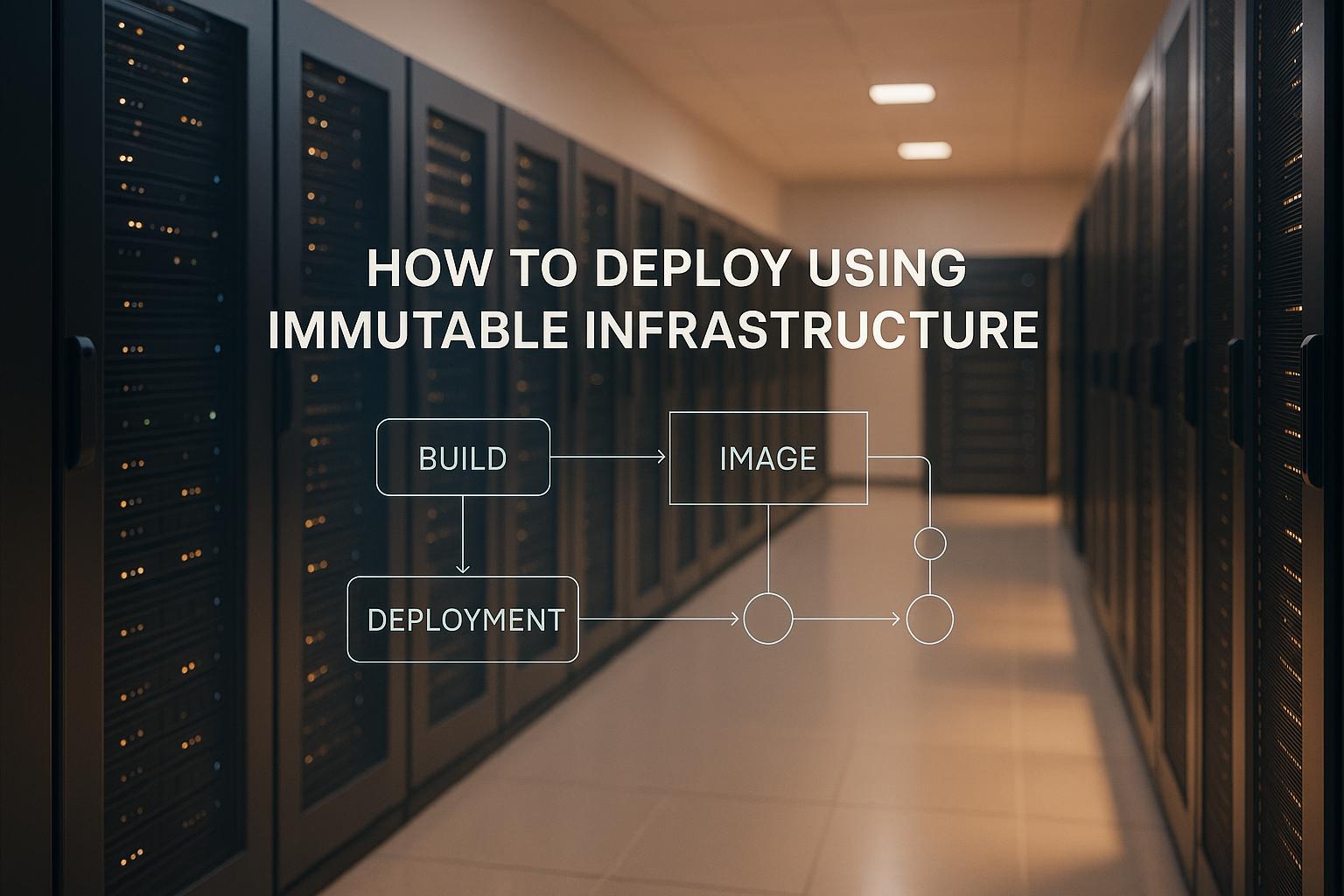
Want reliable, secure, and consistent systems? Immutable infrastructure might be the answer. Instead of updating servers, you replace them with new ones every time. This approach ensures predictable deployments, eliminates configuration drift, and simplifies troubleshooting.
Key Benefits:
- Reliability: Every environment is identical, reducing errors.
- Security: No manual updates mean fewer vulnerabilities.
