SOX compliance in hybrid cloud environments requires strong encryption to protect financial data. This includes securing data at rest, in transit, and in use, while addressing challenges like key management and fragmented audit trails. Hybrid clouds, used by 70% of organisations, complicate compliance due to data spread across on-premises systems, private and public clouds.
Key points:
- Encryption requirements: Use AES-256 for data at rest, TLS 1.2+ for data in transit, and SHA-2 for integrity checks.
- Challenges: Managing encryption keys across platforms, ensuring consistent audit trails, and maintaining performance standards.
- Solutions: Centralised key management systems (e.g., Azure Key Vault, AWS KMS), automated key rotation, and confidential computing for data in use.
- Best practices: Double encryption for sensitive data, role-based access control, and real-time monitoring for compliance.
Organisations must implement robust encryption strategies to meet SOX standards while navigating the complexities of hybrid cloud setups. Failure to comply risks data breaches and legal penalties.
SOX Compliance and Encryption Requirements
Financial Data Protection Under SOX
SOX regulations place a strong emphasis on ensuring the accuracy of financial data, holding corporate leaders directly responsible. For instance, Section 302 requires CEOs and CFOs to personally certify the accuracy of financial reports. This means companies must implement robust IT controls - such as encryption - to protect the integrity of their data [7][8].
Similarly, Section 404 obliges management to establish internal controls that safeguard financial data. Encryption plays a key role here by making sensitive data inaccessible to unauthorised users. Additionally, hashing techniques are used to detect any tampering. As Thales highlights:
Any financial information needs to be safeguarded, and its integrity assured[7].
This framework underscores the importance of encryption in meeting SOX's strict requirements for data protection.
SOX Encryption Mandates
While SOX does not explicitly list encryption standards, its focus on data integrity, confidentiality, and audit readiness makes encryption a critical element of compliance. Industry practices generally recommend AES-256 for securing data at rest and TLS 1.2 or higher for data in transit [2]. For instance, Microsoft Azure enforces TLS 1.2 on all public HTTPS endpoints by default to meet such regulatory requirements [2].
SOX also requires tamper-proof audit logs to support real-time and accurate reporting, as outlined in Section 409. These logs must be immutable and traceable, ensuring they cannot be altered. Encryption and digital signatures are often used to protect these logs, preserving their integrity. IT systems must document every change, including details such as the individual responsible and the timestamp. This is especially crucial in hybrid environments where data moves across multiple platforms, ensuring auditors have reliable evidence to verify compliance.
Need help optimizing your cloud costs?
Get expert advice on how to reduce your cloud expenses without sacrificing performance.
Challenges of SOX Encryption in Hybrid Cloud Environments
Data Distribution Across Hybrid Clouds
When financial data is spread across on-premises systems, private clouds, and public cloud platforms, ensuring consistent encryption becomes a daunting task. This broad distribution amplifies the difficulties of managing encryption keys and maintaining comprehensive audit trails. Each environment may rely on different encryption standards, potentially leaving gaps in protection - something auditors are quick to notice. Adding to this complexity, SOX-regulated data must comply with the laws of the country where it is stored[4][6]. If cloud services replicate data across borders without strict controls, organisations risk breaching data residency requirements and may lose track of where their financial records are located.
These issues are further complicated by the intricate process of managing encryption keys across diverse systems.
Key Management Complexity
Handling encryption keys in hybrid cloud setups often leads to what experts call key sprawl.
Fortanix highlights this problem:
Multiple proprietary KMS solutions cause key sprawl. It is complex to track where all keys are, what they are used for, who accessed them, when, and from where[10].
With 81% of organisations adopting hybrid and multicloud strategies[10], this is a widespread concern. Many cloud providers offer their own proprietary Key Management Systems (KMS), forcing businesses to juggle multiple systems. While the Bring Your Own Key
(BYOK) approach is designed to give organisations more control, it involves uploading keys to the provider's infrastructure - essentially granting them access. This arrangement can conflict with SOX requirements, which demand sole ownership and confidentiality of financial data. Such challenges put compliance with SOX standards for data integrity and auditability at risk.
