In the UK, encryption isn't optional for organisations handling personal data. It's a legal requirement under UK GDPR, PCI DSS, and ISO 27001. Encryption protects sensitive information from risks like data breaches, unauthorised access, and accidental loss. But compliance isn't just about using encryption - it’s about using it correctly.
Here’s what you need to know:
- Encryption is mandatory: Regulations like GDPR require encryption as a safeguard for personal data.
- Use modern standards: Algorithms like AES-256 for data at rest and TLS 1.3 for data in transit are recommended.
- Key management matters: Secure generation, rotation, and destruction of encryption keys are critical.
- Retention and deletion: Automate data retention and securely delete information when no longer needed.
- Regular reviews: Encryption methods must be tested and updated to stay effective against new threats.
Failing to meet these standards can lead to hefty fines and reputational damage. This checklist outlines practical steps to help ensure your encryption strategy aligns with compliance requirements.
Cryptographic Key Management Practices
Creating an Encryption Policy
::: @figure 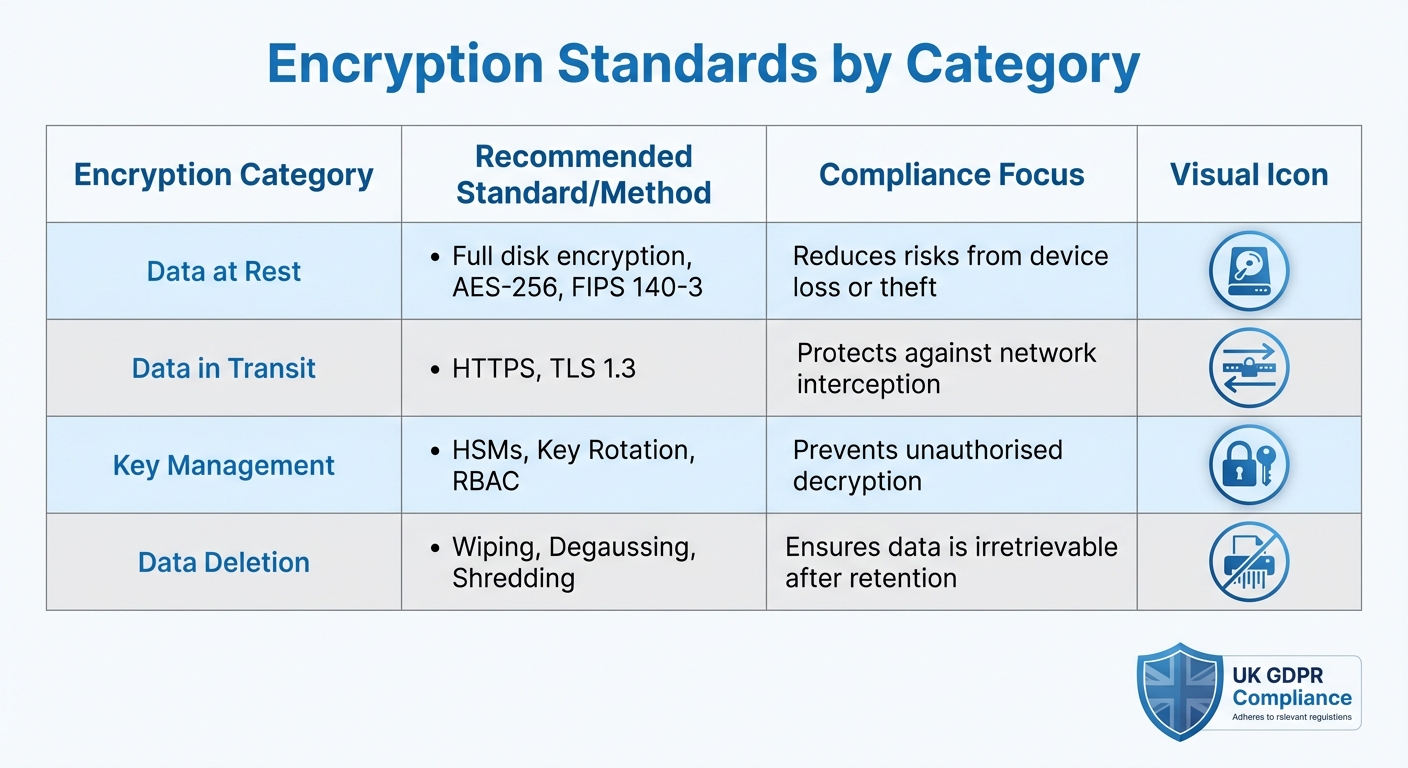 {UK GDPR Encryption Standards by Data Category}
:::
{UK GDPR Encryption Standards by Data Category}
:::
A well-crafted encryption policy turns regulatory guidelines into actionable steps. While the UK GDPR doesn't explicitly require encryption in all cases, Article 32 highlights encryption as an appropriate technical measure
to be considered, depending on factors like technological advancements, costs, and the risks to individuals' rights and freedoms [7]. A documented policy is crucial for demonstrating compliance during audits or reviews by the Information Commissioner's Office (ICO).