- Cost Efficiency: Automation minimises human error and operational costs.
- Simplified Rollbacks: Quickly revert to a stable version if needed.
Tools You’ll Need:
- Infrastructure as Code (IaC): Terraform, Pulumi.
- Image Builders: Packer for consistent machine images.
- Containerisation: Docker, Kubernetes for scalable deployments.
- CI/CD Pipelines: Jenkins, GitHub Actions for automation.
Steps to Implement:
- Build Base Images: Use tools like Packer or Docker.
- Automate Provisioning: Define infrastructure with IaC tools like Terraform.
- Validate and Deploy: Test deployments with blue-green or canary strategies.
- Retire Old Resources: Safely decommission outdated servers.
Quick Comparison: Mutable vs Immutable Infrastructure
| Feature | Mutable Infrastructure | Immutable Infrastructure |
|---|---|---|
| Update Process | Manual patches/updates | Deploy new instances |
| Configuration Drift | Likely | Eliminated |
| Rollback | Complex | Simple |
| Security | Risk of manual errors | Clean, secure deployments |
Why switch? Immutable infrastructure ensures consistency, reduces downtime, and improves security. Start small, train your team, and automate processes for a smooth transition.
Automating Immutable Infrastructure With Packer & Terraform
Requirements for Deploying Immutable Infrastructure
Adopting immutable infrastructure requires careful preparation. You’ll need the right tools, well-defined policies, and a clear understanding of costs to make it work effectively. Let’s start by looking at the essential tools and technologies that form the backbone of this approach.
Required Tools and Technologies
Immutable infrastructure depends on a tightly integrated set of tools. Infrastructure as Code (IaC) tools like Terraform allow you to define and provision infrastructure across multiple cloud platforms.
Packer plays a key role by creating consistent machine images. These images ensure uniformity across development, testing, and production environments. For containerisation and orchestration, tools like Docker and Kubernetes are indispensable, enabling you to deploy containers that remain identical across all stages of the pipeline [1][2].
To manage configurations efficiently, tools such as Ansible and SaltStack simplify the process. On the automation front, Jenkins, GitHub Actions, and GitLab CI/CD integrate seamlessly into workflows to streamline deployments. Meanwhile, Git is crucial for version control, ensuring all infrastructure code is tracked and managed effectively [2].
When choosing tools, it’s important to ensure they’re compatible with your existing systems. Think about how well they’ll scale as your organisation grows and how easily your team can adopt them. The goal is to assemble a toolkit that fits naturally into your processes and supports your infrastructure needs [2]. Once the tools are in place, the next step is to establish policies that secure and standardise your approach.
Setting Up Organisational Policies
Clear organisational policies are vital for maintaining consistency and security. Start by enforcing strict version control to keep deployments predictable and reliable [6].
Standardisation is key. Create policies that define how infrastructure is built, tested, and deployed. This includes setting naming conventions, security baselines, and deployment procedures that everyone follows. Automated testing should also be part of the process to catch potential issues before they reach production.
Security should be a top priority. Adopting the Principle of Least Privilege ensures access is restricted to only what’s necessary, reducing risks. Incorporating security checks throughout the IaC process helps identify vulnerabilities early. Additionally, artefact signing protects IaC configurations from tampering, while static analysis and continuous monitoring flag potential issues during development [6].
Cost Planning in GBP
Once you’ve selected your tools and established policies, it’s time to focus on cost planning in GBP. For UK businesses, understanding both initial setup and ongoing operational costs is essential to ensure a sustainable approach.
Initial costs will vary depending on the complexity of your infrastructure and the tools you choose. Many organisations start with a modest monthly budget, covering expenses like licensing fees, staff training, and consulting services for implementation. This phased approach allows you to expand functionality as your needs grow.
Ongoing costs primarily include cloud infrastructure expenses, which can fluctuate based on usage. However, immutable infrastructure often leads to more predictable spending. Automated processes reduce the need for manual intervention and help minimise errors, while the ability to scale resources up or down based on demand keeps costs optimised.
Over time, the benefits become clear. Reduced downtime, faster deployment cycles, and simplified operations lead to long-term savings. Predictable deployments also cut down on expenses related to failed updates or emergency fixes. When planning, it’s important to consider both immediate costs and future savings. Transparent pricing models and subscription-based services can help provide financial clarity and stability [7].