The complexity doesn’t end with key management; maintaining unified audit trails also poses a significant challenge.
Fragmented Audit Trails and Access Controls
In hybrid environments, audit logs are often scattered across multiple systems, making it difficult to consolidate the data necessary for SOX compliance[1]. As employees access financial data from on-premises systems, private clouds, and public clouds, establishing unified identity and access management becomes increasingly difficult[1]. Inconsistent access controls heighten the risk of unauthorised access. Research suggests that centralised encryption key management can greatly reduce the likelihood of data exposure[9], but fragmentation in hybrid setups creates visibility gaps that delay anomaly detection.
Additionally, encryption processes can introduce performance issues. Processor-heavy algorithms may slow down systems, further complicating compliance efforts[2]. Together, these challenges undermine the audit readiness and control standards required under SOX.
Simplifying SOX Compliance in DevOps
Best Practices and Technologies for SOX-Compliant Encryption
::: @figure 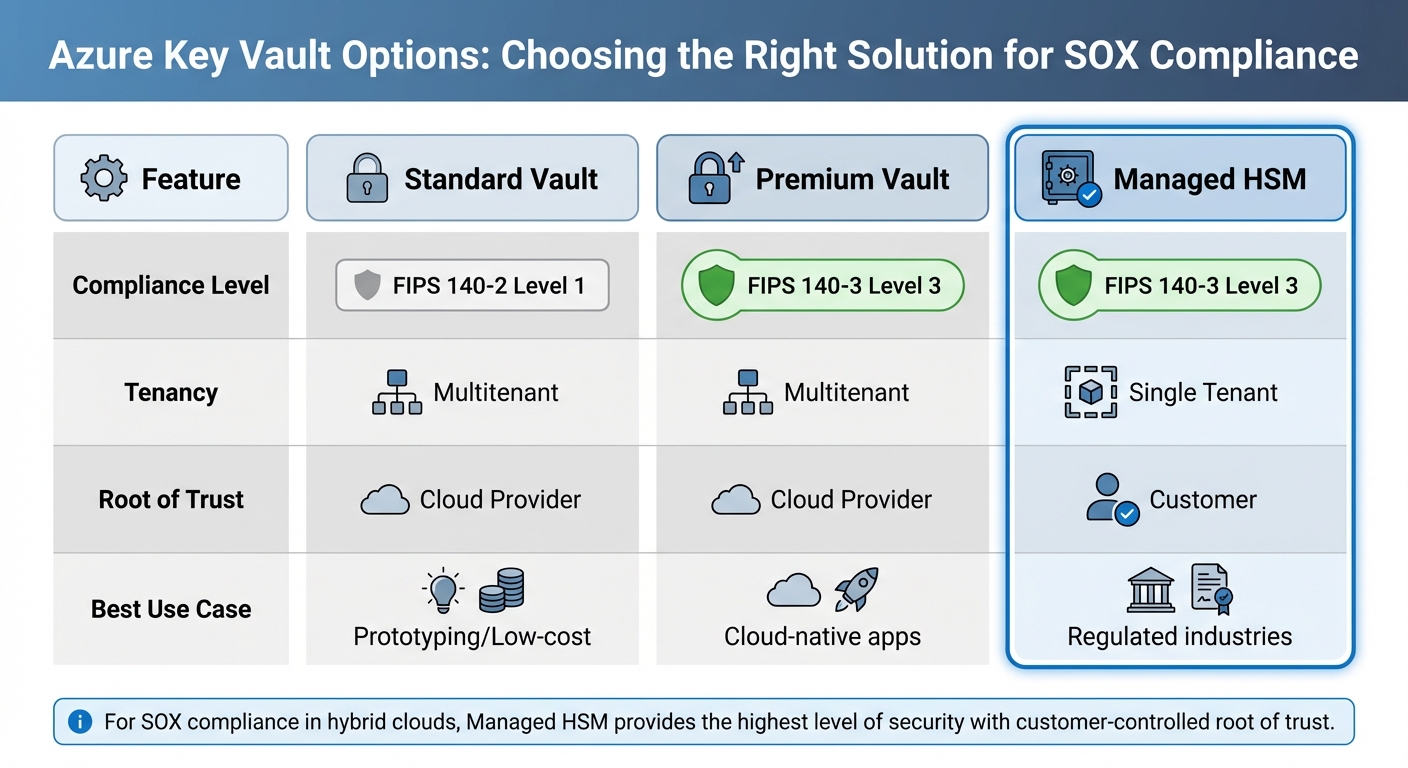 {Azure Key Vault Options Comparison for SOX Compliance}
:::
{Azure Key Vault Options Comparison for SOX Compliance}
:::
Encryption Standards for SOX Compliance
To meet SOX compliance, it's crucial to use AES-256 for data at rest and TLS 1.2+, preferably TLS 1.3, for data in transit. For hybrid connectivity, consider IPsec for VPNs and MACsec (IEEE 802.1AE) for dedicated links. Interestingly, MACsec is often pre-enabled for traffic within or between cloud regions, as noted by Microsoft[2][13][14][15].
For verifying data integrity and detecting tampering, rely on SHA-2 family hashing algorithms like SHA-256, SHA-384, or SHA-512[2]. When it comes to key storage, use HSMs validated to FIPS 140-2/140-3 standards. For example, Azure Key Vault Standard meets FIPS 140-2 Level 1, while its Managed HSMs achieve FIPS 140-3 Level 3, offering top-tier hardware protection[15].
Secure TLS connections typically use RSA-based 2,048-bit key lengths or ECC 256-bit key lengths, ensuring strong encryption protocols that support seamless key management across hybrid environments[14].
Centralised Key Management Solutions
