing Methods for Checklist Validation
To make sure your IAM compliance checklist is both thorough and effective, several testing methods can provide critical insights. These methods draw on resources like the OWASP Web Security Testing Guide and a six-stage network testing framework: Planning, Reconnaissance, Vulnerability Identification, Exploitation, Post-Exploitation, and Reporting. This approach works for both traditional systems and cloud environments like AWS. In cloud settings, testing often centres on IAM users, groups, roles, and trust policies, with tools like the IAM Policy Simulator used to validate permissions effectively [1][11][12].
Manual vs Automated Testing
Each approach has its strengths and limitations. Manual penetration testing stands out for catching complex logic flaws and bypasses that automated tools might miss. Skilled professionals, such as those with OSCP or CREST certifications, can creatively analyse role-based access control and privilege escalation scenarios. However, manual testing can be time-intensive, costly, and challenging to scale for ongoing monitoring [1][12][14].
On the other hand, automated testing is efficient for identifying known vulnerabilities, misconfigurations, and account enumeration issues. These tools integrate well with CI/CD pipelines, enabling continuous compliance checks. They are particularly effective for monitoring password policies and spotting configuration errors. However, automated tools may generate false positives and often struggle with complex workflows [1][13].
Pen testing tells you how an opponent could get into your environment... Threat hunting tells you who is already in your environment and what they're up to.
– Sarah Maloney, Writer, Cybereason [12]
A balanced approach combines the strengths of both methods. Automated scanning provides continuous visibility, while manual testing dives deeper into intricate business logic vulnerabilities. This hybrid model is gaining traction, with the penetration testing market expected to grow from around £1.1 billion in 2022 to approximately £2.2 billion by 2027 [14].
Tools and Techniques for Each Checklist Item
With testing methods outlined, the next step is to match specific tools and techniques to your IAM checklist items.
Authentication testing: Use phishing simulation tools and password strength checkers to ensure MFA is enforced. Test account lockout mechanisms to confirm they work without exposing sensitive details during login or password reset attempts. A system passes if MFA is required for all users; it fails if weak passwords or default credentials are found. AWS suggests a minimum password length of 14 characters and rotating access keys every 90 days [1][2][13].
Authorisation testing: In cloud environments, tools like the AWS IAM Policy Simulator can help validate permissions. Combine this with manual testing for privilege escalation. For example, attempt to access admin-only features using a low-privilege account. The system passes if users are restricted to their assigned roles; it fails if role boundaries can be bypassed [1][11].
Identity lifecycle management: Use automated scripts to test account creation and deprovisioning processes. Check that deactivated accounts cannot be reactivated without proper controls. The IAM Credential Report is useful for identifying credentials inactive for over 90 days. Systems should disable accounts after 90 days of inactivity, and duplicate usernames or insecure tokens signal compliance failures [1][11][13].
Audit and logging validation: AWS tools like CloudTrail, CloudWatch, and AWS Config are essential for ensuring all API calls and sensitive actions are logged. Logs must remain tamper-proof and accessible. A system passes if all management console actions are recorded and centralised; it fails if logs lack proper access controls [2][13].
Remote access controls: Tools like GuardDuty, Security Hub, and port scanners can verify that services are only accessible from authorised IP ranges. Remote access should be restricted to specific IPs, and any publicly exposed resources indicate a compliance issue [3][13].
Penetration tests should be conducted at least annually or after major changes, such as migrating to a new cloud provider or introducing new features. In the UK, the NCSC recommends using the CHECK scheme for external tests to ensure government security standards are met [3]. Always perform testing in a controlled environment that mirrors the live system to avoid disrupting operations [3].
These testing practices are crucial for maintaining compliance with frameworks like PCI DSS, GDPR, HIPAA, and ISO 27001. For tailored advice on integrating these methods into your IAM strategy, Hokstad Consulting offers expert guidance.
Need help optimizing your cloud costs?
Get expert advice on how to reduce your cloud expenses without sacrificing performance.
Regulatory Updates for 2025 and Their Impact
Recent regulatory updates have introduced new technical and procedural requirements that organisations must address to stay compliant. Here's a closer look at these updates and their implications for identity and access management (IAM).
As of January 2025, PCI DSS v4.0.1 is the mandatory standard for organisations handling cardholder data [16]. One major change is the expanded requirement for multi-factor authentication (MFA), now mandatory for all Cardholder Data Environment (CDE) access [16][4]. This includes internal users and non-administrative accounts, significantly broadening the scope.
Password policies have also tightened under PCI DSS. Organisations must now enforce a minimum of 12-character passwords (or eight characters if justified), track the history of four previous passwords, and require 90-day password changes for single-factor accounts [18]. The 12-character password rule must be implemented by 31st March 2025 [16][18].
The ISO/IEC 27001:2022 update has reduced its controls from 114 to 93, reorganising them under four key themes [17]. Eleven new controls directly affect IAM governance, including Monitoring Activities (8.16), Information Security for Use of Cloud Services (5.23), and Configuration Management (8.9) [17]. These updates are particularly relevant for organisations managing identities in hybrid or multi-cloud environments.
