Protecting patient data in hybrid cloud setups requires encryption as a key security measure under HIPAA. While not strictly mandatory, encryption is often necessary to secure electronic Protected Health Information (ePHI) during storage and transfer. Hybrid cloud environments combine on-premises systems with cloud services, offering flexibility but increasing complexity. This article breaks down how encryption supports HIPAA compliance, the challenges of implementation, and the best practices to secure sensitive healthcare data.
Key Takeaways:
- Encryption under HIPAA: Not mandatory but strongly recommended, especially in hybrid cloud setups.
- Hybrid Cloud Benefits: Combines scalability of public cloud with control of on-premises systems.
- Challenges: Inconsistent encryption practices, key management issues, and risks during data transfers.
- Best Practices: Use AES-256 for data at rest, TLS 1.2+ for data in transit, centralised key management, and automated compliance checks.
Hybrid clouds require careful planning to ensure encryption is consistent and meets HIPAA standards. This includes addressing fragmented systems, automating key rotation, and securing data transfers. Organisations must also establish clear responsibilities with cloud providers to avoid compliance risks. By following these steps, healthcare entities can protect patient data while leveraging the benefits of hybrid cloud technology.
Hybrid-Cloud, HIPAA Compliant Enterprise with Kubernetes - Steve Sloka, Heptio
Challenges of Implementing HIPAA Encryption in Hybrid Cloud Setups
Hybrid cloud architectures bring plenty of benefits, but ensuring HIPAA-compliant encryption across these mixed environments is no easy task. Organisations face fragmented systems, tricky key management, and heightened risks of breaches - all of which make compliance a daunting challenge.
Inconsistent Encryption Across On-Premises and Cloud Systems
Every cloud provider has its own set of security interfaces, logging formats, and encryption settings. This lack of standardisation makes it tough to maintain consistent encryption practices across on-premises and cloud systems [7][10]. The result? Blind spots in security. When monitoring tools can’t keep up, threats take longer to detect, and piecing together security intelligence becomes a headache [8].
The financial impact is staggering. Breaches in hybrid cloud setups cost organisations an average of £4.75 million per incident - far more than breaches in purely public or private cloud environments [8]. And here’s the kicker: misconfigurations are behind over 60% of cloud-related data breaches [8].
As Netenrich aptly puts it:
The challenge isn't a shortage of technology; it's the lack of integration between them [8].
Adding to the complexity, HIPAA regulations from 1996 weren’t designed with modern tech like Kubernetes or dynamic cloud workloads in mind [10]. This leaves IT leaders trying to reconcile outdated legal frameworks with today’s fast-evolving infrastructure. With around 80% of organisations now running a mix of public, private, and on-premises systems [8], maintaining consistent encryption has become a monumental task.
Key Management and Security Concerns
Encryption key management is a cornerstone of HIPAA compliance, but it’s also a major vulnerability in hybrid environments. If a single key is compromised, the entire encryption system can be rendered useless, exposing sensitive electronic Protected Health Information (ePHI) to unauthorised access [1]. Without strategies like key segmentation or envelope encryption, a compromised Data Encryption Key (DEK) can leave vast amounts of data unprotected [11].
One common misstep is storing encryption keys alongside the data they’re supposed to protect. This practice makes it easier for attackers to decrypt data during a breach [3]. Another issue arises when the same administrators manage both storage infrastructure and encryption keys, violating the principle of separation of duties. This creates a single point of failure, as Kevin Henry explains:
Administrators who manage storage should not control keys; enforce dual control for key exports [3].
Manual key rotation processes only add to the risk, while inconsistent tools across hybrid setups lead to security gaps and configuration drift, leaving ePHI vulnerable [11].
Compliance Risks During Data Transfers
Transferring ePHI between on-premises systems and cloud platforms is another compliance minefield. Public cloud control planes often log credentials and metadata offsite, which can compromise the chain of custody required by HIPAA [5]. The statistics are alarming: in 2023, the healthcare sector saw a record 725 breaches, exposing 133 million records - many of which occurred during data transfers [9].
Legacy protocols, weak encryption ciphers prone to downgrade attacks, and unmanaged service hops in SaaS pipelines create untraceable vulnerabilities [3][5]. For instance, a regional hospital suffered a breach because a legacy file share wasn’t encrypted at rest, and a contractor’s VPN lacked multi-factor authentication. The attackers were able to exfiltrate thousands of records [3].
