Cloud migration offers scalability but comes with security risks, especially during data transfer and storage. Encryption is the cornerstone of protecting sensitive information throughout the process. Here's what you need to know:
- Data in Transit: Use TLS 1.3 for secure connections and avoid outdated protocols like SSL. Consider VPNs or dedicated connections for added security.
- Data at Rest: Activate cloud-native encryption (e.g., AES-256) and configure access policies carefully. For sensitive workloads, client-side encryption ensures full control over keys.
- Key Management: Cloud-based KMS tools simplify key handling, but hybrid models (e.g., HSMs for root keys) offer greater control. Automate rotation and maintain audit logs.
- Compliance: Ensure encryption aligns with standards like GDPR Article 32 to avoid fines and breaches.
- Common Risks: Misconfigurations, weak key management, and inconsistent policies can expose data. Regular monitoring, logging, and testing mitigate these risks.
Encryption isn't just about tools but also about planning, execution, and continuous oversight. Misconfigurations remain a leading cause of breaches, making proper governance essential. To ensure your migration is secure and compliant, focus on encryption at every stage.
Cloud Transition Strategy: 6 R’s, Security & Post-Migration Steps
Data Assessment and Classification Before Migration
Before starting a migration, it's essential to take stock of your data assets and evaluate their sensitivity. This means cataloguing all assets, noting their locations, access points, and how they flow through your systems. Laying this groundwork helps avoid the risk of transferring unclassified data - a significant concern, as studies show that 60% of breaches involve such data [7]. A well-structured classification framework can then help prioritise encryption efforts.
Data Classification Frameworks
Classifying data correctly is the cornerstone of determining where encryption is necessary. A clear and structured framework categorises data based on sensitivity and establishes encryption priorities. One commonly used model divides data into four tiers:
- Public: No encryption required.
- Internal: Basic protection applied.
- Confidential: Requires encryption both in transit and at rest.
- Restricted: Demands client-side encryption before upload.
For example, an e-commerce company would likely classify customer payment details as restricted under PCI DSS guidelines, applying the highest level of encryption [2][3]. Once classified, data should be mapped to relevant compliance standards. The NIST Special Publication 800-60 framework is a widely respected guide, categorising data by potential impact - low, moderate, or high - on confidentiality, integrity, and availability. This ensures encryption is prioritised where regulatory penalties or business risks are most severe [2][11].
After categorisation, it’s crucial to review the encryption tools provided by your chosen cloud provider to ensure they meet your specific requirements.
Evaluating Cloud Provider Encryption Tools
Once your data is classified, the next step is to evaluate whether your cloud provider's encryption tools are up to the task. For instance, AWS Key Management Service (KMS) offers features like envelope encryption, hardware-backed security modules, and multi-region key support - especially useful for migrations to UK regions like London. Similarly, Azure Key Vault provides managed hardware security modules (HSMs), automatic key rotation, and support for Bring Your Own Key (BYOK). Both services comply with GDPR, but it’s equally important to confirm they meet other standards, such as ISO 27001 or SOC 2, and provide audit logs to satisfy UK data residency requirements [2][7].
For restricted data, check whether the tools support client-side encryption. It’s also wise to test their key rotation capabilities, access controls, and integration with your current systems through proof-of-concept projects. This step ensures the encryption strength aligns with your classification framework while reducing the risk of misconfigurations that could expose sensitive data [2][10].
Matching your classification strategy with the capabilities of encryption tools is critical for a secure migration. For tailored advice on aligning data classification and encryption tools with UK compliance standards, consider consulting specialists like Hokstad Consulting (https://hokstadconsulting.com), who provide customised strategies for secure cloud migrations.
Encryption for Data in Transit
After classifying your data and evaluating your provider's tools, the next step is to protect your information as it moves from your on-premises systems to the cloud. Data in transit
refers to any information travelling across networks - whether it's moving between your data centre and cloud storage, across cloud regions, or from user devices to migration endpoints. Without encryption, this data is vulnerable to interception and man-in-the-middle (MITM) attacks.
