Ensuring compliance in CI/CD pipelines is critical for secure and lawful software development. Automated compliance scanning helps organisations meet regulatory standards like UK GDPR, ISO 27001, and PCI DSS by embedding checks directly into the software development lifecycle. This process prevents non-compliant code from reaching production, reducing security risks and legal exposure.
Key Points:
- What it is: CI/CD compliance scanning ensures code and infrastructure meet legal and organisational standards during development and deployment.
- Why it matters: Protects against breaches, ensures adherence to laws like GDPR, and prevents incidents like the SolarWinds attack.
- How it works: Automated checks at multiple pipeline stages (e.g., pre-commit, build, and deployment) identify issues early.
- Best practices:
- Use tools like SAST, DAST, and software composition analysis.
- Integrate policy-as-code tools (e.g., Open Policy Agent) for automated enforcement.
- Maintain audit trails and a Software Bill of Materials (SBOM).
- Industry-specific needs: Tailor processes for sectors like healthcare and finance, which have stricter rules.
- Continuous monitoring: Regular scans and automated reporting ensure ongoing compliance and audit readiness.
By adopting a shift-left
approach and leveraging automation, teams can address compliance early, saving time and resources while protecting sensitive data and ensuring regulatory adherence.
Key Compliance Standards for CI/CD Pipelines
Common Standards: GDPR, ISO 27001, PCI DSS
When building audit-ready CI/CD pipelines, UK businesses must navigate several critical compliance frameworks. Among these, UK GDPR, ISO 27001:2022, and PCI DSS are particularly important.
UK GDPR mandates appropriate technical and organisational measures
to safeguard data, as outlined in Article 32. It emphasises Data Protection by Design, meaning security must be integrated from the very beginning of development workflows [6][7]. For CI/CD pipelines, this translates into risk-based testing and automated checks to ensure personal data is handled securely throughout the software development lifecycle.
ISO 27001:2022 introduces essential updates for modern development teams. This revision, the first major one since 2013, explicitly addresses the software development lifecycle (SDLC). It highlights secure coding practices and stresses the importance of separating development, test, and production environments [8]. Additionally, the standard requires organisations to conduct security testing on deployed code, ensuring vulnerabilities are identified and mitigated.
PCI DSS applies specifically to pipelines that handle payment card data. It sets out technical controls to protect sensitive cardholder information [6].
Beyond these foundational standards, the NIST Cybersecurity Framework provides guidance on managing cybersecurity risks through identification, protection, detection, response, and recovery. Meanwhile, the OWASP ASVS (Application Security Verification Standard) offers a structured framework for assessing web application security controls [9]. Both frameworks align well with CI/CD practices, particularly in their focus on continuous monitoring and automated testing.
These frameworks establish a solid foundation for securing CI/CD pipelines, but industry-specific requirements often demand additional measures.
Industry-Specific Compliance Requirements
Certain industries face unique compliance challenges that build on these broader standards. For example, healthcare organisations must adhere to stringent data protection rules, while financial services are subject to oversight from the Financial Conduct Authority (FCA) in addition to PCI DSS requirements [11]. These sector-specific regulations must be incorporated into CI/CD workflows to ensure comprehensive compliance.
The regulatory environment is constantly evolving. For instance, the Data (Use and Access) Act, which came into effect on 19th June 2025, is under review and may influence future UK GDPR guidance on data security and access [6]. This highlights the importance of maintaining agile CI/CD processes that can quickly adapt to new legal requirements. Similarly, the UK government's Cyber Essentials scheme, while not as comprehensive as ISO 27001, provides a basic set of technical controls that are often required for securing government contracts [6][7].
Supply chain security is also a critical consideration. With open-source software making up an average of 78% of all deployed web application code, organisations must ensure third-party components meet the same compliance standards [8]. Implementing Software Composition Analysis (SCA) tools in CI/CD pipelines can help identify vulnerabilities and manage licensing risks in these dependencies.
