API gateways are critical in managing and securing modern applications, but they face growing threats like Broken Object Level Authorisation (BOLA), shadow APIs, and business logic attacks. This article evaluates five leading API security tools - Levo.ai, Traceable.ai, Salt Security, Akamai API Security, and Noname Security - based on their detection capabilities, integrations, strengths, weaknesses, and pricing.
Key Highlights:
- Levo.ai: Strong in AI-specific risks (e.g., prompt injection) with eBPF sensors for full visibility. Limited support for non-AWS gateways. Pricing requires consultation.
- Traceable.ai: Behavioural analytics for anomalies, flexible deployment options, and real-time blocking. AI learning phase needed; starts at £16,000/year for 250 endpoints.
- Salt Security: Focuses on behavioural baselines for subtle threats like
low-and-slow
attacks. Relies on gateways for blocking. Pricing is custom. - Akamai API Security: Low-latency protection using its CDN, but real-time blocking requires additional tools. Pricing tailored to enterprise needs.
- Noname Security: Full lifecycle API security with posture management and SDLC testing. API-layer focus may miss deeper system-level issues. Custom pricing.
Quick Comparison:
| Tool | Key Strengths | Weaknesses | Pricing |
|---|---|---|---|
| Levo.ai | AI-specific risk detection, no egress costs | Limited non-AWS support, setup complexity | Custom quote required |
| Traceable.ai | Real-time anomaly detection, flexible deployments | AI learning phase, some findings lack detail | £16,000/year (Discovery) |
| Salt Security | Behavioural analysis, fast insights | Gateway reliance, cloud-focused | Custom quote required |
| Akamai | CDN-based low-latency protection | Requires additional tools for blocking | Custom quote required |
| Noname | Shadow API discovery, SDLC testing | Limited system-level visibility | Custom quote required |
Each tool addresses API security challenges differently. Choosing the right one depends on your organisation’s priorities, such as AI risk management, compliance, or real-time blocking.
::: @figure 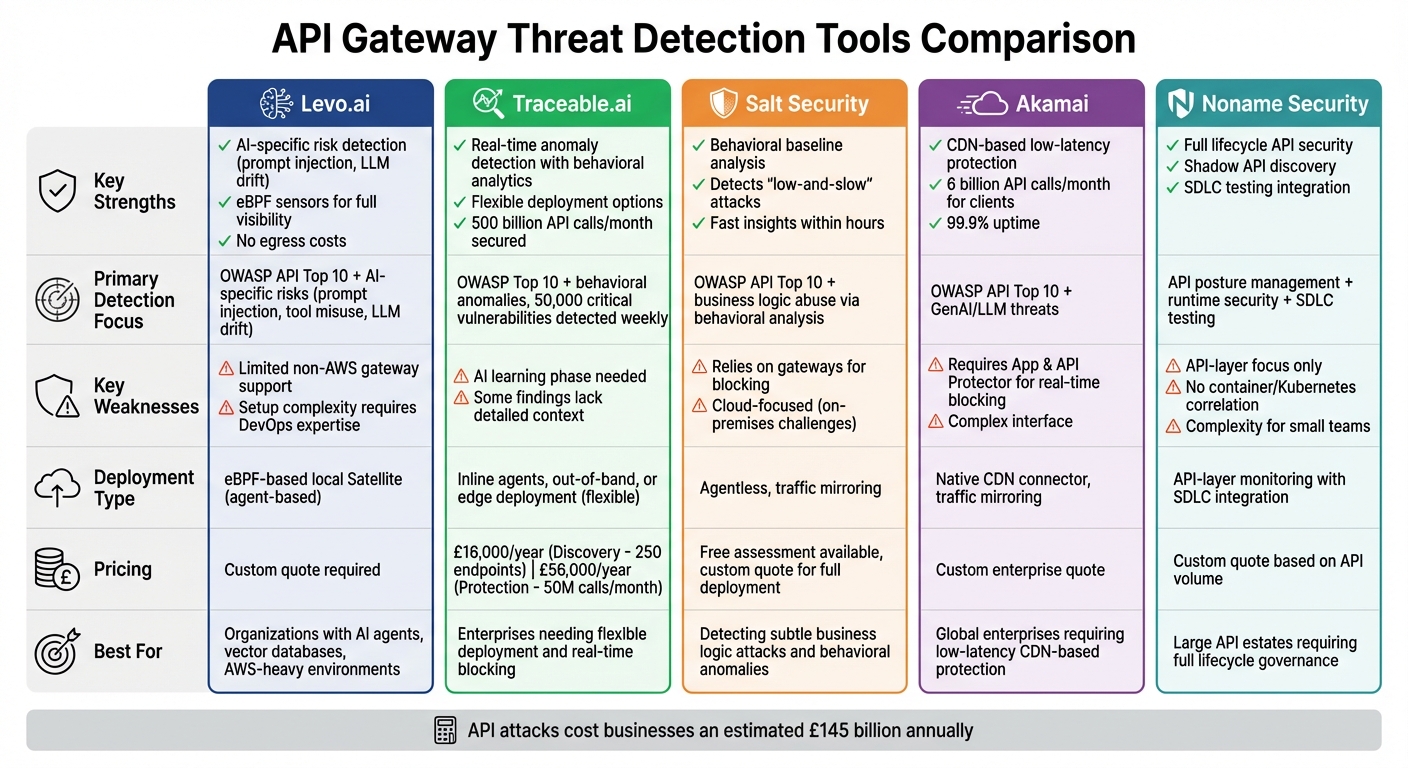 {API Gateway Threat Detection Tools Comparison: Features, Pricing and Strengths}
:::
{API Gateway Threat Detection Tools Comparison: Features, Pricing and Strengths}
:::
1. Levo.ai
Detection Coverage