For organisations in the UK, securing data in transit isn’t just a smart precaution - it’s also a regulatory requirement. Under GDPR, businesses must implement appropriate technical measures
to safeguard personal data. Similarly, regulators like the FCA expect financial services firms to ensure secure remote connections. A breach during migration can result in mandatory disclosures, hefty fines, and reputational harm, making strong encryption for data in transit an absolute must for any cloud migration project.
Transport Layer Security (TLS) Protocols
Once you’ve addressed regulatory compliance for data in transit, the next focus should be on implementing robust transport protocols. The cornerstone of secure data transfer is Transport Layer Security (TLS), which encrypts communication channels between systems. Organisations should aim to use TLS 1.3 as the default protocol, with TLS 1.2 as a fallback for legacy systems. Older versions like SSLv3, TLS 1.0, and TLS 1.1 should be completely disabled due to their vulnerabilities.
Equally important are strong cipher suites. Configure your load balancers, API gateways, and web servers to use modern algorithms such as AES-GCM with 128-bit or 256-bit keys, paired with key exchange methods like ECDHE. Outdated algorithms, including RC4 and 3DES, should be blocked. While most cloud providers offer pre-configured modern
or recommended
security profiles, it’s wise to double-check these settings manually.
To further secure your data, enforce HTTPS and disable plaintext protocols like HTTP, FTP, and Telnet in favour of their secure counterparts (e.g., HTTPS, SFTP, or SSH). Use certificates from trusted certificate authorities and automate their renewal. Regularly test your configuration with SSL scanning tools to ensure compliance with current standards. Document these settings for internal security reviews and audits.
For complete protection, ensure end-to-end TLS encryption from the source to the destination. For instance, on-premises databases should replicate to cloud storage over mutually authenticated TLS connections. Similarly, administrators should only access migration tools via HTTPS or a VPN with multi-factor authentication. Even within your cloud provider's infrastructure, inter-region replication should use encryption in transit, which most major providers enable by default.
Using VPNs or Dedicated Connections
TLS encryption is essential, but adding network-level encryption provides an extra layer of security during migration. A site-to-site VPN creates an encrypted tunnel (using IPsec) between your on-premises network and the cloud virtual network. This approach strengthens your security boundary while simplifying routing and access control. VPNs are a cost-effective and quick solution for medium-scale migrations or hybrid environments. However, because they rely on the public internet, you might experience variations in latency and throughput.
For organisations handling large data volumes or highly sensitive workloads - such as those in financial services or the NHS - a dedicated connection offers a more secure and reliable alternative. Services like AWS Direct Connect, Azure ExpressRoute, or Google Cloud Interconnect provide a private link from your data centre or colocation facility directly to the cloud provider's network. These connections deliver predictable bandwidth, lower latency, and can help meet compliance requirements by bypassing the public internet. While they come with higher fixed costs, many UK organisations begin with internet-based TLS for pilot migrations, add a site-to-site VPN for hybrid setups, and later transition to dedicated connections as data volumes or regulatory demands grow.
It’s important to note that VPNs and dedicated connections enhance security but don’t replace TLS. For sensitive migration workloads, best practice is to enforce TLS between endpoints and run that traffic over a VPN or dedicated connection. This layered approach aligns with regulatory expectations to encrypt data in transit wherever possible.
When setting up a VPN or private connection, configure IPsec with strong, modern encryption algorithms. Restrict VPN access to only the necessary subnets and ports for migration, such as database replication ports and object-storage endpoints. Where possible, separate migration traffic from general user VPN access. For dedicated connections, work with a UK carrier or colocation provider to provision the circuit, then attach it to the appropriate virtual network gateway. Be meticulous when configuring route tables to avoid accidentally exposing internal networks. To ensure reliability, implement high availability with multiple tunnels or circuits using diverse paths to minimise the risk of outages during migration. Additionally, log all VPN and private connection activity - such as connection attempts, throughput, and errors - and integrate these logs into your SIEM tools for quick detection and investigation of anomalies.