After classifying your data, outline the encryption standards for each category - for instance, AES-256 for data at rest and TLS 1.3 for data in transit. Maintain a detailed inventory of encryption tools and processes [4]. This inventory is invaluable for responding quickly if vulnerabilities are found in a particular algorithm or implementation. Additionally, define data classification and retention rules to structure your encryption policy effectively.
Set Up Data Classification and Retention Rules
Data classification and retention rules are the backbone of an encryption policy. Start by categorising personal data based on its sensitivity and the legal basis for processing it. Different data types demand encryption levels that match their sensitivity and associated risks. Your retention schedule should specify how long each data category will be kept, the legal or business rationale for that duration, and the steps to take once the retention period ends - whether it's deletion, anonymisation, or archiving [6][8].
Automated systems can streamline this process by tagging records with retention dates and triggering deletion or review actions without manual input. This not only improves compliance but also reduces human error and operational inefficiencies [5][6]. Keeping data only as long as necessary lowers compliance risks and reduces the volume of encrypted data that needs management. Periodic data reviews, or weeding
exercises, can further minimise exposure by removing outdated or unnecessary information [6].
Record Encryption Standards and Methods
Once you've classified your data, the next step is to document the encryption methods for each category. Use trusted, well-established algorithms instead of creating custom cryptography. The ICO advises:
Encryption is a widely available measure and is relatively easy to implement. There are many low-cost, easily deployable encryption tools and solutions.[7]
Specify standards like FIPS 197 (AES) for securing data at rest and TLS 1.3 for protecting data in transit. Avoid outdated protocols such as SSL due to their known vulnerabilities [2][4]. For cryptographic modules, align with FIPS 140-3 standards [2][7].
| Encryption Category | Recommended Standard/Method | Compliance Focus |
|---|---|---|
| Data at Rest | Full disk encryption, AES-256, FIPS 140-3 | Reduces risks from device loss or theft [2][7] |
| Data in Transit | HTTPS, TLS 1.3 | Protects against network interception [2] |
| Key Management | HSMs, Key Rotation, RBAC | Prevents unauthorised decryption [4][7] |
| Data Deletion | Wiping, Degaussing, Shredding | Ensures data is irretrievable after retention [5] |
Clarify when to use full disk encryption, such as for laptops and USB drives, versus file-level encryption for specific sensitive datasets. Include guidelines for using Hardware Security Modules (HSMs) to store encryption keys and implementing Role-Based Access Control (RBAC) to enforce the principle of least privilege. Ensure decryption keys are never stored on the same device as the encrypted data they protect [7].
Manage Key Lifecycles
Your encryption policy should also address the entire lifecycle of encryption keys, from secure generation and distribution to rotation, revocation, and destruction [4]. Define the lifespan of each key, ensuring they are rotated, archived, or securely deleted at the end of their lifecycle [4]. The ICO highlights the risks of poor key management:
If you lose a decryption key it means that no-one, including you, is able to decrypt the data. You should mitigate this risk through proper key management, file storage or backup procedures.[7]
Simplify key management by implementing a hierarchy, where a top-level key encrypts lower-level keys. This approach enhances security and makes management more efficient [4]. Establish clear procedures for revocation, allowing new key pairs to be created immediately if an existing key is compromised [4]. It's also essential to enforce separation of duties so no individual has access to both encrypted data and its decryption keys [7]. Stay updated on security advisories to respond promptly to vulnerabilities in encryption algorithms, and have a documented plan for transitioning to new methods if current ones become outdated [4]. These steps help ensure compliance with UK data protection laws.