Levo.ai tackles the entire range of OWASP API Security Top 10 vulnerabilities, including Broken Object Level Authorisation (BOLA), Broken Authentication, and Mass Assignment attacks [5][7]. It goes beyond standard web threats by identifying business logic abuse, SQL and NoSQL injection issues, and insecure configurations that traditional tools often miss [5][7].
What sets Levo apart is its ability to address AI-specific risks, such as prompt injection, tool misuse, collusion, and LLM drift. This makes it a great fit for organisations working with AI agents and vector databases [4]. The platform also detects sensitive data like PII, PHI, and secrets within API payloads, AI prompts, and vector queries [4]. Using kernel-level eBPF sensors, Levo captures both north-south perimeter traffic and east-west microservice communications without requiring code changes or sidecar agents [3]. This approach automatically uncovers all API endpoints, including undocumented ones [6]. These capabilities integrate seamlessly into Levo's broader security framework, which leverages key integrations for enhanced protection.
Key Integrations
Levo integrates deeply with AWS API Gateway by leveraging Log and CloudFront Lambda. This enables it to instrument external endpoints and auto-generate OpenAPI and Swagger specifications. It also connects with CI/CD pipelines like GitHub, Jenkins, GitLab, and Bitbucket, allowing security validations for every pull request [6][9]. This shift-left
approach lets teams simulate exploits - such as BOLA and IDOR attacks - before APIs go live [5].
Its eBPF-based monitoring ensures full visibility without adding performance overhead, while support for modern AI stacks like LLMs, Vector Stores, and Model Context Protocol (MCP) servers makes it compatible with cutting-edge environments [4][9]. Additionally, Levo generates Postman collections for manual testing and integrates with tools like Jira for ticketing and Slack for alerts, streamlining remediation processes [6][8][9].
Strengths
Levo operates with minimal latency, avoiding the delays often seen with traditional WAFs [3]. Unlike older systems that rely on opaque signatures, Levo uses transparent white-box
rules based on runtime API context. This approach is far more effective, as traditional WAFs have been shown to miss up to 88% of actual attacks [3].