The financial penalties for such lapses are severe. OCR fines can reach up to £50,000 per violation [5]. Notably, cloud providers storing encrypted data without access to decryption keys are still considered Business Associates under HIPAA, as the Department of Health and Human Services (HHS) clarifies:
Lacking an encryption key does not exempt a CSP from business associate status and obligations under the HIPAA Rules [2].
These challenges highlight the need for robust, centralised encryption practices - something the next section will explore in detail.
Best Practices for HIPAA-Compliant Encryption in Hybrid Clouds
::: @figure 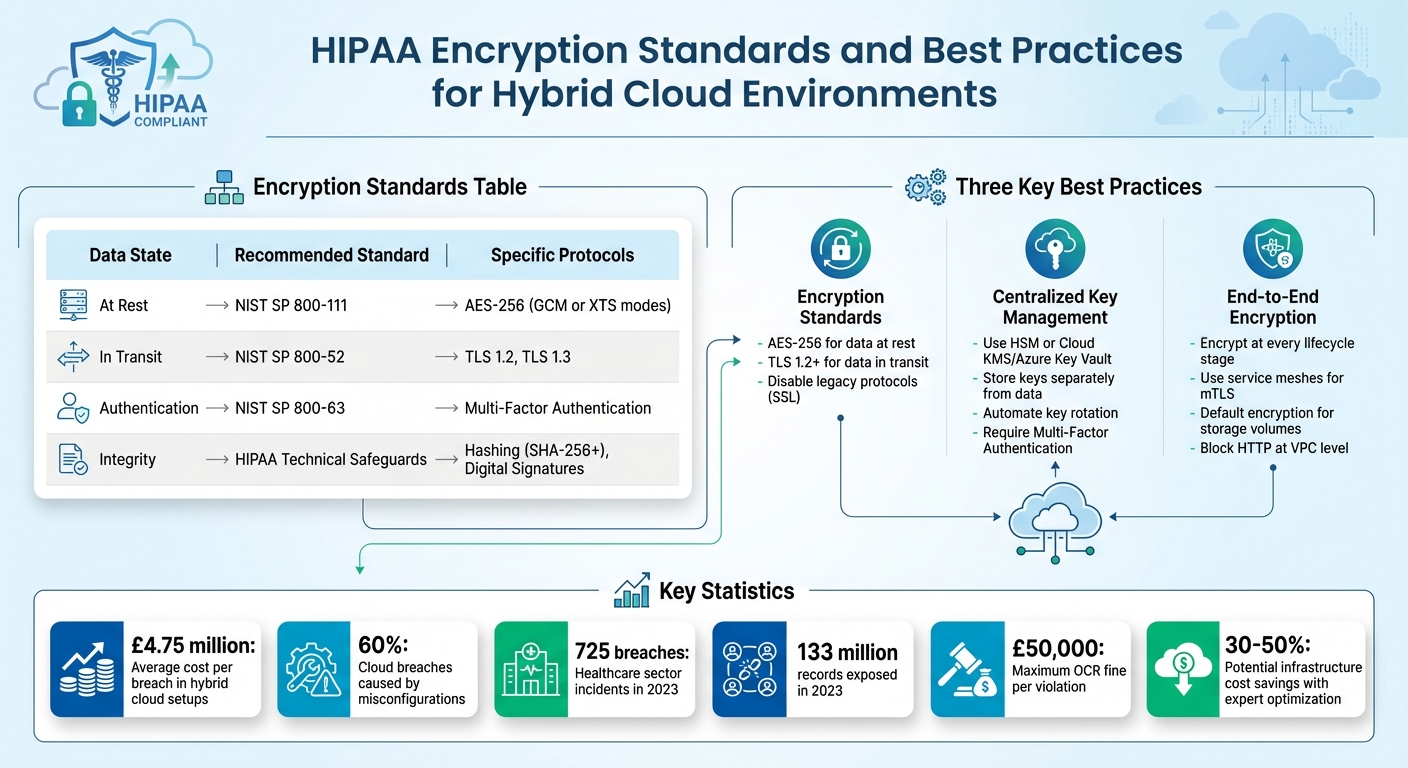 {HIPAA Encryption Standards and Best Practices for Hybrid Cloud Environments}
:::
{HIPAA Encryption Standards and Best Practices for Hybrid Cloud Environments}
:::
Securing sensitive data in hybrid cloud environments requires strong encryption practices. By following proven strategies, organisations can minimise risks and streamline compliance efforts, ensuring both the safe transmission and storage of sensitive information.