For products with heightened sensitivity, it’s advisable to seek expert guidance beyond standard CI/CD practices [3]. The complexities of these requirements are well summarised by this observation:
Everything in the updated [ISO] standard represents practices that every good software engineering shop should be doing, but very few are doing all of these things [8].
How to Create a DevSecOps CI/CD Pipeline
Integrating Compliance Scanning into CI/CD Pipelines
::: @figure 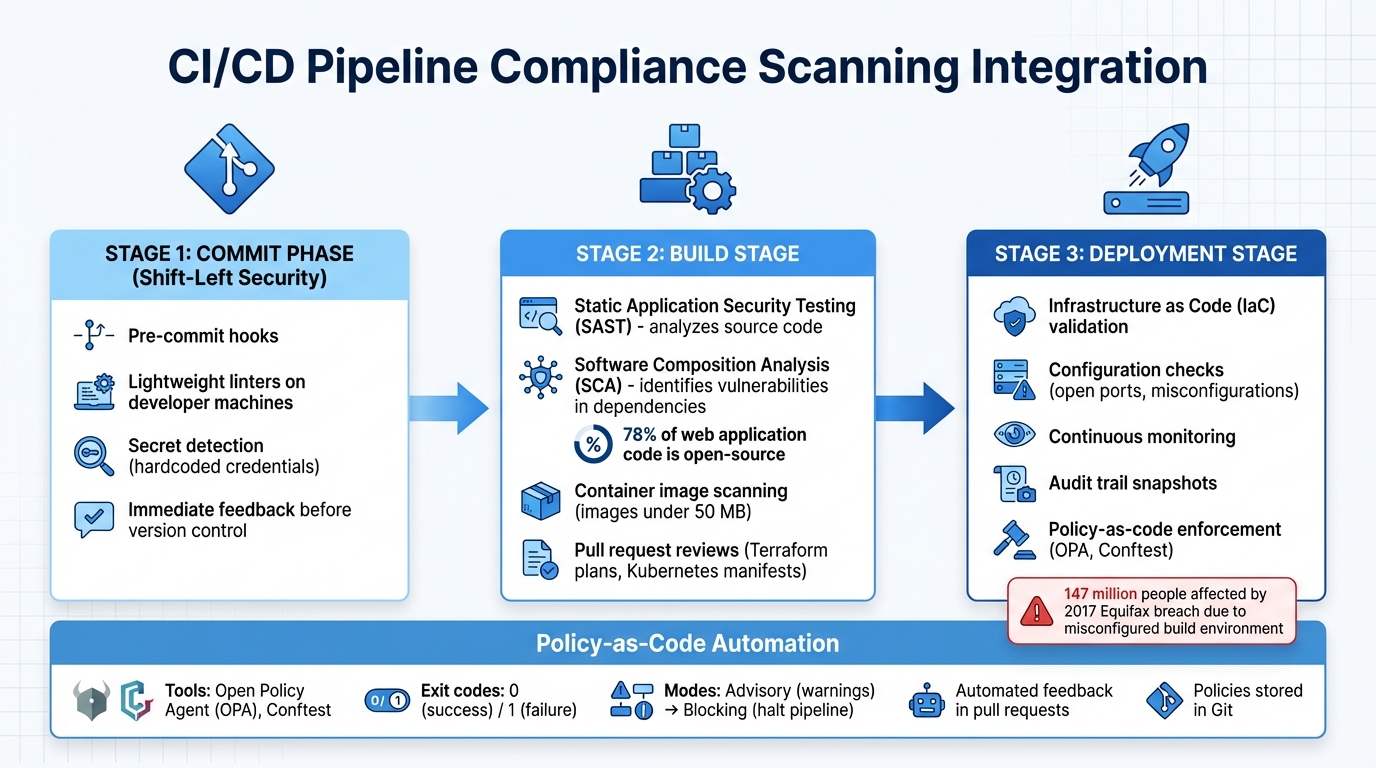 {CI/CD Pipeline Compliance Scanning Integration Points and Best Practices}
:::
{CI/CD Pipeline Compliance Scanning Integration Points and Best Practices}
:::
Shift-Left Security and Early Detection
Getting compliance right starts with addressing it early in the development process. By adopting a shift-left
approach, teams can embed policy checks at the very beginning of development. This means identifying and fixing issues when they’re cheapest and easiest to resolve. Instead of treating compliance as an afterthought, integrating checks into CI/CD pipelines makes it an automated and proactive part of development [12].