Meanwhile, the UK Data (Use and Access) Act, effective from 19th June 2025, requires organisations to reassess their IAM policies to align with new data protection and access control guidelines [7][6]. This legislation emphasises continuous evaluation of technical measures, aligning with UK GDPR Article 32's call for regularly testing, assessing, and evaluating
security effectiveness [6].
Mapping Checklist to Regulatory Requirements
Organisations can directly map their IAM compliance checklist to specific regulatory mandates, each with clear deadlines. For instance:
- Authentication mechanisms: PCI DSS Requirement 8.4.2 mandates MFA for all CDE access starting January 2025 [4].
- Password policies: Requirement 8.3.6 enforces a 12-character minimum by 31st March 2025, while 90-day password rotations for single-factor accounts (Requirement 8.3.9) are already in effect [18].
- Audit trails and monitoring: ISO/IEC 27001:2022 Control 8.16 requires continuous monitoring of user access behaviour [17].
- Script management: PCI DSS introduces new requirements, such as Requirement 6.4.3 for script authorisation and integrity checks, and Requirement 11.6.1 for weekly change-detection mechanisms [15][18].
Below is a summary of how these requirements align with checklist items:
| Checklist Item | Primary Regulation | Key Requirement | Deadline/Status |
|---|---|---|---|
| Strengthen Authentication | PCI DSS 4.0 | MFA for all CDE access (Req 8.4.2) | Mandatory since Jan 2025 [4] |
| Strengthen Authentication | PCI DSS 4.0 | 12-character passwords (Req 8.3.6) | Mandatory after 31 March 2025 [18] |
| Maintain Audit Trails | ISO/IEC 27001:2022 | Monitoring activities (Control 8.16) | Risk-based implementation [17] |
| Enforce Authorisation | UK Data Act 2025 | Access control validation | Effective 19 June 2025 [7] |
| Continuous Monitoring | ISO/IEC 27001:2022 | Threat intelligence (Control 5.7) | Risk-based implementation [17] |
PCI DSS 4.0 also introduces a Customised Approach
, allowing organisations to implement alternative security controls if they meet the requirement's objectives and are validated by a Qualified Security Assessor (QSA) [16][4]. This option is particularly useful for organisations with advanced IAM programmes that can demonstrate equivalent or superior security measures.
How Often to Conduct Penetration Testing
Regulators now emphasise regular testing to ensure security measures remain effective. PCI DSS 4.0 Requirement 11.4 requires annual internal and external penetration tests, as well as testing after any significant IAM changes [4]. For high-risk systems, more frequent testing may be necessary.
In addition, PCI DSS mandates quarterly vulnerability scans. These scans, required under Requirement 11.3.2, must be conducted by an Approved Scanning Vendor (ASV) to identify and address vulnerabilities before they can be exploited [18]. Unlike penetration tests, these scans provide ongoing visibility into your security posture between comprehensive assessments.
ISO/IEC 27001:2022 adopts a risk-based approach to testing frequency, requiring organisations to document their risk analysis [17]. For instance, systems with privileged access to sensitive data may require quarterly testing, whereas lower-risk environments could follow an annual schedule. UK GDPR further reinforces the need for regular
evaluations, ensuring that your testing frequency aligns with your risk profile [6].
Access reviews, however, need to occur more frequently. The NCSC recommends quarterly or monthly reviews for privileged accounts in high-risk systems. These reviews ensure that former employees (leavers
) no longer have access and that employees changing roles (movers
) have their permissions adjusted appropriately [2][7]. This process complements penetration testing by confirming that access controls remain aligned with organisational needs.
Measuring IAM Compliance Success
Achieving compliance isn’t just about ticking boxes - it’s about making real strides in security. For most organisations, 95% rate the quality of their audit report as important
or extremely important
when measuring compliance success. This highlights the need for thorough and meaningful assessments [19].
IAM Compliance Metrics
To gauge true security progress, focus on metrics that matter. Credential lifecycle metrics are a key starting point. For instance, tracking the last accessed
date for passwords and access keys can help identify unused permissions [11]. Additionally, monitor the percentage of administrative accounts secured with active MFA and set up alerts for unauthorised sign-in attempts [20]. Regularly review access completion rates - quarterly for full reviews, supplemented with monthly checks for inactive users [20].
Compliance is now a strategic investment, not a check-the-box exercise.
– A-LIGN [19]
Another critical metric is remediation speed. How fast can vulnerabilities be addressed? Industry standards suggest addressing critical flaws within 24–48 hours, high-risk issues within a week, medium risks within 2–4 weeks, and low-risk items within 30–90 days [22]. To measure this, track your Mean Time to Remediate (MTTR) - a clear indicator of your team’s efficiency.
Operational metrics also matter. For example, 75% of users report faster transactions with digital identity services, while 61% encounter no difficulties when using them [21]. These benchmarks can help you evaluate whether your IAM improvements are enhancing user productivity.
| Metric Category | KPI | Recommended Frequency |
|---|---|---|
| Credential Health | % of keys rotated within 90 days | Monthly [20] |
| Access Governance | Completion rate of user access reviews | Quarterly [20] |
| Authentication | % of administrative users with hardware MFA | Continuous [20] |
| Audit Readiness | Number of controls successfully tested | Annual [19] |
With these metrics in place, the next step is ensuring vulnerabilities are addressed swiftly and effectively.