Step-by-Step Guide to Deploying Using Immutable Infrastructure
Deploying with immutable infrastructure can bring consistency, security, and reliability to your environments. Here’s a breakdown of the key steps to make this process smooth and effective.
Building and Testing Base Images
Base images form the backbone of immutable infrastructure, whether you're working with virtual machines or containers.
For virtual machines, tools like Packer automate the creation of pre-configured machine images. First, define your infrastructure needs using tools like Terraform, and let Packer handle building consistent images across platforms. This eliminates manual errors and ensures uniformity [3].
When working with containers, Dockerfiles define the build process. A well-structured Dockerfile ensures uniformity across all stages. For instance:
# syntax=docker/dockerfile:1
FROM scratch AS src
ARG DOTNET_VERSION=8.0.0-preview.6.23329.7
ADD --checksum=sha256:270d731bd08040c6a3228115de1f74b91cf441c584139ff8f8f6503447cebdbb \
https://dotnetcli.azureedge.net/dotnet/Runtime/$DOTNET_VERSION/dotnet-runtime-$DOTNET_VERSION-linux-arm64.tar.gz /dotnet.tar.gz
FROM mcr.microsoft.com/dotnet/runtime-deps:8.0.0-preview.6-bookworm-slim-arm64v8 AS installer
RUN --mount=from=src,target=/src <<eof mkdir tar eof from mcr.microsoft.com copy run ln this multi-stage build keeps only the essential runtime components reducing attack surface while maintaining functionality before deployment test base images thoroughly. use automated vulnerability scans and stick to minimal lower security risks pin versions specific digests maintain supply chain integrity ci pipelines should automate entire process code commits image building deployment. as rohan timalsina explains:=""> Pre-built, versioned images or containers are used for consistent and repeatable deployments. [\[3\]](https://tuxcare.com/blog/what-is-immutable-infrastructure-a-comprehensive-guide)
Once your base images are validated, automate their provisioning with Infrastructure as Code.
### Automating Provisioning with Infrastructure as Code
Infrastructure as Code (IaC) turns infrastructure management into an automated, repeatable process. **Terraform**, for example, is a widely used tool, holding a 32.8% market share globally, making it a popular choice for UK businesses [\[10\]](https://www.firefly.ai/academy/pulumi-vs-terraform-vs-cloudformation-which-iac-tool-is-best-for-your-infrastructure).
Terraform simplifies the `init`, `plan`, and `apply` steps in infrastructure management. Storing your code in Git and using remote state storage ensures consistency [\[9\]](https://developer.hashicorp.com/terraform/tutorials/automation/automate-terraform). Sensitive information can be handled via environment variables, such as setting `TF_IN_AUTOMATION` for cleaner logs suited to CI/CD pipelines [\[9\]](https://developer.hashicorp.com/terraform/tutorials/automation/automate-terraform).
For more complex workflows, tools like **[Spacelift](https://spacelift.io/)** integrate with platforms such as Terraform, [OpenTofu](https://opentofu.org/), Ansible, [AWS CloudFormation](https://aws.amazon.com/cloudformation/), Pulumi, and Kubernetes, supporting diverse IaC approaches [\[5\]](https://spacelift.io/blog/infrastructure-as-code-tools).
Once your infrastructure is defined and stored in version control, it’s time to validate and deploy it using automated tests.
### Validating and Deploying Infrastructure
Before production deployment, validate your infrastructure with automated tests. These tests can catch syntax errors, security vulnerabilities, and compliance issues early, saving time and reducing costs.
Health checks are essential to confirm that the new infrastructure works as expected. These checks should verify application responsiveness, database connectivity, and integrations with external services.
Blue-green deployments are a great fit for immutable infrastructure. Deploy the new environment alongside the existing one, gradually shifting traffic as validation confirms everything is functioning correctly. Start by routing a small percentage of traffic to the new setup, increasing it as confidence grows.
As Rohan Timalsina notes:
> Automation and version control are fundamental to building and managing this approach. [\[3\]](https://tuxcare.com/blog/what-is-immutable-infrastructure-a-comprehensive-guide)
Performance testing under realistic conditions is also crucial. Monitor metrics like response times, error rates, and resource usage to ensure the new infrastructure meets expectations.