Applying Secure Encryption Standards
Once you've defined your encryption policy, the next step is to select and enforce encryption methods that comply with UK GDPR requirements. Article 32 mandates organisations to implement appropriate technical and organisational measures
that align with the current state of technology, costs, and associated risks [7]. This means opting for widely recognised, industry-standard solutions rather than outdated or proprietary methods. These standards form the backbone of secure algorithms and effective certificate management.
Failing to adhere to proper encryption standards can have serious consequences. For instance, in 2013, Glasgow City Council was fined £150,000 after unencrypted laptops containing data on 20,143 individuals were lost [9]. Similarly, Greater Manchester Police faced a £150,000 fine in 2012 after an unencrypted USB stick with data on over 1,000 people was stolen [9]. These incidents highlight that encryption is not just a technical safeguard but a key compliance requirement.
Choose Strong Algorithms and Protocols
The strength of your encryption hinges on the algorithms and protocols you use. For data at rest, AES-256 (FIPS 197) is the gold standard. It offers an almost unimaginable number of possible keys, making brute-force attacks unfeasible with current technology [4]. Avoid outdated options like DES, which no longer provide adequate security [4].
For data in transit, ensure all web-facing services use TLS 1.3 and enforce HTTPS on every page [10]. While TLS 1.2 is still acceptable if configured to prevent downgrade attacks, older protocols must be avoided entirely [2][10]. The ICO has made its stance clear:
You must not use any version of SSL anymore, because they suffer from well-known vulnerabilities[2].
To further secure your connections, implement HTTP Strict Transport Security (HSTS), which ensures all traffic is automatically routed through HTTPS [10].
Maintain Certificate and Key Strength
Strong algorithms alone are not enough - they must be supported by robust certificates and keys. Certificates should comply with the X.509 standard and use at least 2,048-bit encryption [11]. Outdated hash algorithms like MD5 and MD4, which are vulnerable to attacks, should be replaced with SHA-256 or stronger alternatives [12].
Effective certificate management is critical. Renew certificates midway through their validity period to minimise risks [12]. Maintain a cryptographic inventory that tracks certificate locations, expiry dates, and licensing [11]. Your Public Key Infrastructure (PKI) should synchronise with a trusted time source to enforce strict validity periods [11]. Regularly review your encryption methods - at least once a year - to ensure they remain effective against evolving threats and advancements in computing power [4]. Staying vigilant helps keep your encryption resilient and up to date.
Controlling Access and Authentication
Encryption loses its effectiveness if decryption keys fall into the wrong hands. To prevent this, strict access controls must complement secure encryption standards, ensuring only authorised individuals handle these critical keys. According to the UK GDPR, organisations are obligated to process personal data in a manner that ensures appropriate security of the personal data, including protection against unauthorised or unlawful processing and against accidental loss, destruction or damage, using appropriate technical or organisational measures
[7][13]. This means encryption must be paired with robust access management as part of a layered security strategy [7]. Simply put, securing who can access sensitive keys is just as important as selecting the right encryption algorithms.
Access decisions should follow the principle of least privilege. This involves limiting permissions to only what is necessary for specific tasks and enforcing a separation of duties to prevent any single individual from controlling both encryption keys and sensitive data [7]. These practices work hand in hand with encryption standards to create a cohesive security framework.
Require Multi-Factor Authentication
Multi-Factor Authentication (MFA) should be a non-negotiable requirement for anyone accessing key management systems, encryption tools, or certificate issuance platforms [11]. Relying solely on passwords creates a single point of failure. Instead, authentication should involve alphanumeric passcodes with a mix of letters and symbols, which are far more resistant to brute-force attacks than simple numeric PINs [9].