Levo has raised the bar for API security monitoring and testing. Their eBPF sensor is a game-changer for gaining valuable insights into our APIs.- Saran Makam, VP of Information Security and IT, Poshmark [4]
The Levo Satellite performs all traffic analysis locally, keeping sensitive data within the customer's environment. This not only ensures data privacy but also eliminates costly egress fees that can run into hundreds of thousands of pounds [3]. Automated API inventory management addresses shadow APIs, while the platform's ability to handle complex authentication methods - like OAuth2, JWT, and mTLS - reduces failed security tests caused by expired tokens [5].
Weaknesses
Although the integration with AWS API Gateway is well-developed, support for other major gateways is still in progress [6]. Deployment requires the installation of a local Satellite and eBPF sensor, which may pose challenges for teams with limited DevOps expertise [3]. Additionally, pricing details are not publicly available, requiring potential customers to schedule a demo for enterprise quotes [3][5].
Pricing Model
Levo.ai eliminates expensive data egress costs by performing all traffic analysis locally within the customer's network [3]. However, specific pricing tiers and enterprise options are only available through direct consultation with the vendor [3][5].
| Feature | Levo.ai Runtime Protection | Traditional WAF |
|---|---|---|
| Latency | Sub-millisecond | Often tens of milliseconds |
| Traffic Coverage | North-South & East-West | Primarily North-South |
| Data Privacy | Local analysis (zero egress) | Often requires shipping data to cloud |
| Rule Type | Transparent white-box (tunable) | Opaque black-box (signatures) |
2. Traceable.ai
Detection Coverage
Traceable.ai addresses vulnerabilities listed in the OWASP Web and API Top 10, while also tackling threats like business logic abuse, zero-day attacks, and sensitive data leaks [10]. The platform uses context-aware behavioural analytics and machine learning to monitor user behaviour, API interactions, data flow, and code execution. By establishing a behavioural baseline, it can trigger real-time alerts for anomalies, such as floods of requests from foreign IPs or unauthorised access to objects.
In addition to detection, Traceable.ai offers a blocking mode at the API edge, stopping attacks like remote code execution (RCE), distributed denial-of-service (DDoS), cross-site scripting (XSS), and parameter anomalies before they reach applications. It also extends protection to Generative AI and LLM-powered APIs, addressing the growing security concerns tied to AI-driven applications. Currently, the platform secures over 500 billion API calls monthly and detects around 50,000 critical vulnerabilities each week [10]. Below, we explore the integrations that enable these capabilities.
Key Integrations
Traceable.ai integrates seamlessly with leading API gateways and proxies such as Apigee, Kong, NGINX, Ambassador, and Istio. For real-time protection, inline agents work directly with gateways like Apigee or NGINX, enabling instant threat analysis and blocking. For agentless security, cloud and edge integrations with AWS WAF, Amazon CloudFront (via Lambda@Edge), and Cloudflare filter potentially harmful traffic at the network edge before it reaches applications.
The platform also employs eBPF technology to monitor workloads and network traffic endpoints, offering deep visibility into API activity without requiring changes to the application code. Additionally, Traceable.ai collaborates with security partners like F5, Wiz, and Tines to automate threat responses and streamline security management.
| Deployment Model | Mechanism | Best Use Case |
|---|---|---|
| Inline Agent | Agent-based (e.g. NGINX, Apigee) | Real-time threat analysis and immediate blocking |
| Out-of-Band | Log-based (gateways/load balancers) | Detection via forwarded traffic logs |
| Edge Deployment | DNS/CDN (e.g. CloudFront, Cloudflare) | Agentless security at the network edge |
Strengths
Traceable.ai excels in identifying all types of APIs, including shadow, zombie, and third-party endpoints, by analysing traffic and gateway integrations. It offers both shift-left testing and runtime protection.