### Removing Old Resources
Part of the immutable infrastructure process involves retiring outdated resources safely. Rushing this step can lead to outages or data loss, so it’s essential to proceed carefully.
After shifting production traffic to the new infrastructure, monitor retired assets briefly to ensure everything is running smoothly before starting decommissioning [\[12\]](https://learn.microsoft.com/en-us/azure/cloud-adoption-framework/migrate/release/optimize-cost-after-migration).
Here’s how to handle this step effectively:
- **Testing and Scheduling**: Test the removal process in non-production environments first, and schedule decommissioning during low-impact periods [\[12\]](https://learn.microsoft.com/en-us/azure/cloud-adoption-framework/migrate/release/optimize-cost-after-migration).
- **Holding Period**: Keep decommissioned resources accessible for a set time as a temporary backup [\[12\]](https://learn.microsoft.com/en-us/azure/cloud-adoption-framework/migrate/release/optimize-cost-after-migration).
- **Audits**: Regular audits can identify unused resources. For example, monthly AWS audits might reveal idle Amazon EC2 instances, allowing for cost savings [\[11\]](https://blog.omnistrate.com/posts/49).
- **Documentation**: Maintain detailed records of resource dependencies. This ensures smooth transitions, such as verifying connections between an Amazon RDS instance and dependent services [\[11\]](https://blog.omnistrate.com/posts/49).
- **Automation**: Use scripts to streamline the process. For instance, a script could scan S3 buckets for objects older than 90 days and delete them automatically [\[11\]](https://blog.omnistrate.com/posts/49).
Good communication between teams is key. Operations teams should notify development teams well in advance of decommissioning to address any dependencies or concerns [\[11\]](https://blog.omnistrate.com/posts/49).
<div class="call-to-action">
<div class="cta-content">
<h3>Need help optimizing your cloud costs?</h3>
<p>Get expert advice on how to reduce your cloud expenses without sacrificing performance.</p>
</div>
<div class="cta-button">
<a href="https://calendly.com/hokstad/exploration" class="btn-primary">
Schedule a 30 minutes, no-obligation call
</a>
</div>
</div>
## Tools and Automation Best Practices
With the deployment steps covered, let’s dive into effective practices for tools, automation, and cost management. Choosing the right tools and automation strategies can simplify and enhance your immutable infrastructure deployment.
### Recommended Tools and Platforms
The tools you select play a critical role in achieving secure and efficient automation.
**Packer** is a key tool for creating uniform machine images across multiple platforms from a single configuration. For example, a financial services company used Packer to build "golden images" that included essential security and compliance settings, ensuring consistency across deployments while meeting regulatory requirements [\[2\]](https://devops.com/immutable-infrastructure-the-next-step-for-devops)[\[14\]](https://medium.com/@williamwarley/mastering-packer-a-comprehensive-guide-to-automated-machine-image-creation-61cd7d8ac9ed).
**Terraform** uses a declarative approach to manage infrastructure-as-code, enabling safe and predictable changes. An e-commerce company leveraged Terraform to cut feature rollout times from weeks to days, while also improving their security posture [\[14\]](https://medium.com/@williamwarley/mastering-packer-a-comprehensive-guide-to-automated-machine-image-creation-61cd7d8ac9ed).
**Docker and Kubernetes** work hand-in-hand to address containerisation needs. Docker ensures applications run consistently across environments by packaging them into containers. Kubernetes, on the other hand, handles the orchestration, automating deployment, scaling, and management of these containerised applications [\[2\]](https://devops.com/immutable-infrastructure-the-next-step-for-devops). A global software firm combined Packer with Docker and Kubernetes to create identical environments for development, testing, and production, significantly boosting developer productivity and reducing setup times [\[14\]](https://medium.com/@williamwarley/mastering-packer-a-comprehensive-guide-to-automated-machine-image-creation-61cd7d8ac9ed).