To further enhance security, decryption keys should never be stored on paper or sent alongside encrypted files via email attachments [9]. Keep them separate and secure to minimise risks.
Limit Access to Necessary Personnel
Strong authentication is just the beginning - access to encryption resources should also be tightly restricted. Only individuals who need access for their specific roles should be granted permissions. Keys should be stored in FIPS-validated Hardware Security Modules (HSMs) or Trusted Platform Modules (TPMs), which provide secure environments that prevent keys from being exported in plain text [14][11]. Human operators should never directly access unencrypted key material; instead, programmatic access via secure APIs or managed services is the safer route [14].
Document authorised users, perform quarterly audits to prevent privilege creep, and block unauthorised data extraction by restricting access to ports for unencrypted USB devices [4][9]. When employees change roles or leave the organisation, promptly update their access rights through a formal movers and leavers process. These measures not only align with regulatory requirements but also streamline access management, making your encryption strategy more secure and compliant.
Managing Data Retention and Deletion
Once encryption standards and key management are in place, the next step in compliance is managing data retention and ensuring secure deletion. While encryption protects data, compliance also requires that it is deleted promptly when no longer needed. According to the UK GDPR's storage limitation principle, organisations must only keep personal data for as long as it serves its original purpose. To meet this requirement, it's essential to establish clear retention schedules and implement secure methods for data deletion.
Retention schedules should align with your data classification policies [8][6]. Together with encryption protocols, these measures form a comprehensive compliance strategy.
Set Up Automated Retention Rules
Automating data retention and deletion processes can significantly reduce the risk of errors. Configure systems to automatically delete data once the retention period expires, including information stored in archives, recycle bins, and backups [5]. Where feasible, integrate approval workflows, requiring management sign-off before final deletion. Assign a team member to oversee disposal logs and verify destruction certificates to ensure accountability [6][5].
It's important to regularly review these automated rules to ensure they comply with any updates to legal requirements or changes in how data is processed [8][6]. If automated systems fail to delete records as scheduled, treat this as a data incident and take immediate corrective measures [5].
Once automation is in place, focus on using effective techniques to permanently erase data.
Use Secure Deletion Techniques
Simply deleting files isn’t enough, as data can often be recovered. For encrypted data, cryptographic erasure provides a reliable solution. This method involves setting finite lifespans for encryption keys and securely deleting the decryption key once the retention period ends, rendering the data unreadable [4]. As the Information Commissioner's Office (ICO) explains:
You could configure keys to have a finite lifespan and for processes to be in place to generate a new key and re-encrypt the data. You can then archive the old key and securely delete it when you no longer require it[4].
For physical storage media, methods like device-wiping software, degaussing for magnetic drives, or hardware shredding are effective for end-of-life devices [5]. If you outsource disposal, ensure contracts include security provisions, audit rights, and require destruction certificates to confirm complete and secure disposal [5].
In cases where permanent deletion isn’t technically feasible, isolate the records in a restricted-access environment to prevent unauthorised use [5].
Auditing, Monitoring, and Updates
Under UK GDPR, regular testing and reviews are essential to ensure encryption methods remain effective [4]. What’s secure today might not hold up tomorrow as computing power increases and new attack strategies emerge.
Take DES, for instance. Once considered secure, it quickly became outdated as technology advanced [4]. This highlights why periodic audits are critical to staying ahead of evolving threats.
Conduct Regular Audits
Set up a formal schedule to review your encryption practices - an annual audit should be the minimum standard [4]. Maintain an up-to-date inventory of all encryption tools, processes, and algorithms used across your organisation. This way, you can swiftly evaluate your security measures when new vulnerabilities arise.
During these audits, check that key lifecycle management is properly handled [4]. Confirm that automated systems are correctly purging encrypted records once their retention periods are up. If you rely on third-party providers for data destruction, cross-check their destruction certificates with your hardware logs to ensure secure disposal [5].
Track Encryption Activities
Keeping logs of key usage, access attempts, and encryption events provides a clear audit trail. This not only reinforces accountability but also helps identify unauthorised access. Regularly monitor for protocol vulnerabilities, such as downgrade attacks, where an attacker forces a server to revert to less secure settings [10]. Pair encryption with integrity checks to detect any tampering, even if the data hasn’t been decrypted [7].