Encryption Standards for Data at Rest and In Transit
To meet the 2021 HITECH Act amendment standards and avoid penalties, organisations should adhere to encryption guidelines like NIST SP 800-111 for data at rest and NIST SP 800-52 for data in transit [12]. For stored data, such as discs, databases, and backups, AES-256 encryption is the recommended standard. While AES 128-bit encryption - developed nearly five decades ago - remains acceptable, the 256-bit variant is now the go-to choice for high-security needs [12].
For data in transit, protocols like TLS 1.2 or higher (preferably TLS 1.3) should be used, and older protocols like SSL should be disabled to prevent downgrade attacks [16]. To ensure that electronic Protected Health Information (ePHI) remains unchanged during transmission, integrity controls such as checksums, SHA-256 hashes, or digital signatures are essential [13].
| Data State | Recommended Standard | Specific Protocols |
|---|---|---|
| At Rest | NIST SP 800-111 | AES-256 (GCM or XTS modes) |
| In Transit | NIST SP 800-52 | TLS 1.2, TLS 1.3 |
| Authentication | NIST SP 800-63 | Multi-Factor Authentication |
| Integrity | HIPAA Technical Safeguards | Hashing (SHA-256+), Digital Signatures |
Centralised Key Management Solutions
A key part of encryption is managing the encryption keys themselves. Best practice involves storing encryption keys separately from the data they protect. Solutions like Hardware Security Modules (HSM) or cloud-based services such as Cloud KMS or Azure Key Vault can help centralise key management [16]. This approach reduces the potential damage if a key is compromised. Microsoft Azure highlights this importance:
Protecting a decryption key is important because rotation is a common way to control the blast radius if a key is compromised [6].
Key rotation should be automated, either on a regular schedule or immediately following changes in staff roles. Access to the key management system should require Multi-Factor Authentication (MFA) [13]. Additionally, centralised systems provide detailed audit logs, which can help identify unusual activities and support compliance with HIPAA's audit requirements [2].
End-to-End Encryption Implementation
To ensure comprehensive protection, data should be encrypted at every stage of its lifecycle - from its creation on-premises to its transmission, storage, and processing in the cloud [2]. For microservice-based architectures, service meshes can enforce mutual TLS (mTLS), simplifying TLS negotiation by offloading it from application code [4]. Furthermore, cloud accounts should be configured to encrypt storage volumes by default, preventing the creation of unencrypted data [4].
Blocking insecure protocols like HTTP at the VPC level and using Application Load Balancers to redirect traffic to HTTPS ensures secure communication [4]. Declaring encryption settings within Infrastructure as Code (IaC) templates can further guarantee consistent enforcement across hybrid deployments [4].
As Brian Soby, CTO and Co-founder of AppOmni, points out:
Continuous evaluation has to happen after login, not just at login. The guidance pushes maturity beyond authenticate, then trust, towards ongoing decisions driven by what the user is doing [14][15].
Need help optimizing your cloud costs?
Get expert advice on how to reduce your cloud expenses without sacrificing performance.
Practical Steps to Achieve HIPAA Compliance in Hybrid Environments
Conducting a Risk Assessment
Start by cataloguing all cloud services, workloads, databases, APIs, and integrations that handle electronic Protected Health Information (ePHI). This inventory, updated annually, should map out data flows, including archival processes, while identifying shadow IT and cross-region transfers that might lead to compliance issues [17][18]. Using metadata tagging can help maintain accountability by creating a clear inventory of systems that create, receive, maintain, or transmit ePHI [17].
It's crucial to review the shared responsibility model to understand which security controls are managed by your provider and which are your responsibility [17][18]. Your risk assessment should pinpoint specific threats - like misconfigurations, privilege misuse, insecure APIs, and data exfiltration - and rank these risks based on their likelihood and potential impact [18]. Use these findings to create a prioritised risk register, assigning remediation tasks with clear timelines and responsible owners.