**Jenkins** remains a go-to for automating delivery pipelines, particularly for testing and deploying immutable infrastructures [\[2\]](https://devops.com/immutable-infrastructure-the-next-step-for-devops). Other CI/CD tools, like **GitHub Actions** and **GitLab CI/CD**, offer seamless integration with repositories. GitHub Actions automates workflows directly from the codebase, supporting CI/CD, testing, and deployment. GitLab CI/CD provides advanced customisation options, making it ideal for complex deployment scenarios [\[13\]](https://spacelift.io/blog/devops-automation-tools).
| Tool | Role in Immutable Infrastructure | Integration with CI/CD |
| --- | --- | --- |
| Packer | Creates consistent machine images for various platforms [\[2\]](https://devops.com/immutable-infrastructure-the-next-step-for-devops) | Automates image creation within CI/CD [\[14\]](https://medium.com/@williamwarley/mastering-packer-a-comprehensive-guide-to-automated-machine-image-creation-61cd7d8ac9ed) |
| Terraform | Manages infrastructure as code with a declarative approach [\[2\]](https://devops.com/immutable-infrastructure-the-next-step-for-devops) | Enables safe, predictable infrastructure changes [\[2\]](https://devops.com/immutable-infrastructure-the-next-step-for-devops) |
| Docker | Packages applications into containers for consistency [\[2\]](https://devops.com/immutable-infrastructure-the-next-step-for-devops) | Simplifies deployment across environments [\[2\]](https://devops.com/immutable-infrastructure-the-next-step-for-devops) |
| Kubernetes | Automates management of containerised applications [\[2\]](https://devops.com/immutable-infrastructure-the-next-step-for-devops) | Orchestrates containers for scalable deployment [\[2\]](https://devops.com/immutable-infrastructure-the-next-step-for-devops) |
### Automation and Security Integration
Security should be seamlessly embedded into your Infrastructure as Code (IaC) process. Tools like [Xygeni](https://xygeni.io/) continuously scan Terraform, CloudFormation, Kubernetes, Bicep, and ARM templates to ensure compliance with best practices [\[6\]](https://xygeni.io/blog/infrastructure-as-code-security-best-practices). This automated scanning helps maintain robust cloud security.
Container image scanning is essential for identifying vulnerabilities within images before deployment [\[6\]](https://xygeni.io/blog/infrastructure-as-code-security-best-practices). Xygeni also offers a secrets security solution that scans repositories for hardcoded credentials, blocking insecure commits during the CI/CD process. This proactive approach prevents security risks from reaching production [\[6\]](https://xygeni.io/blog/infrastructure-as-code-security-best-practices).
**Policy-as-Code** enables you to define and enforce rules programmatically, reducing manual errors. Similarly, artifact signing ensures the authenticity of infrastructure components before deployment [\[6\]](https://xygeni.io/blog/infrastructure-as-code-security-best-practices).
Integrating static analysis tools into CI/CD pipelines helps detect vulnerabilities early in development. This not only lowers remediation costs but also strengthens overall security [\[6\]](https://xygeni.io/blog/infrastructure-as-code-security-best-practices). Beyond security, efficient automation also focuses on performance and cost management.
### Performance and Cost Optimisation
Streamlining builds can significantly reduce both deployment times and costs. Techniques like caching installation files and dependencies between builds save time and bandwidth. Additionally, optimising Docker images by reducing the number of layers and using minimal base images can cut storage costs and shrink the attack surface.
Multi-stage builds are another effective strategy, as they ensure only essential runtime components are included in the final image. Regular audits and automated scripts can identify and remove unused resources, keeping costs under control as your infrastructure scales.
Dr. Anirudh Mustyala from JPMorgan Chase & Co emphasises:
> Infrastructure automation tools offer multiple benefits that can help you scale your tech infrastructure effectively...Automated provisioning and configuration...Reduced manual errors...Faster change implementation [\[15\]](https://www.linkedin.com/advice/0/how-can-infrastructure-automation-tools-help-you-ssgyf)
To further optimise costs, focus on right-sizing instances based on actual usage rather than peak demand. Fine-tuning auto-scaling policies ensures resources adjust to demand without unnecessary over-provisioning. When done right, this approach can cut cloud expenses by 30–50%.
Standardising processes with Infrastructure as Code ensures consistency, reduces troubleshooting time, and lets teams concentrate on delivering value. For businesses in the UK, partnering with experts who understand technical and regulatory nuances can simplify adoption and ensure compliance with local standards.