For example, in a case study with Jobvite, Traceable secured over 50,000 APIs and saved more than 1,000 engineering hours. Meanwhile, Axos Bank saw a 100% improvement in API visibility and uncovered four times as many vulnerabilities after adopting the platform.
It became a one stop shop for us to review and approve API usage through the dev cycle. Traceable allowed us to quickly identify our API risk in terms of data leakage and auth issues.- Principal Security Architect, Software Industry [10]
The platform’s accolades include winning Best API Security Solution at the SC Awards 2025 and being named a Leader in the GigaOm Radar for API Security. Its machine-learning capabilities enable it to adapt continuously to new threats, a critical advantage in today’s dynamic threat environment.
Weaknesses
The initial deployment requires a learning phase, as the AI needs time to fully model the environment’s behaviour to function at its best. Additionally, while the platform provides broad visibility across enterprises, some findings may lack the detailed context required for developers to address issues quickly, especially when compared to tools focused on shift-left testing.
Pricing Model
Traceable.ai offers a free tier for initial API discovery and risk assessment at no cost (£0). The Discovery Tier is priced at approximately £16,000 annually for up to 250 API endpoints, while the Protection Tier costs around £56,000 per year for handling 50 million API calls per month. For larger organisations, enterprise pricing is tailored to specific needs, factoring in scale, features, and other requirements.
3. Salt Security
Detection Coverage
Salt Security tackles all aspects of the OWASP API Security Top 10, addressing vulnerabilities like broken object level authorisation (BOLA), injection flaws, mass assignment, and unauthorised data exposure [13]. Using patented behavioural analysis, it establishes a baseline for normal API activity and flags anomalies without relying on manual rules or signatures. This method is particularly effective at identifying business logic abuse and low-and-slow
attack patterns, which traditional WAFs often miss.
The platform automatically identifies shadow, zombie, and third-party APIs across environments. It also safeguards AI-driven applications by detecting shadow MCP servers and monitoring AI agents to prevent prompt manipulation and abuse. Additionally, it tracks sensitive data in motion – including PII, PHI, and PCI DSS data – to uncover risks that traditional DSPM tools might fail to detect.
Key Integrations
Salt Security enhances its detection capabilities by integrating smoothly with essential infrastructure components, enabling swift threat mitigation. For example, it works with API gateways like Kong through a dedicated plugin or sidecar collector, using passive traffic mirroring over secure HTTPS to ensure no impact on application performance [16]. While gateways handle enforcement, Salt identifies threats and sends real-time block commands.
The platform also connects with ITSM and defect-tracking tools like Jira to automate vulnerability ticketing. It integrates with SIEM and SOAR platforms to enrich security alerts and trigger automated responses. For development, Salt provides integration options with CI/CD pipelines via APIs or webhooks, allowing teams to assess API schemas and vulnerabilities during the build phase [35,37]. This flexibility makes Salt compatible with both cloud-native and legacy on-premises environments, requiring no agents or code modifications [31,35].
Strengths
Salt Security's agentless deployment means users can gain actionable insights within hours of setup. One review highlighted:
Salt analysed all our APIs within hours, providing immediate, actionable insights[12].
Its ability to monitor multiple API attributes and establish behavioural baselines allows it to detect threats that signature-based tools might miss. Salt also maps the entire API ecosystem, covering internal, external, shadow, and zombie APIs, ensuring complete visibility. A fintech CISO shared:
Salt stopped an attack that would've cost us millions. Our WAF never even saw it[14].
Salt Labs, the company's research arm, frequently uncovers real-world API vulnerabilities, such as account takeover flaws in travel services and sensitive data leaks on web platforms. Feedback on Gartner Peer Insights describes the platform as easy to use and intuitive
with powerful detection for the OWASP API Top 10
[12].
Weaknesses
Salt Security relies on cloud-scale big data and analytics to function effectively. This means stand-alone on-premises deployments may face challenges in gathering enough data to build accurate behavioural baselines [15]. Additionally, while the platform excels at threat detection, it often depends on existing enforcement tools like API gateways or WAFs for real-time blocking. This approach requires reliable gateway enforcement and a brief learning period to establish baselines.
