Creating Identity and Access Management (IAM) policies that align with GDPR is not just about security - it’s a legal requirement. Non-compliance can lead to fines of up to £17.5 million or 4% of global turnover, data processing bans, and loss of trust. Here’s a quick breakdown:
- Key GDPR Principles for IAM: Data minimisation, purpose limitation, accuracy, storage limitation, integrity, confidentiality, and accountability.
- IAM Controls for Compliance: Use Role-Based Access Control (RBAC) for predefined roles and Attribute-Based Access Control (ABAC) for dynamic, context-specific rules. Implement Multi-Factor Authentication (MFA) and Single Sign-On (SSO) for secure access.
- Automation and Monitoring: Automate access provisioning and deprovisioning to enforce least privilege. Regular audits, access reviews, and logging ensure compliance with GDPR’s accountability standards.
- Legal Foundations: Article 5 and Article 25 mandate data protection by design, limiting data collection and ensuring robust security measures.
The stakes are high, but effective IAM policies reduce risks, protect personal data, and demonstrate compliance. Below, we explore practical steps and tools to achieve this.
GDPR Basics and How They Apply to IAM
Main GDPR Principles for IAM
The General Data Protection Regulation (GDPR) outlines seven key principles that guide how organisations handle personal data, each with implications for Identity and Access Management (IAM) systems. For example, data minimisation ensures that only the essential personal data required for a user’s role is collected and accessed, aligning closely with the IAM principle of least privilege [5]. Similarly, purpose limitation restricts access to specific, predefined functions, making Role-Based Access Control (RBAC) a critical component [5].
The accuracy principle requires organisations to keep identity data up to date, which can be achieved through regular access reviews and data correction processes [5]. Meanwhile, storage limitation mandates that personal data is retained only for as long as necessary, underscoring the importance of efficient processes for onboarding, role changes, and offboarding (commonly referred to as joiner, mover, leaver processes). These processes ensure that access is revoked and data is either deleted or anonymised when no longer needed [5].
The integrity and confidentiality principle demands robust technical and organisational measures to safeguard data. This includes implementing Multi-Factor Authentication (MFA), encryption, and RBAC to prevent unauthorised access [5].
One of the most critical principles, accountability, requires organisations to demonstrate compliance through proper documentation, detailed access logs, and audit trails. As highlighted by the Information Commissioner’s Office (ICO):
Accountability is not a box-ticking exercise. Being responsible for compliance with the UK GDPR means that you need to be proactive and organised about your approach to data protection.[2]
Legal Requirements for Access Management
IAM systems must operate within a clear legal framework for processing identity data. Under the lawfulness, fairness, and transparency principle, organisations are required to establish a valid legal basis - such as obtaining explicit user consent or demonstrating legitimate interest - before processing personal data [5]. This legal basis must also be documented for transparency.
Article 25 of GDPR introduces the concept of Data Protection by Design and Default, which requires organisations to embed privacy measures into IAM systems from the outset [4]. For access management, this means collecting only the user attributes necessary for authentication and authorisation, avoiding the retention of unnecessary personal information just in case
[5].
These legal principles provide the foundation for understanding the risks and penalties tied to non-compliance in IAM.
Consequences of Non-Compliance
Failing to comply with GDPR can result in significant financial penalties. Organisations risk fines of up to £17.5 million or 4% of their total annual global turnover, whichever is greater [5].
Beyond financial repercussions, non-compliance can lead to operational challenges, including audits and restrictions on data processing activities. Reputational damage is another major concern. For instance, only 18% of companies reported being aware of whether their vendors were sharing information with third parties, highlighting how compliance failures can undermine trust across the supply chain [3].
In the event of a data breach, organisations are required to notify authorities within 72 hours if the breach poses a risk to individuals’ rights. This makes robust IAM systems with strong logging and monitoring capabilities a necessity [1].