## Benefits, Challenges, and Best Practices
Building on the deployment process outlined earlier, let's delve into the benefits, challenges, and best practices that can help refine your approach to immutable infrastructure.
### Benefits of Immutable Infrastructure
Using immutable infrastructure brings a range of advantages, particularly in terms of security and operational reliability. Each deployment starts with a clean slate, simplifying debugging and rollbacks. This approach eliminates configuration drift, ensuring your systems maintain a consistent and verified state [\[1\]](https://www.legitsecurity.com/aspm-knowledge-base/what-is-immutable-infrastructure).
From a security perspective, immutable infrastructure prevents in-place changes that could lead to vulnerabilities through manual updates or quick fixes [\[1\]](https://www.legitsecurity.com/aspm-knowledge-base/what-is-immutable-infrastructure)[\[3\]](https://tuxcare.com/blog/what-is-immutable-infrastructure-a-comprehensive-guide). Operationally, organisations often notice fewer support issues [\[16\]](https://blog.makstar.co.uk/what-is-immutable-infrastructure) and enjoy more predictable release cycles. Blue-green deployments, for instance, allow seamless traffic transitions and minimise downtime [\[1\]](https://www.legitsecurity.com/aspm-knowledge-base/what-is-immutable-infrastructure).
| Aspect | Mutable Infrastructure | Immutable Infrastructure |
| --- | --- | --- |
| Configuration Management | Manual updates and modifications | Automated deployment of new instances |
| Configuration Drift | Prone to inconsistencies | Eliminates configuration drift |
| Rollback Capability | Complex and risky | Simple reversion to previous versions |
| Security Posture | Vulnerable to incremental changes | Clean, verified state for each deployment |
| Support Requirements | Higher due to inconsistencies | Reduced support calls [\[16\]](https://blog.makstar.co.uk/what-is-immutable-infrastructure) |
However, adopting immutable infrastructure is not without its challenges.
### Common Challenges and Solutions
Transitioning to immutable infrastructure can present hurdles that demand thoughtful planning and execution:
- **Initial setup complexity:** Setting up robust CI/CD pipelines and efficient processes for creating images or containers is essential [\[3\]](https://tuxcare.com/blog/what-is-immutable-infrastructure-a-comprehensive-guide).
- **Increased storage needs:** Multiple image versions can increase costs. This can be managed by automating cleanup policies and optimising image sizes through multi-stage builds [\[3\]](https://tuxcare.com/blog/what-is-immutable-infrastructure-a-comprehensive-guide).
- **Learning curve and cultural shift:** Teams may need training on tools like Packer, Docker, and Kubernetes, as well as adopting a "replace, don't update" mindset [\[3\]](https://tuxcare.com/blog/what-is-immutable-infrastructure-a-comprehensive-guide).
- **Debugging and troubleshooting:** Without direct access to running servers, issues must be recreated in a clean environment. Reliable logging and monitoring systems are critical here [\[3\]](https://tuxcare.com/blog/what-is-immutable-infrastructure-a-comprehensive-guide).
- **Stateful applications and data persistence:** To ensure data accessibility, separate state management from immutable components [\[3\]](https://tuxcare.com/blog/what-is-immutable-infrastructure-a-comprehensive-guide).
Addressing these challenges requires adopting best practices that streamline deployments and strengthen security.
### Best Practices for Deployment
To successfully deploy immutable infrastructure, consider these strategies:
- **Security as code:** Build security into your infrastructure from the start, incorporating encryption, access controls, and vulnerability scanning. Role-based access control (RBAC) can also help prevent unauthorised access [\[18\]](https://codefresh.io/learn/infrastructure-as-code/why-you-need-immutable-infrastructure-and-4-tips-for-success)[\[19\]](https://zeet.co/blog/infrastructure-as-code-best-practices).
- **Frequent rollback testing:** Automate and test rollback processes regularly to ensure you can quickly return to a stable state when needed [\[18\]](https://codefresh.io/learn/infrastructure-as-code/why-you-need-immutable-infrastructure-and-4-tips-for-success).