Fixing Vulnerabilities After Testing
There’s a big difference between remediation and mitigation. Remediation involves fully resolving a vulnerability - like fixing code or applying a patch - while mitigation uses temporary measures, such as firewalls or network segmentation, to reduce risk when a permanent fix isn’t immediately available [22][23].
Finding vulnerabilities is easy. Fixing them is not.
– Vicarius [23]
To maintain a strong security posture, act quickly after testing. Bring your security team together to prioritise fixes based on their business impact [3]. Instead of focusing solely on high CVSS scores, prioritise vulnerabilities with known exploits, those impacting critical systems, or those on internet-facing assets [22][23]. For IAM-specific concerns, this means restricting user access to only what’s necessary, deactivating unused access keys, and swiftly removing permissions for former employees [7][24].
Verification is crucial. Re-scan systems and conduct follow-up penetration tests to confirm that fixes were successful and didn’t introduce new issues [22][3]. Always test patches and configuration changes in a staging environment before rolling them out to production [22][3]. Keep detailed records of vulnerabilities, remediation actions, and verification results to support compliance efforts and future audits [22][7].
For ongoing support, Hokstad Consulting offers cloud security audits and IAM optimisation services (https://hokstadconsulting.com). Their expertise in DevOps and cloud infrastructure can help automate compliance workflows, such as monitoring for non-compliant users and automatically deactivating unused access keys [24]. Automation like this not only reduces manual errors but also ensures long-term IAM improvements remain effective.
Conclusion
IAM compliance in 2025 requires more than just ticking boxes - it demands robust and effective security measures. With 61% of breaches linked to compromised credentials [25], the urgency to strengthen identity and access management has never been greater. This guide's checklist - from establishing governance policies to automating compliance reporting - provides a clear plan, but the real game-changer is regular penetration testing. Together, these steps build a strong and reliable security framework.
Manual testing plays a crucial role in uncovering vulnerabilities like business logic flaws and account takeovers [5]. Compliance frameworks such as PCI DSS 4.0, GDPR Article 32, and the anticipated 2025 HIPAA updates mandate annual testing [5]. Additional tests are essential after significant changes to ensure IAM systems remain effective [3].
Independent third-party consultants bring impartiality to the table, offering audit-ready reports backed by detailed proof-of-concept evidence [5]. For example, Hokstad Consulting provides customised cloud security audits and IAM optimisation services. Their approach combines DevOps expertise with automated compliance workflows, helping businesses improve security while cutting cloud costs by 30–50%.
With machine identities expected to outnumber human identities 45 to 1 by 2025, and 99% of cloud users currently holding excessive permissions [25], continuous validation is non-negotiable. By following this checklist, prioritising regular testing, and acting swiftly on findings, organisations can transform compliance from a requirement into a competitive advantage. Expert guidance and ongoing evaluation ensure your security framework stays strong and adaptable in the face of evolving threats.
FAQs
What are the key updates in PCI DSS v4.0.1 that organisations need to address by 2025?
The latest updates in PCI DSS v4.0.1 focus on clarifying existing requirements, making minor tweaks, and addressing errors in the documentation. While no new mandatory controls have been added, some refinements stand out - such as clearer language for requirement 3.4.2, which deals with PAN data relocation, and revised guidance concerning access control documentation.
These adjustments are designed to help organisations implement the standards more consistently and align more effectively with compliance expectations. It's essential for businesses to carefully review these changes and ensure their systems are ready well ahead of the 2025 deadline.
How can organisations automate identity lifecycle management to reduce security risks?
To streamline identity lifecycle management, organisations should visualise the entire journey - from onboarding and role assignment to access reviews, credential updates, and offboarding. Modern Identity and Access Management (IAM) tools can integrate with HR systems to automatically create and deactivate accounts as employees join or leave. This approach significantly reduces the risk of leaving unused credentials active.
Using role-based access controls is a key step to ensure users only have the access they genuinely need. Automation tools or APIs can simplify tasks like approval workflows, updating entitlements, and revoking credentials. Additionally, automating credential rotation - such as every 90 days - helps to close security gaps.
For organisations in the UK, embedding these practices into CI/CD pipelines and cloud workflows ensures that new services start with proper authorisation configurations. By combining automation with robust governance and continuous monitoring, businesses can stay aligned with regulations like GDPR and PCI-DSS, while also mitigating the risks of unauthorised access.
Why is regular penetration testing important for ensuring IAM compliance and security?
Regular penetration testing is essential for uncovering vulnerabilities and misconfigurations lurking in your Identity and Access Management (IAM) systems. It’s also a crucial step for organisations aiming to meet compliance requirements like PCI DSS, HIPAA, and SOC 2, as it provides clear, audit-ready evidence of your security measures.
Beyond compliance, penetration testing is a powerful tool for improving your organisation's overall security. By mimicking real-world threats, it helps ensure your IAM systems are prepared to handle emerging risks, protecting your sensitive data while keeping you aligned with regulatory demands.