Encryption for Data at Rest
Data stored in the cloud - commonly referred to as data at rest
- faces risks such as unauthorised access and insider threats. Encrypting this data is a critical step to prevent breaches and ensure compliance with GDPR Article 32. Most major cloud providers, like AWS, Google Cloud, and Azure, offer encryption for data at rest, either as a default feature or through straightforward configuration. For example, services such as AWS S3, Google Cloud Persistent Disk, and Azure Blob Storage typically use AES-256 encryption, often enabled automatically. However, encryption alone isn't a silver bullet. Misconfigured access policies or publicly exposed storage buckets can still leave data vulnerable. Even with encryption in place, poor key management or weak access controls can undermine your security efforts. To address these challenges, organisations often turn to a combination of cloud-native and client-side encryption methods, striking a balance between ease of use and control.
Cloud-Native Encryption Solutions
For many organisations, cloud-native encryption is the easiest and most practical starting point. Server-side encryption (SSE) automatically encrypts data as it’s written to storage and decrypts it for authorised users when accessed. For instance, AWS S3 offers SSE-S3, which uses AES-256 encryption with keys fully managed by AWS. For greater control, SSE-KMS enables customers to manage their own keys. Similarly, Google Cloud encrypts all Persistent Disk data by default with AES-256 and provides options for key management through Cloud KMS. Azure offers comparable features via Azure Storage Service Encryption and Azure Disk Encryption.
These built-in solutions integrate seamlessly into cloud environments and align with compliance standards like SOC 2 and PCI DSS. For example, an e-commerce business migrating customer transaction records to AWS S3 can use SSE-KMS to meet PCI DSS requirements while setting up granular key policies. These policies might restrict decryption to specific IAM roles or require multi-factor authentication for key access. Similarly, a financial services organisation using Google Cloud Persistent Disk encryption could configure Cloud KMS to rotate keys quarterly, reducing the risk of breaches in accordance with industry best practices.
However, cloud-native encryption has its limitations. In most cases, the cloud provider manages the cryptographic operations and may retain infrastructure-level access to your data during processing. Even with customer-managed keys (via KMS), this access could pose a concern for highly sensitive data, such as financial records, health information, or trade secrets. For such scenarios, where full control over encryption keys is essential, client-side encryption offers a more secure alternative.
Client-Side Encryption
Client-side encryption ensures that data is encrypted on your premises before it is uploaded to the cloud. In this approach, you retain full control over the encryption keys, and the cloud provider only stores the encrypted data (ciphertext). This means that even if the cloud provider is compromised - or compelled to provide access - they cannot decrypt your data. This method is particularly beneficial for organisations with strict data sovereignty requirements or those adhering to zero trust
principles regarding their cloud provider.
To implement client-side encryption, tools like the AWS Encryption SDK or OpenSSL can be used to encrypt data locally with AES-256-GCM. Keys are managed internally, typically stored in your organisation's key management system (KMS) or hardware security module (HSM), ensuring they never leave your control. When cloud applications need to access the data, they retrieve the keys, decrypt the data in memory, and process it. This approach ensures a higher level of security, even in cases where cloud storage configurations may be flawed or compromised.
While client-side encryption provides enhanced security, it comes with added complexity. Rigorous key management is essential, and disaster recovery plans must account for key availability. Additionally, decryption logic needs to be integrated into cloud applications. Despite these challenges, many organisations handling highly sensitive workloads find the added effort worthwhile. A Thales whitepaper highlights that S3 permissions and encryption options can be confusing, with several major breaches tied to misconfigurations. As a result, it recommends client-side encryption or third-party transparent encryption as extra layers of protection on top of native S3 encryption [9].
In practice, many UK organisations adopt a hybrid approach. They rely on cloud-native encryption for general workloads while reserving client-side encryption for their most sensitive data. This strategy strikes a balance between security, compliance, and operational simplicity, ensuring critical data remains protected and under their control throughout cloud migrations and beyond.
For customised advice on implementing effective encryption strategies during cloud migration, organisations can seek expert consultation from Hokstad Consulting.
Need help optimizing your cloud costs?
Get expert advice on how to reduce your cloud expenses without sacrificing performance.
Key Management Strategies
Even the strongest encryption can fall apart if key management isn’t up to par. The Cloud Security Alliance has pointed out that key management is often more challenging than encryption itself
when migrating to public cloud environments [10]. Supporting this, a 2022 Thales cloud security study revealed that 45% of businesses identified managing keys across cloud providers as a major hurdle in safeguarding cloud-based data [9]. For UK organisations, effective key management is not just a best practice - it’s a necessity for compliance with GDPR and data sovereignty regulations.