Implement role-based access control and follow the principle of least privilege to limit access to encryption keys. By separating duties, no single individual can access both encrypted data and its keys, reducing the risk of internal breaches [7].
Insights from these audits should feed directly into timely updates to your encryption policies.
Update Policies Regularly
Encryption standards can develop vulnerabilities at any time, making it crucial to update policies promptly [4]. Subscribe to technical bulletins for alerts on new encryption vulnerabilities. The Information Commissioner’s Office advises:
You must consider an appropriate review period for your use of encryption[4].
Prepare a documented transition plan to switch to new encryption methods if current standards are compromised. Significant regulatory changes, such as the Data (Use and Access) Act, which came into effect on 19 June 2025, should trigger immediate policy reviews [1][3]. Finally, ensure server configurations block outdated protocols - SSL is insecure and must not be used, while TLS 1.2 and 1.3 remain the recommended standards [10].
Conclusion
To align encryption with compliance, it’s essential to establish a clear policy detailing when and how to use trusted algorithms like AES-256 and protocols such as TLS 1.3 for protecting data both at rest and in transit [2][4].
Effective key management is another cornerstone of secure encryption. This includes keeping decryption keys stored separately, using Hardware Security Modules (HSMs), and implementing key rotation with defined lifespans. These steps significantly reduce the risk of data breaches [7].
Restrict access to encryption keys by enforcing the principle of least privilege. Use role-based access control (RBAC) combined with multi-factor authentication (MFA) to ensure only authorised individuals can access sensitive keys [7].
Encryption strategies should also align with your data retention policies. By automating retention rules, you can ensure encrypted records are deleted once their retention periods end. Techniques like cryptographic erasure or hardware shredding further guarantee that data isn’t retained longer than necessary. This integration of encryption, retention, and secure deletion supports both compliance and robust data protection [5].
Regularly reviewing your encryption practices is crucial. Maintain a cryptographic inventory, stay alert to emerging threats, and prepare transition plans for adopting updated standards when required. This proactive approach ensures your encryption methods remain aligned with the UK GDPR’s requirements for appropriate technical and organisational measures [7][13].
FAQs
What are the essential steps for developing an encryption policy that meets compliance requirements?
To develop an encryption policy that aligns with compliance requirements, start by pinpointing the regulations and standards relevant to your organisation. Establish clear goals for encryption, such as safeguarding sensitive information and ensuring secure data storage, retention, and deletion practices. Choose encryption algorithms and key lengths that adhere to compliance rules and reflect current industry standards.
Implement robust key management procedures to prevent unauthorised access to encryption keys. Make it a priority to regularly review and adjust your encryption methods to stay ahead of changing regulations and emerging threats. Additionally, ensure your team is well-trained in the importance of encryption and how to apply it effectively in their daily responsibilities.
What steps should organisations take to manage encryption keys effectively?
To handle encryption keys properly, organisations need to focus on secure storage to keep keys safe from unauthorised access. Regularly rotating keys is another essential step, as it lowers the chances of a key being compromised. At the same time, strict access controls ensure that only authorised individuals have the ability to interact with these keys.
Automating key management processes can make a big difference. It helps enforce least privilege access, reducing the risk of mistakes caused by human error. On top of that, keeping an eye on key usage can uncover unusual activity and ensure compliance with data protection laws. By adopting these measures, organisations can strengthen their encryption efforts and protect sensitive data effectively.
What are the best practices for encrypting data both at rest and in transit?
To maintain strong encryption, it's important to safeguard data both when stored and during transmission by following proven standards and practices. The Advanced Encryption Standard (AES), particularly with large key sizes like 256-bit, is a widely trusted choice for securing data. Additionally, cryptographic keys must be stored securely, rotated periodically, and managed with care to prevent unauthorised access.
Equally crucial is ensuring that encryption methods align with applicable compliance requirements and industry regulations. Regularly reviewing and updating encryption protocols not only strengthens security but also ensures they keep pace with changing standards.