Core Elements of GDPR-Compliant IAM Policies
::: @figure 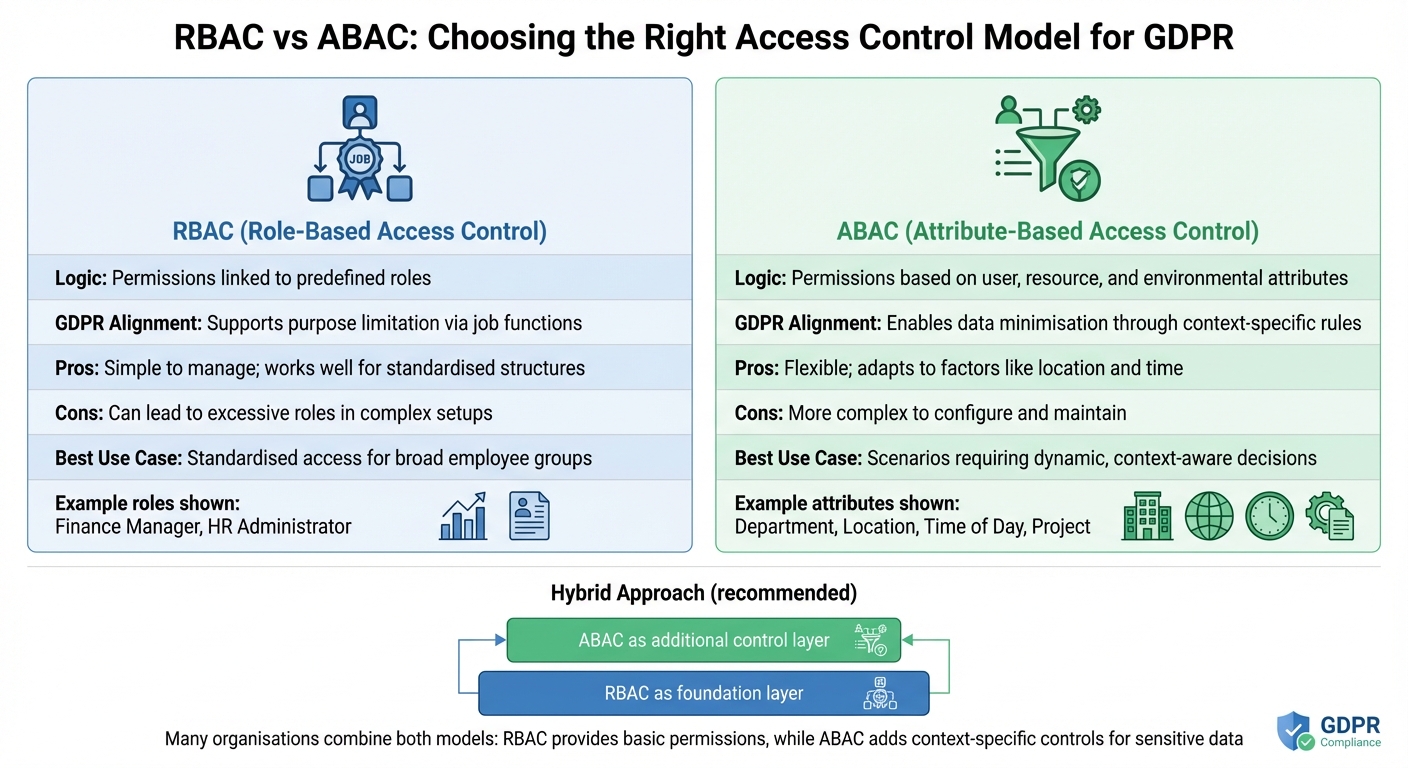 {RBAC vs ABAC for GDPR Compliance: Key Differences and Use Cases}
:::
{RBAC vs ABAC for GDPR Compliance: Key Differences and Use Cases}
:::
To effectively secure and manage access under GDPR principles, organisations need to focus on three key areas: access assignment, identity verification, and ongoing management. Here’s how these elements come together.
RBAC and ABAC for GDPR Compliance
Role-Based Access Control (RBAC) assigns permissions based on predefined job roles like Finance Manager
or HR Administrator.
This approach ties access directly to business needs. However, in complex environments, RBAC can lead to role explosion
, where managing an overwhelming number of roles becomes a challenge.