Proper key management spans the entire lifecycle: from generation and distribution to storage, rotation, usage, backup, and eventual destruction. Whether keys are stored on-premises, in the cloud, or across both, it’s crucial to establish clearly defined roles for tasks like key creation, rotation, and deletion. Separating responsibilities among security, operations, and application teams can prevent misuse or orphaned keys. With this groundwork in place, organisations can confidently adopt cloud key management solutions.
Cloud Key Management Services (KMS)
Cloud-native Key Management Services (KMS), such as AWS KMS, Azure Key Vault, and Google Cloud KMS, offer API-driven operations, robust access controls, detailed logging, and automated key rotation. These platforms integrate seamlessly with cloud resources like storage, databases, and compute, making them an ideal choice for many workloads. For example, AWS KMS can automatically rotate master keys annually while maintaining access to older key versions for decrypting legacy data. Similarly, Azure Key Vault provides granular Identity and Access Management (IAM) policies to tightly control which accounts and services can use specific keys.
For workloads requiring higher levels of security - like financial services or public sector applications - Hardware Security Modules (HSMs) are an excellent option. These devices provide tamper-resistant, FIPS 140-2 validated storage and key generation. Cloud-based HSM services, such as AWS CloudHSM or Azure Dedicated HSM, combine the scalability of cloud infrastructure with the direct control of on-premises cryptographic operations. A common approach in the UK is a hybrid model: root keys are stored in on-premises or dedicated HSMs, while data encryption keys (DEKs) are managed in the cloud using envelope encryption. This strategy ensures centralised control of critical keys while benefiting from cloud automation.
Envelope encryption is widely used for secure key handling at scale. In this model, data is encrypted with a DEK, which is then wrapped (encrypted) with a master key stored in a KMS or HSM. This method allows organisations to rotate master keys without re-encrypting the data itself - only the wrapped DEKs need updating. Envelope encryption also facilitates secure data migration between environments, with access controlled via designated key encryption keys.
To further strengthen key management, ensure all key operations are strictly logged and audited. Segregating keys by environment, region, and workload can help minimise the impact of a potential compromise. Once a robust KMS is in place, attention should shift to securely migrating keys to maintain encryption integrity.
Secure Key Migration
When moving encryption keys from on-premises systems to the cloud, secure migration is critical to prevent exposure during transit. Start by cataloguing all keys, including their algorithms, sizes, and usage patterns, while retiring any obsolete keys. Use secure, authenticated channels for transferring keys - preferably vendor-provided import mechanisms that rely on pre-established trust and temporary wrapping keys, rather than generic VPNs or manual methods.
To minimise risks, secure keys in HSMs at both the source and destination, and use import tokens to eliminate the need for administrators to handle raw key material. Implement dual control and approval processes, along with comprehensive logging, for every key migration event. Before making the final switch, test the new KMS-managed keys in a non-production environment to ensure applications can decrypt data correctly. Keep the original keying setup operational until the migration is fully validated, and prepare a documented rollback plan in case issues arise.
For especially complex environments, bringing in external experts can reduce risks. Specialists with experience in cloud migration can provide tested runbooks and tools to streamline the process. Organisations looking for tailored advice and automation support can turn to Hokstad Consulting, which focuses on strategic cloud migration and DevOps transformations.
Post-Migration Monitoring and Testing
Once you've migrated to the cloud, the work doesn't stop there. Keeping an eye on encryption settings is crucial to ensure your new configurations stay secure. Without proper oversight, issues like public storage buckets, disabled encryption, or weakened access policies can creep in, and these are common culprits behind cloud data breaches [9]. For organisations in the UK, this isn't just a best practice - it's a legal requirement under UK GDPR to demonstrate accountability and safeguard personal data.
After the migration, start by verifying that all storage classes, databases, backups, and snapshots have encryption at rest enabled. Make sure every data transfer uses TLS 1.2 or higher with strong ciphers [2][5]. Tools like AWS Config or Azure Policy can help you spot any encryption lapses [6]. Setting up alerts for changes to encryption settings, key policies, or IAM roles ensures your security team can respond quickly to any unauthorised modifications. By integrating these checks into your DevOps processes, you can maintain consistent encryption enforcement as your cloud environment evolves. These steps lay the groundwork for detailed monitoring, logging, and regular vulnerability assessments.