Managing encryption effectively in hybrid environments requires a centralised key management system. Tools like Azure Key Vault or AWS KMS allow organisations to oversee keys, secrets, and policies from one location, ensuring consistent security practices[16]. As Microsoft highlights:
Secure key management is essential to protect data in the cloud[15].
Centralised systems also enable detailed logging and monitoring, which are critical for SOX audit trails[5][15]. They enforce separation of duties, ensuring that individuals managing encryption keys cannot access the encrypted data itself[5].
For organisations looking to integrate on-premises and cloud encryption, Bring Your Own Key (BYOK) functionality allows the import of existing HSM keys[15][17]. This approach addresses concerns about key sovereignty, as Microsoft explains:
Key sovereignty means that a customer's organisation has full and exclusive control over who can access keys and change key management policies[18].
Here's a quick comparison of key management options:
| Feature | Standard Vault | Premium Vault | Managed HSM |
|---|---|---|---|
| Compliance Level | FIPS 140-2 Level 1 | FIPS 140-3 Level 3 | FIPS 140-3 Level 3 |
| Tenancy | Multitenant | Multitenant | Single Tenant |
| Root of Trust | Cloud Provider | Cloud Provider | Customer |
| Best Use Case | Prototyping/Low-cost | Cloud-native apps | Regulated industries |
Automated lifecycle management is another key feature, streamlining the provisioning, rotation, and renewal of keys and certificates. This ensures compliance is maintained without manual intervention[2][3]. As AWS notes:
The cybersecurity industry constantly evolves to meet the ever-changing threat landscape. As such, your standards should change to adopt the latest technologies[12].
By centralising key management, organisations can maintain a consistent and audit-ready encryption strategy across hybrid environments.
Implementing Encryption Across Hybrid Clouds
Effective encryption in hybrid cloud environments starts with data discovery and classification. Tools like Microsoft Purview can help identify and catalogue sensitive financial data across Azure, on-premises systems, and other cloud platforms, ensuring all SOX-relevant data is accounted for[5].
For highly sensitive data, organisations should enforce double encryption - applying independent layers of encryption at both the infrastructure and application levels, using separate keys[2][5].