Pricing Model
Salt Security provides a free API attack surface assessment [13] and a Try Salt for free
option for initial evaluations [12]. For full-scale deployments, pricing is customised based on factors like API volume, endpoint count, and required features. Since specific pricing tiers aren’t publicly available, organisations need to engage directly with Salt Security's sales team to receive a tailored quote. This flexible pricing model accommodates diverse enterprise needs while ensuring scalability.
4. Akamai API Security
Detection Coverage
Akamai API Security provides extensive threat detection capabilities, addressing the entire OWASP API Security Top 10. This includes vulnerabilities like broken authentication, authorisation issues, and configuration errors. It also stands out by focusing on threats related to GenAI models, large language models (LLMs), and Model Context Protocol (MCP) servers [18]. The platform identifies risks such as business logic abuse, unauthorised data access, account takeovers, data scraping, and application-layer denial of service attacks. Its machine learning-powered attacker confidence engine
analyses API behaviour and network patterns to separate legitimate users from potential attackers. Notably, only 27% of organisations with a complete API inventory are aware of which APIs expose sensitive data [17]. Akamai’s detection system integrates effortlessly with current infrastructures, enhancing its utility.
Key Integrations
Akamai API Security integrates with tools like web application firewalls (WAFs), security information and event management (SIEM) systems, and IT service management (ITSM) platforms such as Jira. These integrations enable automated remediation workflows. A native connector allows traffic mirroring directly from the Akamai CDN without introducing latency. The platform supports deployment across SaaS, hybrid, and on-premises environments. Furthermore, Akamai conducts over 200 automated tests simulating malicious traffic during development to detect vulnerabilities before production. For instance, Commerzbank uses Akamai to secure 6 billion monthly API calls with proactive threat detection, while Novant Health relies on the platform to safeguard sensitive patient data and identify potential vulnerabilities during development [18]. These integrations enhance both security and operational efficiency.
Strengths
Akamai is designed to work across varied environments, ensuring compatibility without locking users into a single vendor. Its automated testing suite strengthens security by identifying vulnerabilities before deployment, while continuous discovery maintains an up-to-date API inventory. KuppingerCole has recognised Akamai as a leader in multiple categories, including Product and Market for API security and management. Additionally, Godrej has achieved an impressive near 99.9% uptime by incorporating Akamai’s security solutions [18].
Weaknesses
While Akamai excels in behavioural analysis and threat detection, real-time in-line blocking requires integration with its App & API Protector. This reliance sets it apart from competitors that offer full in-line blocking as a standalone feature. Additionally, the platform’s interface can be challenging to navigate, requiring significant configuration to extract actionable insights [19].
Pricing Model
Akamai does not disclose standard pricing for its API Security solution. Instead, it provides tailored quotes based on factors like API traffic volume and the number of endpoints. Positioned as an enterprise-grade solution, its pricing reflects the deployment scale. For organisations with limited security resources, a Managed Security Service add-on offers 24/7 monitoring and expert support [11].
Need help optimizing your cloud costs?
Get expert advice on how to reduce your cloud expenses without sacrificing performance.
5. Noname Security
Detection Coverage
Noname Security takes a thorough approach to threat detection by addressing API security through three key areas: API security posture management, runtime security, and active Software Development Life Cycle (SDLC) testing. The platform automatically identifies and creates an inventory of all APIs, including shadow, orphan, and zombie APIs. Using AI-driven behavioural analysis, it detects attacks, anomalies, and misconfigurations. Unlike solutions that focus solely on traffic monitoring, Noname Security also evaluates application and infrastructure configurations to identify vulnerabilities before they can be exploited. This strategy is particularly important as Gartner forecasts that by 2025, less than half of enterprise APIs will be actively managed due to the rapid growth of APIs [20]. This lack of visibility highlights the pressing need for dependable API detection.