Access Control and Logging
The first line of defence for encrypted data is strict access control paired with comprehensive logging. Use role-based access control (RBAC) and follow the principle of least privilege. This means limiting decryption and key management to only those roles that absolutely need it [7]. Separate roles for application access, administrative tasks, and key management, and enforce multi-factor authentication (MFA) for all privileged accounts. Make policies as specific as possible, such as allowing a role to decrypt only with a specific key in a designated region. This approach minimises potential damage if credentials are ever compromised [4].
Enable audit logging across all cloud regions and accounts to track every API call, including changes to encryption settings, IAM policies, and KMS keys [2][4]. Make sure logs for object stores, file shares, and databases capture access events along with details like source IP addresses, user identities, and timestamps [2][6]. For key management systems, ensure audit logs record every encrypt, decrypt, rotation, and policy change [4][10]. Forward these logs to a secure SIEM system with retention settings that comply with UK regulations [2][6]. Don't forget to encrypt the logs themselves to prevent tampering.
Regular Vulnerability Testing
Encryption controls are only as effective as they are resilient. Routine testing is vital to ensure they can't be bypassed. Use automated vulnerability scanning and periodic penetration testing to identify gaps. Configure scanners to flag outdated TLS, weak ciphers, missing HSTS headers, and unencrypted endpoints [2][5]. Cloud-aware tools can also evaluate storage services, databases, and key management policies, checking for misconfigured encryption, public exposure, or overly permissive IAM roles [2][6][8]. For internet-facing components, schedule scans at least monthly, and for internal resources, aim for quarterly checks. Address any findings that could weaken encryption as soon as possible [2][7].
Penetration tests should go a step further by actively trying to bypass encryption. Testers might intercept unencrypted traffic, exploit misconfigurations, or escalate privileges [2][8]. They should confirm that unauthorised users cannot access data without the correct keys and that KMS interfaces enforce strict authentication [4][10]. Align testing with NCSC guidance and your organisation's critical processes, and make sure to repeat tests after significant changes to your architecture or encryption policies. Use the findings to update infrastructure templates, CI/CD pipelines, and policies, reducing the risk of repeated errors [6][8].