To make this approach effective, scanning should happen at multiple points in the pipeline. For instance, pre-commit hooks can run lightweight linters directly on developers' machines, offering immediate feedback before any code is committed [7, 19]. At the pull request stage, more thorough checks - like reviewing Terraform plans or Kubernetes manifests - can ensure configurations meet compliance standards before merging [12]. A stark reminder of the importance of pipeline security is the 2017 Equifax breach, which exposed data from 147 million people due to a misconfigured build environment [14].
Key Integration Points in Pipelines
For comprehensive compliance, checks need to cover all critical stages of the CI/CD pipeline. Here’s how this can be done:
- Commit Phase: Pre-commit hooks can catch hard-coded secrets or credentials before they even enter version control [7, 24].
- Build Stage: Static Application Security Testing (SAST) can analyse source code, while Software Composition Analysis (SCA) identifies vulnerabilities in third-party dependencies. Additionally, container images - ideally under 50 MB - should be scanned before deployment [7, 20, 24].
- Deployment Stage: Infrastructure as Code (IaC) templates, like those for Terraform or Kubernetes, can be validated to detect misconfigurations such as open ports. Continuous monitoring can then record audit trails by capturing snapshots of each analysis [1].
Teams can implement these checks using a mix of native CI/CD plugins, command-line tools, or REST APIs.
Automating Policy Enforcement
Automation takes compliance a step further by embedding policy-as-code
directly into the pipeline. Tools like Open Policy Agent (OPA) and Conftest allow teams to define compliance rules as executable code, which can then validate configurations automatically before deployment [15]. These tools rely on standardised exit codes - 0 for success and 1 for failure - so CI/CD platforms can block non-compliant builds without manual intervention [20, 21].
OPA is a great tool for implementing policy-as-code guardrails in CI/CD pipelines. With OPA, you can automatically verify configurations, validate outputs, and enforce organisational policies before code reaches production.
- Open Policy Agent [15]
To ease the transition when introducing new compliance rules, teams can start with an advisory mode that warns developers of issues without blocking workflows [12]. For high-priority issues, such as critical security gaps or potential cost overruns, blocking mode can be enabled to halt the pipeline until problems are resolved. Automated feedback loops that post scan results directly into pull request comments give developers the context they need to address issues effectively [12]. By storing compliance policies in Git and subjecting them to the same review processes as application code, teams can maintain consistency and ensure auditability, creating a foundation for continuous compliance [12].
Need help optimizing your cloud costs?
Get expert advice on how to reduce your cloud expenses without sacrificing performance.
Best Practices for Compliance-Driven Vulnerability Scanning
Layered Scanning for Complete Coverage
Using just one scanning tool can leave dangerous blind spots that attackers might exploit. To ensure thorough compliance scanning, it's essential to combine multiple approaches. Static Application Security Testing (SAST) checks source code for bugs and known vulnerabilities, while Software Composition Analysis (SCA) highlights issues in third-party libraries. For running applications, Dynamic Application Security Testing (DAST) is a better fit, often producing fewer false positives compared to SAST [4]. Depending on your environment, you might also need container image scanners, API fuzzing tools, or secret detection software to uncover hardcoded credentials [13].