There is a massive gap in the visibility on the API layer from the perspective of consumption and exposure of information through the API. This leads to lack of governance and posture management of APIs.
- Ahmad Al Qadri, Chief Executive Officer, Evanssion [20]
Key Integrations
Noname Security enhances its detection capabilities by integrating smoothly with existing remediation tools and security frameworks, simplifying incident response workflows. It not only monitors API traffic but also evaluates infrastructure configurations, offering full lifecycle visibility. By embedding into the SDLC, it actively tests and validates APIs before deployment. Additionally, its collaboration with Akamai's edge and CDN infrastructure bolsters its threat response capabilities. The platform also supports runtime visibility through compatibility with API gateways like Gravitee [21][22].
Strengths
Noname Security stands out for its ability to map large API inventories, uncovering shadow and zombie APIs that other tools might miss. Its robust governance features and compliance reporting make it well-suited for enterprises handling extensive API ecosystems. The platform's focus on traffic analysis and pre-deployment validation minimises the risk of vulnerabilities entering production. Furthermore, it has built strong partnerships in regions like the Middle East and Africa, particularly within industries like finance and aviation, where API governance is a critical priority [20][22].
Weaknesses
One of the platform's main drawbacks is its exclusive focus on the API layer. It does not correlate API events with container activity or Kubernetes control plane operations, creating potential blind spots in cloud-native environments. Additionally, it lacks visibility into post-API call processes, such as code execution or call stack analysis, which limits its ability to provide full-stack threat correlation. For smaller security teams, the platform's complexity and extensive features may pose operational challenges. Integration issues with Akamai could also impact the development of future capabilities [22].
Pricing Model
Noname Security’s pricing reflects its enterprise-level focus, with costs tailored to deployment size and API volume. While exact pricing details are not publicly available, its broad feature set and advanced capabilities suggest it is aimed at organisations managing large API estates. Smaller teams with fewer resources may find the platform less suitable for their needs [22].
APIs SOS: A Tactical Guide to Detection and Response
Advantages and Disadvantages
Here's an overview of the key strengths and limitations of the five leading API gateway threat detection tools discussed earlier.
When it comes to scalability and threat intelligence, the platforms differ significantly. For instance, Traceable.ai secures over 500 billion API calls monthly and identifies approximately 50,000 critical vulnerabilities every week [10]. Salt Security's agentless deployment offers quick insights, with one user stating, Salt analysed all our APIs within hours, providing immediate, actionable insights
[12]. Akamai, leveraging its global CDN infrastructure, delivers low-latency protection, with Commerzbank using it to secure 6 billion API calls each month [18].
The detection capabilities also stand out in different ways. Levo.ai focuses on risks unique to AI, such as prompt injection and LLM drift, making it ideal for organisations working with AI agents or vector databases [4]. Traceable.ai uses machine learning and behavioural analytics to detect anomalies in real-time, while Salt Security's patented behavioural analysis excels at identifying business logic abuse and low-and-slow
attacks that traditional WAFs often miss [13]. Noname Security offers a broad approach, covering API security posture management, runtime security, and active SDLC testing. It automatically identifies shadow, orphan, and zombie APIs, ensuring comprehensive oversight.
Pricing models vary widely across these tools. Traceable.ai provides a free tier for initial API discovery, with its Discovery Tier priced at around £16,000 annually for up to 250 endpoints, and its Protection Tier costing approximately £56,000 per year for 50 million monthly API calls. Salt Security offers a free API attack surface assessment [13], while both Levo.ai and Akamai require direct consultations for tailored enterprise quotes [3][5][11]. Noname Security's pricing is customised based on deployment size and API volume, reflecting its enterprise-level focus.