To optimise performance, aim for a network round-trip time of 35 milliseconds or less between the cloud service and an external key manager[11]. Implement Role-Based Access Control (RBAC) to tightly manage key access, ensuring even platform administrators need explicit authorisation to access encryption keys[2][15]. Additionally, enabling soft delete and purge protection safeguards critical encryption keys against accidental or malicious deletion[5].
For organisations with the most stringent requirements, confidential computing offers an extra layer of protection. It encrypts data in use
by securing financial information during processing in memory, using hardware-isolated enclaves[2][6]. This approach ensures sensitive data remains protected at all times, even during computation.
Case Studies and Research Findings
Case Study: Veeam's SOX-Compliant Hybrid Cloud Solution
Veeam has developed an encryption architecture tailored for hybrid cloud environments, featuring robust 256-bit AES encryption and a three-tier key hierarchy. This setup is specifically designed to align with SOX compliance requirements[20].
To further support compliance, Veeam ONE offers real-time monitoring and customisable reports, ensuring organisations can retain data for the mandated five years. According to Product Marketing Manager Kelsey Teske, the platform enables businesses to distinguish between protected and unprotected data while verifying adherence to retention policies - all from a single, user-friendly interface[19].
These practical solutions highlight the potential for further exploration into unified key management strategies, which are discussed in the following section.
Research Findings: Unified Key Management Outcomes
Studies on unified key management platforms, such as Fortanix DSM, underscore their effectiveness in addressing SOX compliance challenges within hybrid cloud setups. With 81% of organisations adopting hybrid strategies, fragmented audit trails often emerge as a major issue. Platforms like Fortanix DSM, which holds a 4.6/5 rating, simplify key lifecycle management across varied environments[10].
Aroop Menon from Fortanix points out the security benefits of using external key management systems:
The best security available for cloud encryption comes from using Bring Your Own KMS (BYOKMS), also called External Key Management (EKM)[21].
This method ensures encryption keys remain separate from the data, preventing cloud providers from accessing sensitive financial information. Such separation is a critical factor for meeting SOX auditing standards[10][21].
Hokstad Consulting: Hybrid Cloud Encryption Services

Customised SOX Encryption Solutions
Hokstad Consulting takes a practical, forward-thinking approach to SOX encryption in hybrid cloud environments. By embedding security frameworks directly into DevOps workflows, they ensure SOX-compliant encryption becomes a seamless part of the infrastructure. Instead of relying on traditional manual audits, they leverage Infrastructure as Code (IaC) to enforce encryption policies consistently across hybrid and multi-cloud setups. This ensures that security measures automatically scale alongside infrastructure growth, avoiding the common pitfalls of static documentation and fragmented audit trails.
Their automated CI/CD pipelines are equipped with compliance checks to minimise human error during key deployment. Additionally, real-time monitoring solutions provide continuous oversight of encryption health, enabling quick detection and resolution of compliance issues. This proactive approach stands in stark contrast to outdated methods that depend on periodic manual reviews.
| Feature | Hokstad Consulting Approach | Traditional Compliance Approach |
|---|---|---|
| Implementation | Integrated into DevOps/CI/CD | Manual tick-boxexercises |
| Policy Enforcement | Managed via Infrastructure as Code (IaC) | Static documentation and manual checks |
| Monitoring | Real-time automated alerts | Periodic manual audits |
| Cost Impact | Cuts cloud expenses by 30–50% | Often increases operational costs |
| Scalability | Fully automated and cloud-agnostic | Limited by manual resources |
Compliance and Key Management Support
Hokstad Consulting also addresses key management complexities through flexible retainer models. These models provide on-demand DevOps support, allowing encryption strategies to adapt to evolving regulatory and operational needs. Their expertise often reveals ways to streamline encryption setups, achieving cost savings of 30–50% on cloud infrastructure.