If you're looking for expert help to design monitoring systems, integrate logs into your DevOps workflows, or implement cost-efficient safeguards, Hokstad Consulting offers tailored cloud migration and automation services. Their expertise can help you maintain robust encryption and testing processes as your environment grows [6][8].
Common Challenges and Solutions
::: @figure 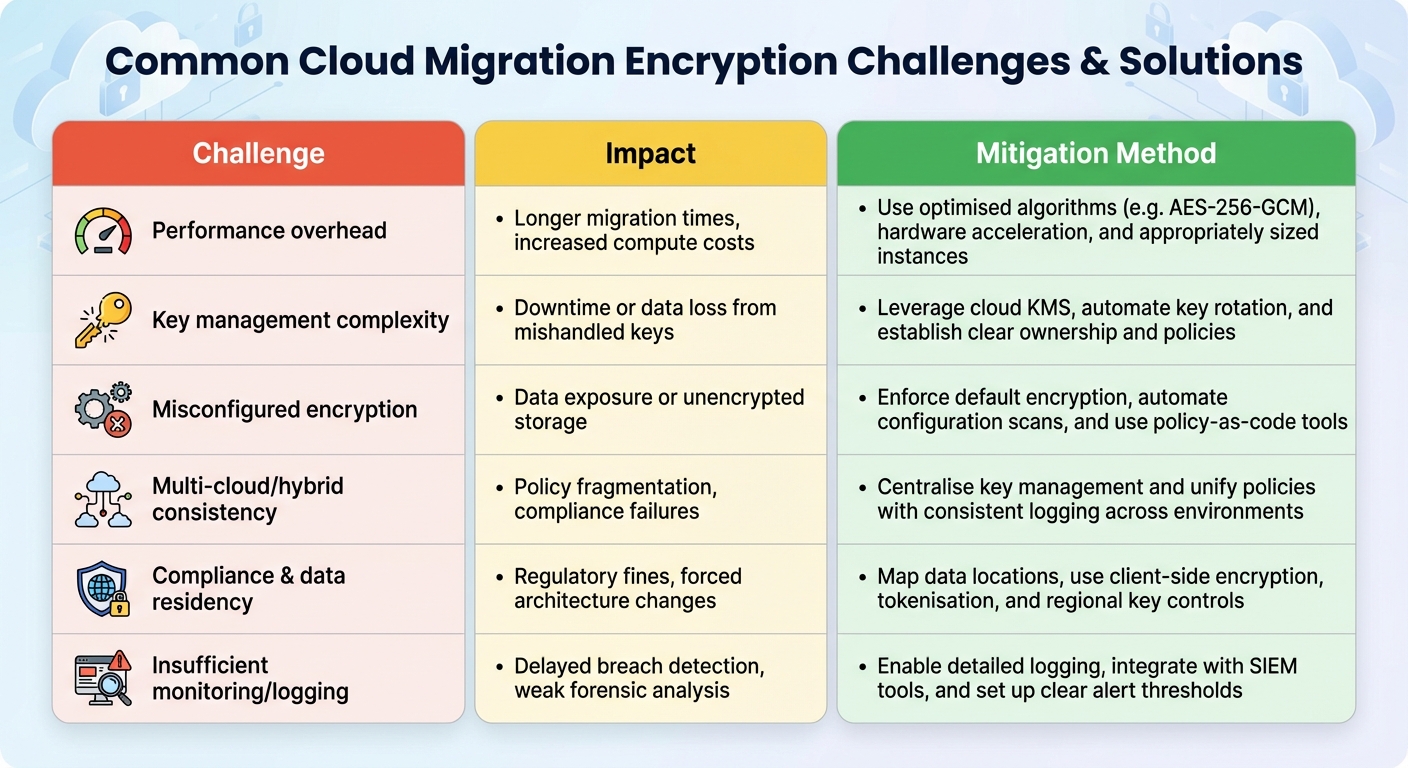 {Common Cloud Migration Encryption Challenges and Solutions}
:::
{Common Cloud Migration Encryption Challenges and Solutions}
:::
Encrypting data during cloud migration comes with several hurdles. One major challenge is the performance overhead - encrypting and decrypting large amounts of data can strain CPU resources and increase latency during bulk transfers, slowing down the process significantly [2].
Key management is another complex area. Juggling on-premises keys with cloud-based Key Management Services (KMS), while ensuring proper rotation schedules across different environments, can be a logistical headache. This complexity increases the risk of losing keys or exposing them to unauthorised access [2].
Misconfigured storage services also play a significant role in data breaches. Issues like unencrypted storage buckets or overly permissive database settings leave sensitive information exposed [9]. In hybrid or multi-cloud environments, maintaining consistent encryption policies across providers and on-premises systems becomes even more difficult. Problems such as fragmented key stores, inconsistent TLS configurations, and incomplete audit trails can make it harder to meet compliance requirements like UK GDPR or PCI DSS [9].
The shared responsibility model adds another layer of confusion. Many organisations mistakenly believe that cloud providers fully handle data security. In reality, it’s the customer’s job to configure encryption, manage keys, and control access. Without proper access controls, multi-factor authentication (MFA), and thorough logging, there’s still a risk of insiders or compromised accounts accessing plaintext data [2].
These challenges highlight the importance of robust post-migration monitoring and careful planning. Below is a summary of these challenges, their potential impacts, and strategies to address them.