Attribute-Based Access Control (ABAC), on the other hand, uses dynamic conditions - such as department, location, time of day, or project assignment - to determine access. This approach allows for context-specific rules, such as limiting access to EU data centres or restricting sensitive data usage to business hours.
| Feature | RBAC | ABAC |
|---|---|---|
| Logic | Permissions linked to predefined roles | Permissions based on user, resource, and environmental attributes |
| GDPR Alignment | Supports purpose limitation via job functions | Enables data minimisation through context-specific rules |
| Pros | Simple to manage; works well for standardised structures | Flexible; adapts to factors like location and time |
| Cons | Can lead to excessive roles in complex setups | More complex to configure and maintain |
| Best Use Case | Standardised access for broad employee groups | Scenarios requiring dynamic, context-aware decisions |
Many organisations combine these models: RBAC provides a foundation for basic permissions, while ABAC adds an extra layer of control for sensitive or context-dependent data.
Beyond access control models, authentication methods play a crucial role in aligning IAM policies with GDPR requirements.
MFA and SSO for Secure Access
Multi-Factor Authentication (MFA) strengthens identity security by requiring multiple verification steps, such as a password paired with a mobile authentication code. This approach directly supports GDPR principles of data integrity and confidentiality.
Single Sign-On (SSO) simplifies the authentication process by allowing users to access multiple systems with a single set of credentials. Besides convenience, SSO improves visibility into access patterns and streamlines audit logging - key components of GDPR’s accountability requirements. Together, MFA and SSO form a strong authentication framework that protects personal data while maintaining comprehensive access records.
Securing authentication is just the start. Regular reviews and automated processes ensure compliance remains consistent over time.
Access Reviews and Automated Provisioning
Regular access reviews help organisations identify and remove unused permissions, ensuring compliance with GDPR’s data retention principles. Automated provisioning and deprovisioning systems instantly adjust access rights when roles change, reducing the risk of unused or orphaned
accounts.
For example, reviewing last accessed
data makes it easier to enforce the principle of least privilege by removing permissions that are no longer necessary. When IAM tools integrate with HR systems, access can be revoked immediately when an employee’s status changes, further reducing security risks.
This granular level of control supports GDPR compliance and enhances efficient operation by automatically providing access to those users that require it based on their role.- Idenhaus [3]
Additionally, tagging systems that handle Personally Identifiable Information (PII) allows organisations to apply stricter access controls to sensitive data. This ensures that only authorised personnel can interact with GDPR-regulated information, reinforcing compliance and security measures.
How to Design GDPR-Compliant IAM Policies
Creating IAM policies that align with GDPR requires balancing security, operational efficiency, and adherence to regulatory requirements. Here’s how to craft policies that are both practical and compliant.
Applying Least Privilege and Data Minimisation
Restrict user permissions to only what is necessary for their specific roles. This principle of least privilege not only enhances security but also supports GDPR’s data minimisation requirement by limiting access to sensitive data.
Least-privilege is the security best practice of granting the minimum permissions required to perform a task. Implementing least-privilege access in an already active... account can be challenging because you don't want to unintentionally block users from performing their job duties.- Thomas Scott, Koen van Blijderveen, Adil El Kanabi, and Rafal Pawlaszek, Amazon Web Services [10]
Automated tools can simplify this process by generating precise policies from audit logs that reflect actual usage patterns. This eliminates guesswork and ensures permissions are closely aligned with real business needs. For temporary elevated access, use time-restricted credentials that expire automatically after a set period. Additionally, permissions boundaries can help delegate policy management while maintaining security safeguards, striking a balance between operational needs and GDPR compliance [8].
Such measures create a framework for effective collaboration across teams.
Working Across Teams
Collaboration between legal, IT, and compliance teams is essential. Legal teams establish the lawful basis for data processing, IT translates these into technical controls, and compliance ensures alignment with GDPR standards.
Develop a cross-functional working group that meets regularly to review and update IAM policies. This ensures permissions remain minimal and consistent across all departments.
The controller shall... implement appropriate technical and organisational measures... which are designed to implement data-protection principles, such as data minimisation, in an effective manner- Article 25 of the GDPR [4]
When operational changes occur - like software updates or staff changes - trigger immediate reviews of IAM policies. Senior management should advocate for a culture of data protection, ensuring all teams understand their responsibilities in maintaining GDPR compliance.