For infrastructure, scanners can identify outdated operating system patches and weak passwords, while web application scanners focus on custom code vulnerabilities and OWASP Top 10 risks [2]. Inline scanning is another useful layer, ensuring that non-compliant container images are blocked from reaching production environments [10]. Modern tools also deploy location fingerprints
to track vulnerabilities across file changes, helping avoid duplicate alerts when code is moved [13].
Once these layered scanning techniques are in place, the next step is to focus on managing the results and addressing vulnerabilities strategically.
Handling Scan Results and Prioritising Remediation
After completing scans, the real challenge lies in managing and remediating the vulnerabilities effectively.
Start by prioritising vulnerabilities using a severity scale - ranging from Minor to Critical. This ensures that systems exposed to the internet or handling sensitive data are dealt with immediately [16] [18]. Keeping a vulnerability register is vital for tracking details like status (e.g., Open, Closed, Mitigated), severity, and remediation actions. This not only aids in remediation but also ensures you're prepared for audits.
To streamline the process, integrate scan results into developers' existing workflows, such as their communication tools or platforms. Fine-tune scanners to minimise false positives, which helps maintain developer trust in the process [17]. Configure CI/CD pipelines to halt deployments if they detect policy violations [13]. Once a vulnerability is fixed, create a regression test to ensure it doesn’t reappear [17].
Continuous Monitoring and Audit Readiness
Automating scans is key to staying ahead. Set up scans to run on a schedule, on demand, or after new builds and deployments [2]. Infrastructure scans should occur at least once a month or immediately after addressing a critical vulnerability [2]. Application-level scans, on the other hand, should run whenever source code is updated or a new version is deployed.
Maintaining a Software Bill of Materials (SBOM) in formats like CycloneDX or SPDX provides a clear inventory of all components and dependencies, which is invaluable for audits [5]. Centralising vulnerability management and remediation in one portal can simplify audit preparations [2]. Be sure to document excluded assets in your risk register for transparency. Finally, configure tools to generate reports in multiple formats - such as CSV, JSON, or HTML - so they can be easily shared with both technical and non-technical stakeholders [5].
Vulnerability scanning affords an organisation the ability to keep pace with individuals and groups intent on compromising systems, many of which use similar tools and techniques to discover security flaws.
Achieving Continuous Compliance with Hokstad Consulting

Hokstad Consulting's Approach to Compliance Scanning
Hokstad Consulting supports UK businesses by embedding security controls directly into their CI/CD pipelines. Their DevOps transformation services focus on identifying and deploying the most suitable vulnerability detection tools - such as OWASP ZAP, Trivy, and Clair - tailored to your infrastructure, budget, and the specific regulatory requirements of UK laws. They also guide organisations in adopting Policy-as-Code (PaC) solutions using engines like Open Policy Agent (OPA) and Kyverno, automating compliance checks for frameworks like GDPR, PCI DSS, and SOC 2 within Kubernetes environments.
Their expertise extends to creating custom integrations for secrets management and automated compliance reporting, spanning both legacy systems and cloud-native architectures. Hokstad Consulting implements zero-trust architecture principles, which include deny-all network policies by default and robust identity management systems, ensuring proper network segmentation. They also ensure Kubernetes environments are equipped with detailed audit trails and data loss prevention measures, crucial for meeting GDPR's 72-hour breach notification requirement. By centralising policy management in version-controlled repositories, they promote consistency across teams and enable shift-left security practices through pre-merge and pre-deployment validations. This cohesive approach lays the groundwork for robust and scalable security measures.
Tailored Solutions for UK Businesses
Hokstad Consulting takes their expertise further by offering solutions specifically designed for UK businesses. They specialise in data residency and sovereignty controls, developing pipelines that ensure sensitive data, logs, and build artefacts remain within UK borders. This approach addresses concerns around outsourcing critical infrastructure to international providers while ensuring compliance with UK GDPR and maintaining local operational independence.