Deployment considerations reveal further trade-offs. Levo.ai uses eBPF-based monitoring for full visibility without performance overhead, with its local Satellite handling traffic analysis within the customer's environment to avoid egress fees [3]. However, this setup requires installing a Satellite and eBPF sensor, which might be challenging for teams with limited DevOps expertise. Traceable.ai provides flexible deployment options, including inline agents, out-of-band monitoring, and edge deployment via DNS/CDN, though its AI requires a learning phase to fully understand the environment's behaviour. Akamai's native CDN connector offers traffic mirroring without latency, but real-time blocking requires integration with its App & API Protector.
Conclusion
Our analysis of the top five API gateway threat detection tools highlights how each caters to unique organisational needs, providing a range of features to address evolving security challenges. Levo.ai specialises in safeguarding AI systems against risks like prompt injection and LLM drift, while its eBPF-based monitoring reduces costs by analysing traffic locally [3][4]. Traceable.ai processes over 500 billion API calls monthly and uncovers around 50,000 critical vulnerabilities each week, with flexibility in deployment through inline agents and edge protection [10]. Salt Security takes a behavioural approach, detecting business logic abuse and subtle low-and-slow
attacks that traditional WAFs often miss, delivering actionable insights within hours [12][13]. Akamai API Security utilises its global CDN infrastructure to provide low-latency protection, handling 6 billion API calls monthly for clients like Commerzbank, though real-time blocking requires pairing with its App & API Protector [18]. Lastly, Noname Security offers full lifecycle API security, including posture management, runtime protection, and active SDLC testing, while automatically identifying shadow, orphan, and zombie APIs [20].
Choosing the right tool depends on your organisation's needs and technical capabilities. Teams focused on DevOps may prioritise solutions with CI/CD pipeline integration for early-stage security checks, while compliance-focused environments should emphasise features like shadow API discovery and adherence to the OWASP API Security Top 10. Key functionalities such as geofencing for GDPR compliance, automated secrets management, and schema validation to block malformed requests are critical for meeting regulatory demands [23][2][1]. Additionally, integration with SIEM systems facilitates audit trails essential for compliance [23][24]. With API attacks potentially costing businesses an estimated £145 billion annually [24], selecting the right tool from these five options can play a pivotal role in strengthening your API security framework and mitigating future threats.
FAQs
What should organisations look for when selecting an API security tool?
When choosing an API security tool, organisations need to focus on features that provide strong protection while integrating smoothly into their existing systems. Look for tools with real-time threat detection features like anomaly detection and behavioural analysis. These capabilities can help spot and address suspicious activity before it causes harm. It's also important to ensure the tool offers thorough support for API discovery, security testing, and runtime protection to safeguard both internal and external APIs effectively.
Compatibility with your current systems and the ability to integrate easily into CI/CD pipelines is another critical factor. Tools that support widely used standards such as OAuth and OpenID Connect are essential for secure authentication and managing access control. Beyond functionality, consider the tool’s ability to scale with your organisation’s growth, its pricing structure, and the quality of vendor support. These aspects ensure the solution can meet your organisation’s changing needs while providing dependable help when required.
The right API security tool should strike a balance between advanced threat detection, extensive API protection, and seamless integration, enabling your organisation to stay ahead of potential risks and maintain a secure API environment.
What is prompt injection, and how does it affect API security?
Prompt injection is an AI-targeted threat where attackers tamper with input prompts to make APIs or AI models act in unexpected or harmful ways. This could result in leaking sensitive information, performing unauthorised actions, or undermining the system's security.
To counter these risks, implementing strong threat detection tools and customised security protocols is crucial. These measures work to spot harmful inputs and safeguard APIs from the ever-changing landscape of AI-related vulnerabilities.
Why is real-time threat blocking essential for API security, and what tools provide this feature?
Real-time threat blocking plays a key role in API security. It enables the instant detection and prevention of malicious activities, helping to protect sensitive data, maintain system integrity, and reduce the chances of downtime or security breaches.
The best API gateway tools come equipped with features like automatic threat detection, endpoint validation, and rapid mitigation. These functionalities are essential for keeping your APIs secure and dependable in the fast-moving digital world we operate in today.