- **Minimise image sizes:** Use lightweight base images and multi-stage builds to optimise resource use. Regularly audit image contents for efficiency [\[3\]](https://tuxcare.com/blog/what-is-immutable-infrastructure-a-comprehensive-guide).
- **Version everything:** Maintain detailed records of changes to infrastructure, application code, and data for full traceability [\[18\]](https://codefresh.io/learn/infrastructure-as-code/why-you-need-immutable-infrastructure-and-4-tips-for-success).
- **Decouple state management:** Separate data from applications and infrastructure to allow independent updates, reducing the risk of data loss during deployments [\[18\]](https://codefresh.io/learn/infrastructure-as-code/why-you-need-immutable-infrastructure-and-4-tips-for-success).
- **Monitoring and logging:** Observability is key for tracking performance, identifying issues, and addressing them proactively [\[19\]](https://zeet.co/blog/infrastructure-as-code-best-practices).
- **Automate processes:** Automating tasks reduces human error and ensures deployments are consistent and reproducible [\[4\]](https://docs.aws.amazon.com/wellarchitected/latest/framework/rel_tracking_change_management_immutable_infrastructure.html).
- **Detect configuration drifts:** Use tools to identify and address unauthorised changes before they impact your systems [\[4\]](https://docs.aws.amazon.com/wellarchitected/latest/framework/rel_tracking_change_management_immutable_infrastructure.html).
For UK organisations, these practices not only improve operational efficiency but also aid compliance with data protection and financial regulations. By aligning with these best practices, businesses can achieve secure, scalable, and predictable deployment processes that integrate seamlessly with their CI/CD pipelines.
## Conclusion
Shifting to immutable infrastructure is transforming cloud deployments across the UK, offering gains in security, reliability, and operational efficiency. Organisations adopting this method report fewer support calls [\[16\]](https://blog.makstar.co.uk/what-is-immutable-infrastructure), faster resolution of security incidents [\[16\]](https://blog.makstar.co.uk/what-is-immutable-infrastructure), and the complete removal of configuration drift [\[16\]](https://blog.makstar.co.uk/what-is-immutable-infrastructure).
### Key Points Summary
Immutable deployments provide distinct advantages for UK businesses, particularly those operating under strict regulatory requirements. By eliminating manual updates, each deployment starts from a clean, verified baseline, significantly bolstering security [\[1\]](https://www.legitsecurity.com/aspm-knowledge-base/what-is-immutable-infrastructure). This is particularly critical as 75% of security professionals have noted a rise in cyberattacks over the past year [\[20\]](https://gitprotect.io/blog/why-immutable-backups-are-essential-for-data-security-in-devops).
Operationally, the benefits are just as compelling. Blue-green deployments are streamlined, troubleshooting and rollbacks are simplified, and software updates become faster and more predictable, enabling businesses to adapt swiftly to market changes [\[1\]](https://www.legitsecurity.com/aspm-knowledge-base/what-is-immutable-infrastructure). As highlighted by [Legit Security](https://www.legitsecurity.com/):
> Your infrastructure demands consistency, security, and efficiency. The immutable infrastructure approach achieves this by deploying patches and updates as new instances instead of modifying existing environments, eliminating configuration drift and reducing security vulnerabilities.
- Legit Security [\[1\]](https://www.legitsecurity.com/aspm-knowledge-base/what-is-immutable-infrastructure)
From a cost perspective, immutable infrastructure minimises manual intervention and reduces maintenance expenses [\[21\]](https://www.linkedin.com/pulse/immutable-infrastructure-path-stability-efficiency-tahmid-ul-muntakim-uyzhc). Automation tools like Terraform and Pulumi, paired with CI/CD pipelines powered by platforms such as GitHub Actions or Jenkins, further enhance confidence in both software quality and the underlying architecture [\[17\]](https://www.boxuk.com/insight/automation-and-immutable-infrastructure-what-it-means-for-your-business).
The importance of these practices is underscored by security trends: 94% of decision-makers either already use immutable data storage or plan to adopt it within the next year [\[20\]](https://gitprotect.io/blog/why-immutable-backups-are-essential-for-data-security-in-devops), while 69% consider it a critical element of their cybersecurity strategy [\[20\]](https://gitprotect.io/blog/why-immutable-backups-are-essential-for-data-security-in-devops).