To start, they conduct thorough compliance gap analyses, identifying vulnerabilities in existing CI/CD practices. From there, they create tailored remediation strategies to address these gaps. Their pricing models are designed with flexibility in mind, offering options such as a no savings, no fee
structure, retainers, and free initial consultations for vulnerability and compliance assessments. Hokstad Consulting provides unbiased, expert advice, helping organisations choose between PaC engines like OPA and Kyverno based on their team's skill sets and the complexity of UK regulatory requirements.
Conclusion
Key Takeaways
For UK CI/CD pipelines, compliance-driven vulnerability scanning isn't optional - it’s a necessity. Implementing shift-left security practices and automated scanners helps identify vulnerabilities early, ensuring adherence to UK GDPR, PCI DSS, and ISO 27001. This approach not only reduces legal risks but also protects your organisation's reputation. By integrating security controls directly into your deployment workflows, you can achieve continuous compliance without disrupting operations.
A layered security strategy strengthens this process. Start with regular infrastructure scans - ideally conducted at least once a month - and complement these with tools designed for specific areas like APIs and containers. Automating policy enforcement with tools such as Open Policy Agent or Kyverno can prevent non-compliant deployments from going live. This frees up your security team to focus on more complex threats rather than routine vulnerabilities.
Beyond scanning, audit readiness is crucial for maintaining compliance. Automated tools can generate detailed reports and audit trails that align with legal requirements, offering transparency and accountability. The Information Commissioner’s Office often considers technical measures like audit trails and encryption when assessing penalties for data breaches. Providing developers with real-time feedback and remediation guidance tailored to their programming language ensures issues are resolved quickly and efficiently.
UK businesses can also gain an edge by leveraging specialist support tailored to local regulations. Companies like Hokstad Consulting bring a deep understanding of UK-specific compliance needs, blending DevOps expertise with regulatory knowledge. This ensures organisations can uphold stringent security standards while maintaining operational agility and effectiveness.
FAQs
Why should compliance scanning be part of your CI/CD pipelines?
Integrating compliance scanning into your CI/CD pipelines is a smart way to catch vulnerabilities and regulatory issues early - before they ever reach deployment. By addressing these problems upfront, you can maintain security and meet compliance requirements without disrupting the pace of development.
When compliance checks are built into every code change, you create a system of continuous monitoring. This means developers get instant feedback right within their workflow, helping them fix issues quickly. Not only does this save time, but it also boosts code quality and keeps sensitive data secure by conducting all analysis locally.
Making compliance scanning a core part of your CI/CD process enables quicker, safer software releases while ensuring your product aligns with industry standards and regulations.
How can businesses in the UK ensure their CI/CD pipelines comply with GDPR and other regulations?
To align with GDPR and other regulatory requirements in CI/CD pipelines, businesses in the UK need to implement strong security protocols and keep detailed records. This involves conducting regular risk assessments, using protective measures such as encryption and pseudonymisation, and scheduling routine vulnerability scans to identify potential weaknesses.
It's also essential to have a well-defined information security policy in place. For processes considered high-risk, performing Data Protection Impact Assessments (DPIAs) is crucial. Regular testing and audits of pipeline controls further ensure that security measures are effective. Integrating these practices into your CI/CD workflows not only bolsters compliance but also helps reduce potential risks.
What are the best tools for automating compliance policies in CI/CD pipelines?
Automating compliance policies within CI/CD pipelines plays a key role in upholding security and operational standards. Among the top tools available, Open Policy Agent (OPA) stands out, especially when paired with Conftest, as it enables seamless policy-as-code implementation. Another versatile option is Trivy, which integrates smoothly with CI/CD platforms and covers a range of security needs. For those focusing on scanning infrastructure-as-code (IaC) configurations, Checkov is a popular and reliable choice. Meanwhile, Snyk excels at identifying vulnerabilities in dependencies and code, offering comprehensive security checks.
Each tool brings its own strengths to the table, so the right choice will depend on the specific requirements of your pipeline and compliance objectives. By incorporating these tools, you can maintain regulatory standards while keeping your development process efficient and uninterrupted.