Their cloud migration services go a step further, offering multi-layered backup solutions and creating cloud-agnostic microservices. This prevents vendor lock-in while maintaining SOX compliance across various hosting configurations. Such adaptability is particularly beneficial for organisations handling sensitive financial data across public, private, and hybrid clouds.
Conclusion
Achieving SOX compliance in hybrid cloud environments hinges on implementing strong encryption practices to safeguard financial data in all its forms: at rest, in transit, and in use. Encryption does more than just shield information - it acts as a critical sovereignty control
, ensuring that even if providers access the data, it remains unreadable [4]. This becomes especially important when financial data is spread across on-premises systems, private clouds, and public cloud platforms.
The challenges, however, are not minor. Managing encryption keys and maintaining clear audit trails can be daunting. The statistics underline the urgency: 98% of businesses have faced cloud-data breaches in the past 18 months, yet only 13% fully grasp their cloud-security responsibilities. Shockingly, just 20–40% of cloud data is encrypted, leaving sensitive financial details vulnerable.
To counter these risks, organisations are adopting proven strategies. Centralised key management, automated key rotation integrated into CI/CD pipelines, and hardware-backed security via HSMs are paving the way for scalable compliance. Meanwhile, confidential computing technologies now allow data to remain protected even during active processing [2][3].
For firms in the UK, SOX-compliant encryption must also align with UK GDPR and the Data Protection Act 2018. Non-compliance here can lead to severe penalties, including fines of up to £17.5 million or 4% of global annual turnover. A unified approach to encryption, addressing both SOX and UK data protection laws, is therefore crucial. Hokstad Consulting tackles this challenge by embedding security measures directly into DevOps workflows. Their No Savings, No Fee
model has helped clients not only achieve compliance but also cut costs by 30–50%.
FAQs
What encryption standards are essential for ensuring SOX compliance in hybrid cloud environments?
To meet SOX compliance in hybrid cloud environments, it's essential to use robust encryption protocols for protecting data both at rest and in transit. A common approach is employing industry-standard methods like AES (Advanced Encryption Standard) with a 256-bit key, which provides a high level of security for sensitive financial information.
Equally important is ensuring that encryption practices adhere to regulatory guidelines. This includes implementing secure key management strategies and conducting regular audits of encryption processes. These steps play a crucial role in maintaining data integrity and preventing unauthorised access, both of which are fundamental to SOX compliance.
How can organisations securely manage encryption keys in hybrid cloud environments?
To manage encryption keys securely in hybrid cloud environments, organisations should consider using a centralised key management system (KMS). This approach simplifies oversight, ensures uniformity, and automates key processes like rotation and access control. By doing so, it minimises the risk of mistakes and unauthorised access. Adding hardware security modules (HSMs) to the mix can further strengthen protection by safeguarding keys from theft or tampering.
For compliance with regulations like the UK’s GDPR, organisations should adopt policy-driven frameworks. These frameworks ensure strict documentation, maintain detailed audit trails, and enforce access controls. Depending on organisational requirements, models such as Bring Your Own Key (BYOK) or Hold Your Own Key (HYOK) can offer enhanced control over encryption keys.
In multi-cloud environments, using solutions that unify key management across providers can help avoid key sprawl and maintain consistent security measures. By prioritising automation, centralised management, and well-defined policies, organisations can protect their encryption keys effectively in hybrid cloud setups.
What are the key challenges in achieving SOX compliance within hybrid cloud environments?
Maintaining SOX compliance in hybrid cloud setups is no small feat. The mix of on-premises and cloud systems introduces layers of complexity, especially when it comes to aligning security standards across both environments. It’s crucial to safeguard the confidentiality, integrity, and availability of data, particularly as it transitions between these interconnected systems.
One major hurdle is addressing vulnerabilities at integration points, which can create weak spots in your security framework. Another is establishing consistent monitoring and control measures that work seamlessly across varied infrastructures. On top of that, organisations face the added pressure of keeping up with ever-changing compliance requirements - all while ensuring their systems remain secure and adaptable to growth.