Challenges Table
| Challenge | Impact | Mitigation Method |
|---|---|---|
| Performance overhead | Longer migration times, increased compute costs | Use optimised algorithms (e.g. AES-256-GCM), hardware acceleration, and appropriately sized instances [2] |
| Key management complexity | Downtime or data loss from mishandled keys | Leverage cloud KMS, automate key rotation, and establish clear ownership and policies [2] |
| Misconfigured encryption | Data exposure or unencrypted storage | Enforce default encryption, automate configuration scans, and use policy-as-code tools [9] |
| Multi-cloud/hybrid consistency | Policy fragmentation, compliance failures | Centralise key management and unify policies with consistent logging across environments [9] |
| Compliance & data residency | Regulatory fines, forced architecture changes | Map data locations, use client-side encryption, tokenisation, and regional key controls [7] |
| Insufficient monitoring/logging | Delayed breach detection, weak forensic analysis | Enable detailed logging, integrate with SIEM tools, and set up clear alert thresholds [2] |
To tackle these issues, start by benchmarking encryption performance before migration to ensure your systems can handle the load. Use advanced ciphers like AES-256-GCM, which strike a good balance between performance and security [2]. Centralising key management with cloud-native or multi-cloud KMS can simplify processes like key rotation and logging.
Make encryption the default for all data at rest and enforce TLS for data in transit. Tools like infrastructure-as-code and automated policy checks can help ensure these configurations are consistently applied. Strengthen security further with role-based access control (RBAC), MFA for admin accounts, and aggregated SIEM logs to quickly detect anomalies.
For tailored advice on building resilient encryption strategies and automating key management, check out Hokstad Consulting. Their expertise can help streamline your migration process and enhance your data security.
Conclusion
Protecting data during cloud migration demands a multi-layered strategy that begins well before any workloads are moved. Steps like pre-migration classification, encrypting data both in transit and at rest, effective key management, and ongoing monitoring are essential to safeguarding sensitive information [2][6]. Interestingly, misconfigurations - not weak cryptography - are the primary cause of cloud data exposure. This makes it crucial to embed encryption within a broader governance framework that also includes access controls, logging, and regular vulnerability testing [6][8][9].
This approach fits seamlessly within the shared responsibility model. While cloud providers handle the security of the infrastructure, organisations must focus on properly configuring encryption, managing keys, and enforcing least-privilege access [2][6][8]. For highly sensitive or multi-cloud data, client-side encryption and independent key management offer an extra layer of control, even though cloud-native encryption simplifies operations [2][9][10].
Taking it a step further, embedding encryption policies directly into infrastructure-as-code templates and CI/CD pipelines helps minimise human error and ensures consistent security checks. For instance, a tech startup was able to reduce its deployment time from six hours to just twenty minutes by automating these processes (Source: Hokstad Consulting, 2025).
Expert advice can make the difference between a secure, efficient migration and one riddled with vulnerabilities and compliance issues. Hokstad Consulting excels in creating encrypted architectures, automating key management, and integrating security into deployment workflows, potentially cutting infrastructure costs by up to 50% [1].
FAQs
What are the key advantages of using client-side encryption during cloud migration?
Client-side encryption boosts security by encrypting your data directly on your device before it's uploaded to the cloud. This approach reduces the chances of anyone gaining unauthorised access during transmission or while the data is stored in the cloud.
A key advantage is that you maintain complete control over the encryption keys, ensuring that even the cloud provider cannot access your information. This method is particularly useful for businesses needing to meet strict data protection regulations, keeping sensitive data private throughout the entire migration process.
How can I confirm that my cloud provider’s encryption meets compliance requirements?
To ensure your cloud provider's encryption aligns with compliance requirements, begin by verifying they adhere to established standards like GDPR, the UK Data Protection Act, and ISO 27001. Take the time to review their security certifications, audit reports, and encryption policies - covering both data at rest and in transit.
Regular compliance checks are equally essential, as regulations and technology can evolve over time. For more specific guidance, you might want to consult with professionals who specialise in cloud security and compliance. Their expertise can help you navigate the complexities and stay up to date.
How can I avoid misconfigurations during cloud migration?
When tackling cloud migration, reducing the risk of misconfigurations is crucial. Start by leveraging Infrastructure as Code (IaC). This approach ensures your configurations are consistent and repeatable, making it easier to avoid errors.
Before deployment, take the time to thoroughly test and validate all configurations. Catching potential issues early can save you from headaches down the line. It's also essential to have clear change management processes in place. These help you maintain control over updates and adjustments without creating chaos.
Don't overlook the value of monitoring tools either. They can help you quickly spot and fix configuration errors before they escalate. Finally, working alongside experienced professionals can make the entire migration process smoother and more secure, with solutions tailored to your specific requirements.