Examine all Business Associate Agreements (BAAs) to confirm that vendors and subprocessors have agreements aligning with your encryption and logging standards [17][18]. Remember, HIPAA documentation, including risk analysis results and risk registers, must be retained for at least six years [18]. Reassessments should be conducted annually or whenever significant architectural changes occur, such as migrating to new regions or onboarding new cloud services [17][18].
These efforts lay the groundwork for automating processes that maintain ongoing compliance.
Automating Encryption with DevOps Tools
Automation can help resolve the inconsistencies and manual errors that often plague encryption processes. Using Infrastructure as Code (IaC) tools like Terraform, Ansible, Chef, and Puppet, teams can pre-configure encryption settings, ensuring compliance from the outset for all servers and storage volumes [20][21]. Automated provisioning and CI/CD compliance checks can enforce encryption at rest (e.g., AES-256) and in transit (e.g., TLS 1.2+) as default standards. Playbooks can also simplify key rotation and certificate renewal tasks [20][21][22].
These tools are particularly useful for detecting configuration drift - where manual changes disable encryption settings - and can automatically correct such issues to maintain compliance [20].
Regular Audits and Monitoring
Automated controls are only part of the equation; regular audits ensure sustained security and compliance. Centralising logs from both on-premises and cloud environments using Security Information and Event Management (SIEM) tools like Microsoft Sentinel can provide a secure way to capture all activity [11][23]. User and Entity Behaviour Analytics (UEBA) can help detect unusual activity, privilege escalations, or data exfiltration, offering continuous monitoring beyond initial login [11][14][15].
Set up automated alerts to flag encryption failures or the detection of non-encrypted endpoints [21]. Perform formal access reviews quarterly, while high-risk roles should undergo monthly checks [11]. These practices align with the overarching goal of maintaining HIPAA-compliant encryption across hybrid environments. Notably, under the 2021 HITECH Act amendment, organisations that demonstrate at least 12 months of compliance with a recognised security framework may avoid penalties from the Office for Civil Rights (OCR) [12].
Working with Experts for HIPAA Encryption in Hybrid Clouds
Customised Solutions for Hybrid Cloud Security
Ensuring HIPAA-compliant encryption in hybrid cloud environments requires a deep understanding of both the regulations and the technical aspects of implementation. Under the shared responsibility model, healthcare organisations must secure their data within the cloud, while cloud providers manage the underlying infrastructure [1].
Hokstad Consulting offers tailored DevOps and cloud migration services to address these challenges. Their approach aligns encryption protocols with NIST standards - specifically SP 800-111 for securing data at rest and SP 800-52 for data in transit [12][19]. By leveraging Infrastructure as Code (IaC), they ensure consistent and version-controlled compliance measures across all environments [24][25].
Experts also handle the complexities of Business Associate Agreements, ensuring that even no-view
services meet HIPAA requirements. As clarified by HHS.gov:
Lacking an encryption key does not exempt a CSP from business associate status and obligations under the HIPAA Rules [2].
The 2021 amendment to the HITECH Act has further incentivised compliance documentation. Steve Alder, Editor-in-Chief of The HIPAA Journal, explains:
The HIPAA encryption requirements have increased in relevance since an amendment to the HITECH Act in 2021 gave HHS' Office for Civil Rights the discretion to refrain from enforcing penalties for HIPAA violations when covered entities and business associates can demonstrate at least twelve months HIPAA compliance [12].
This specialised expertise helps bridge the regulatory and technical challenges that hybrid environments often present.
Continuous Support and Cost Optimisation
HIPAA compliance isn't a one-and-done task - it requires ongoing monitoring and proactive updates [26]. Hokstad Consulting provides continuous support, with their cloud cost engineering services helping organisations cut infrastructure expenses by 30–50%. This is achieved through strategic workload placement and addressing the rising costs and complexities of cloud management [25].
Their support includes 24/7 SIEM-integrated monitoring, which detects anomalies such as unauthorised access or decryption failures in real time [25]. Centralised key management across platforms like AWS, Azure, and Google Cloud ensures compliance with separation of duties requirements. This prevents teams managing storage infrastructure from accessing encryption keys [11][3]. Features like automated key rotation and customer-managed keys (CMKs) give organisations full control over their data's lifecycle and residency [11][6].