Conducting Audits and Updating Policies
After designing and implementing IAM policies, continuous auditing is crucial to maintain compliance. Regular audits help verify that principles like least privilege and data minimisation are consistently applied.
Frequent reviews can uncover potential vulnerabilities. Schedule policy reviews regularly and after significant events, such as employee departures, new system integrations, or suspected unauthorised access.
If policies are not reviewed and updated periodically, or when changes to process are agreed, they will become out of date and ineffective.- Information Commissioner's Office (ICO) [7]
Automate policy validation using tools like CI/CD pipelines to detect overly permissive settings [9]. IAM Access Analyzer, for instance, can identify potential security issues and provide actionable recommendations. Set up alerts for changes affecting sensitive data access to catch unauthorised modifications early.
Sampling access logs periodically ensures controls are working as intended. Export IAM lifecycle events to a centralised logging system for long-term analysis and reporting. Article 30 of the UK GDPR requires organisations to maintain detailed records of processing activities, including data retention periods. Comprehensive IAM audit logs can support these requirements.
| Audit Activity | Frequency | GDPR Alignment |
|---|---|---|
Review last accesseddata |
Monthly | Data minimisation; least privilege |
| Validate policy documentation | Quarterly | Accountability; Article 30 records |
| Test emergency access procedures | Bi-annually | Integrity & confidentiality |
| Cross-functional policy review | Annually or after major changes | Data protection by design |
Documenting these audits provides clear evidence of compliance. GDPR accountability isn’t about ticking boxes - it’s about demonstrating a proactive and systematic approach to data protection through regular updates and reviews.
IAM Tools and Technologies for GDPR Compliance
Selecting the right IAM tools is crucial for maintaining GDPR compliance and ensuring robust security. The focus should be on solutions that incorporate data protection principles at their core, rather than treating compliance as an add-on.
Choosing IAM Tools That Support GDPR
When evaluating IAM tools, prioritise features that align with GDPR's technical requirements. Key functionalities include granular access controls like RBAC (Role-Based Access Control) and ABAC (Attribute-Based Access Control), as well as automated lifecycle management to quickly revoke access when roles change. Temporary credentials that expire automatically are also essential for reducing risks tied to permanent privileged access.
Identity and access management allows organisations to document who has access to what, and determine when and why they were granted access.– Idenhaus [3]
Data protection features such as encryption (both at rest and in transit) and pseudonymisation are fundamental under GDPR. Additionally, tools with policy validation and analysis capabilities can use machine learning to identify risks, such as public or cross-account access, and propose adjustments for overly permissive accounts. Ensure your tools also support EU data residency requirements, keeping identity data within the EU when necessary. These elements ensure the tools integrate smoothly with your existing IAM infrastructure.
Monitoring and Audit Features
To maintain ongoing GDPR compliance, effective monitoring transforms it from a one-off task to a continuous process. IAM tools should include ‘last accessed’ tracking to pinpoint unused permissions, roles, and credentials, enabling regular access reviews and reinforcing the principle of least privilege. Automated data tagging helps enforce stricter governance for resources containing personal data (PII).
Look for tools that provide automated reporting and generate audit-ready documentation of access rights and identity activities. Advanced solutions may also feature anomaly detection, leveraging AI and behavioural analysis to flag unusual access patterns, such as potential insider threats. Robust policy analysis tools can further validate policy configurations and identify unintended public or cross-account access. These capabilities are critical, especially given that GDPR regulators imposed over €114 million in fines during the regulation's first 20 months [6].
Connecting IAM Tools with Existing Systems
Integrating IAM tools with your current systems enhances compliance and operational efficiency. Federated identity management allows legacy systems like Active Directory or LDAP to connect with modern cloud IAM tools, enabling users to access multiple environments with a single set of temporary credentials.
Protocols like SAML, OpenID Connect, and SCIM support secure federation and automated provisioning across systems. For machine identities, such as applications or servers, use IAM roles that issue temporary credentials to avoid relying on long-term access keys. Centralising access management through a unified identity hub simplifies the process of managing permissions across various accounts and systems. During integration, data tagging ensures GDPR-specific access rules are applied automatically, while self-service portals for password resets and access requests maintain efficiency without compromising audit trails.