These advantages make a compelling case for immediate action.
### Next Steps for Implementation
To realise the benefits of immutable infrastructure, UK businesses should take a methodical approach. Begin by evaluating existing deployments to identify applications that would gain the most, focusing on those requiring high availability and robust security.
Initial steps include creating version-controlled Infrastructure as Code configurations, setting up reliable CI/CD pipelines, and adopting containerisation tools like Docker and Kubernetes [\[1\]](https://www.legitsecurity.com/aspm-knowledge-base/what-is-immutable-infrastructure). Start with less critical applications to refine the process before moving on to mission-critical systems.
Equally important is the need for team training and a shift in mindset. Adopting a "replace, don't update" philosophy is key, alongside developing expertise with modern DevOps tools. Regular security assessments and compliance checks should also become standard practice, particularly for organisations handling sensitive data under GDPR.
### How [Hokstad Consulting](https://hokstadconsulting.com/) Can Help

For businesses seeking expert guidance, Hokstad Consulting offers specialised support to accelerate adoption. Their expertise in DevOps transformation and cloud optimisation ensures a smooth shift to immutable infrastructure while delivering measurable results. Clients have reported cloud cost reductions of 30–50% and faster deployment cycles, perfectly aligning with the efficiency gains of this approach.
Hokstad Consulting provides strategic cloud migration services designed to ensure zero downtime. Their capabilities in automating CI/CD pipelines, custom development, and ongoing security audits address the technical needs essential for successful implementation.
With tailored solutions for public, private, and hybrid cloud environments, Hokstad Consulting offers comprehensive support to UK businesses. Their "No Savings, No Fee" model for cost optimisation reflects their commitment to delivering tangible improvements in deployment processes and operational efficiency.
## FAQs
<div class="faq">
<h3 class="faq-question">What challenges do businesses face when adopting immutable infrastructure, and how can they address them?</h3>
<div class="faq-answer">
<p>Adopting immutable infrastructure comes with its fair share of challenges, primarily due to the <strong>shift in mindset</strong> it requires. Transitioning from mutable to immutable systems often means rethinking workflows, team dynamics, and established practices. On top of that, navigating the <strong>learning curve</strong> of new tools and frameworks can slow down the process.</p>
<p>To tackle these obstacles, businesses should invest in <strong>thorough training</strong> for everyone involved. This ensures that teams not only understand the technical aspects but also the advantages of adopting immutable systems. Promoting collaboration across departments and implementing clear, well-tested workflows can further ease the transition. By creating an environment that supports flexibility and equipping teams with the right resources, organisations can set themselves up for success with immutable infrastructure while reaping its long-term rewards.</p>
</div>
</div>
<div class="faq">
<h3 class="faq-question">What are the long-term cost and efficiency benefits of using immutable infrastructure for cloud operations?</h3>
<div class="faq-answer">
<p>Adopting <strong>immutable infrastructure</strong> can bring long-term advantages to cloud operations. By removing configuration drift and enabling consistent, repeatable deployments, it simplifies troubleshooting and cuts down on operational headaches. This method also strengthens security and supports scalability, resulting in environments that are more predictable and resilient.</p>
<p>In practice, this approach leads to fewer failures, quicker deployment cycles, and lower cloud expenses. Immutable infrastructure streamlines processes, helping organisations run their cloud systems more efficiently while keeping costs under control.</p>
</div>
</div>
<div class="faq">
<h3 class="faq-question">What are the best practices for maintaining security and compliance when using immutable infrastructure?</h3>
<div class="faq-answer">
<p>To uphold <strong>security</strong> and <strong>compliance</strong> with immutable infrastructure, it's crucial to begin with clean, verified images for all deployments. By steering clear of in-place modifications, you minimise vulnerabilities and ensure a consistent setup across your systems.</p>
<p>Automating essential tasks like patching and updates not only reduces the likelihood of human error but also helps maintain uniform configurations across different environments. Additionally, securing your deployment pipelines is a must - it limits potential attack vectors and ensures alignment with organisational standards. These steps collectively lead to a more predictable and secure infrastructure, all while simplifying the process of managing compliance.</p>
</div>
</div>
</eof>