Gil Vidals, CEO of HIPAA Vault, highlights the growing importance of multi-cloud strategies:
Multi-cloud adoption in healthcare is a strategic imperative [25].
With 79% of healthcare organisations planning to implement multi-cloud strategies by 2025, the need for specialist support is more critical than ever. Hokstad Consulting’s retainer model offers flexible, ongoing infrastructure management that evolves with changing regulatory requirements and cloud architectures.
Conclusion: Achieving Secure and Compliant Hybrid Cloud Infrastructure
Meeting HIPAA requirements for hybrid cloud encryption involves a shared responsibility. While cloud providers secure the infrastructure, organisations must focus on encrypting and configuring their in-cloud data effectively [1]. The stakes are high: fines for HIPAA violations from the Office for Civil Rights (OCR) can reach up to £38,000 per violation [5]. For breaches affecting 500 or more individuals, organisations are required to notify prominent media outlets and regulatory bodies within 60 calendar days [26].
To ensure robust security, organisations should implement end-to-end encryption. This includes using AES-256 for data at rest and TLS 1.2 or later for data in transit. Centralised key management, through tools like Hardware Security Modules (HSMs) or Key Management Services (KMS), is also essential [6][11]. Employing FIPS-validated cryptographic modules and automating key rotation further reduces the risk of exposure in case of a compromise [11][26]. Additionally, adopting micro-segmentation and a Zero Trust architecture eliminates implicit trust within the hybrid environment [1]. Tools like Infrastructure as Code (IaC) ensure that every new resource is compliant from the outset [4]. Together, these measures provide a solid framework for addressing the challenges of hybrid cloud setups.
Given the intricate nature of hybrid cloud environments, expert guidance becomes crucial. Hokstad Consulting offers a tailored approach, combining DevOps automation with cloud cost engineering, helping organisations achieve 30–50% savings on infrastructure costs without compromising security. Their flexible retainer model and continuous monitoring ensure compliance adapts seamlessly to evolving regulatory standards and cloud technologies.
FAQs
Why isn’t encryption mandatory under HIPAA, and why is it still highly recommended?
Encryption under HIPAA isn't an absolute requirement. It's considered an addressable
safeguard, meaning organisations need to evaluate their specific risks to electronic protected health information (ePHI) and determine whether encryption is a suitable measure for their situation.
That said, encryption is highly advisable. It adds a critical layer of protection to ensure the confidentiality and security of ePHI. By encrypting sensitive data, organisations minimise the chances of unauthorised access - especially crucial in hybrid cloud setups where data moves across various systems. Beyond security, using encryption shows a proactive stance on compliance and helps reduce the likelihood of breaches or penalties.
How can organisations maintain consistent encryption in hybrid cloud environments?
To ensure encryption remains consistent in hybrid cloud environments, organisations should prioritise centralised key management. This approach simplifies the control and oversight of encryption keys across systems. Automating tasks like key retrieval and rotation adds an extra layer of security by reducing the risks associated with manual handling.
Equally important is maintaining uniform encryption standards and policies across all platforms. This alignment helps eliminate compliance gaps and ensures a cohesive security framework. Regular monitoring and auditing of access, using tools designed for your specific infrastructure, can uncover and address potential vulnerabilities before they become serious issues.
By implementing these measures, organisations can protect sensitive data effectively while meeting compliance requirements with confidence.
What are the best practices for securely managing encryption keys in a hybrid cloud environment?
Managing encryption keys securely in a hybrid cloud environment is crucial for safeguarding sensitive data and meeting regulatory requirements. One effective approach is using a centralised key management system (KMS). This ensures consistent key management across public, private, and on-premises systems, reducing potential vulnerabilities.
Automating key processes - like rotation, renewal, and revocation - helps minimise human error while bolstering security. Additionally, encryption keys should be stored securely in hardware security modules (HSMs) rather than being embedded in application code, which can expose them to unnecessary risk.
To further tighten security, enforce least privilege access controls so only authorised personnel can access or use the keys. Regular security audits are also essential to verify compliance with regulations such as GDPR. For organisations looking for greater control, methods like Bring Your Own Key (BYOK) or Hold Your Own Key (HYOK) offer flexibility by allowing ownership and management of encryption keys.
By adopting a structured, automated strategy for encryption key management, organisations can better protect their data and ensure compliance within hybrid cloud environments.