This granular level of control supports GDPR compliance and enhances efficient operation by automatically providing access to those users that require it based on their role.– Idenhaus [3]
When working with third-party IAM tools, ensure contracts specify compliance with GDPR's Article 32 security measures. Vendor assessments are equally critical, as only 18% of companies are aware if their vendors share information with other suppliers [3].
For more tailored advice on optimising IAM solutions for GDPR, organisations can consult specialists like Hokstad Consulting, who offer expertise in refining cloud infrastructure and implementing strategies that reduce risk while improving operational workflows.
Conclusion
As GDPR reshapes data protection standards, creating IAM policies that align with its requirements is an ongoing responsibility. This isn't just about compliance - it's about safeguarding personal data and ensuring smooth organisational operations. By implementing strong access controls and authentication protocols, organisations can mitigate risks and uphold the accountability demanded by GDPR. As the Information Commissioner's Office (ICO) states: The accountability principle makes it clear that you are responsible for complying with the GDPR... and you must be able to demonstrate your compliance
[2].
Automating provisioning processes and conducting regular reviews not only provide clear audit trails but also enable quick responses to breaches. These practices help protect the confidentiality, integrity, and availability of personal data, ensuring organisations remain compliant while staying prepared for regulatory changes.
Staying ahead of evolving regulations is crucial. The UK Data (Use and Access) Act, enacted on 19 June 2025, highlights how legal frameworks continue to adapt. To keep pace, organisations should routinely test and refine their security measures, leveraging advanced technologies like service mesh solutions for automated mutual TLS or behaviour-based anomaly detection to identify emerging threats.
The stakes for non-compliance are high, with fines reaching up to €20 million or 4% of annual global turnover, whichever is greater [1]. However, beyond avoiding penalties, effective IAM practices can strengthen customer trust, streamline operations through automation, and provide a competitive advantage. For expert advice on aligning your IAM systems with GDPR, consider reaching out to Hokstad Consulting.
FAQs
How does GDPR impact the creation of IAM policies?
GDPR has a profound impact on how Identity and Access Management (IAM) policies are structured, compelling organisations to embed data protection by design and by default into their processes. This involves strictly limiting access to personal data based on necessity, applying least-privilege principles, and using role-based access controls. Wherever feasible, permissions should also be time-limited to further safeguard sensitive information.
Another critical requirement is the maintenance of comprehensive audit logs. These logs help track who accessed or modified personal data, ensuring transparency and accountability. Additionally, IAM policies must facilitate individuals in exercising their GDPR rights, such as requesting access to, correcting, or deleting their personal data, without unnecessary hurdles. By integrating these practices, organisations not only strengthen compliance but also minimise the risk of potential fines.
How do RBAC and ABAC differ in supporting GDPR compliance?
RBAC (Role-Based Access Control) works by assigning permissions to users based on predefined roles. While this makes it easy to set up, it often falls short when dealing with the detailed demands of GDPR. One major issue is its rigidity - roles can overlap, leading to overly broad permissions. This not only complicates managing access but also makes it harder to uphold GDPR principles like purpose limitation and consent tracking. Additionally, during audits, demonstrating precise access controls can become a significant challenge due to this lack of granularity.
ABAC (Attribute-Based Access Control), in contrast, takes a more flexible approach by using dynamic attributes like user roles, data sensitivity, and even location to determine access. This context-aware system aligns well with GDPR’s emphasis on data minimisation and protection by design. For example, it allows organisations to enforce rules such as limiting access to EU-resident data only to users with valid consent, all while maintaining clear and detailed audit trails.
To sum it up, RBAC offers a straightforward setup but struggles to meet GDPR’s nuanced requirements. ABAC, with its dynamic and attribute-driven controls, provides a more effective solution for ensuring compliance and accountability.
How does automation help ensure GDPR compliance in IAM systems?
Automation is key to keeping Identity and Access Management (IAM) systems in line with GDPR requirements. It ensures least-privilege access policies are applied consistently, minimises the chances of human error, simplifies the process of granting and revoking permissions, and offers ongoing monitoring and auditing capabilities.
By automating these tasks, organisations can better meet GDPR’s demands for accountability and data protection. At the same time, it lightens the load on IT teams, making operations more efficient.
